Position Based Routing Technique: Greedy Perimeter Stateless Routing for Wireless Networks
Full text
Figure
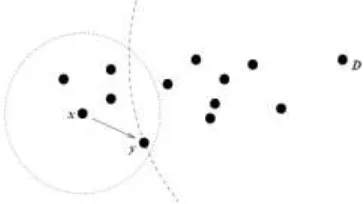

Related documents
In general, series that tended to use more than one name to label or describe their documents were also less consistent in the way the document was structured or the type of content
In der vorliegenden Arbeit wurde gezeigt, daß FKBP51 auf zwei verschiedenen Stufen in die Signaltransduktion von GR und MR eingreift: zum einen durch eine Reduktion der
Existing approaches to phantom protection in B trees (namely, key range locking) cannot be applied to multidimensional data structures since they rely on a total order over the
Preoperative circulating tumor cells detection using the isolation by size of epithelial tumor cell method for patients with lung cancer is a new prognostic biomarker.
Since the objective of the present study was to evaluate Sarva Shiksha Abhiyan (SSA) launched in 2001 in Himachal Pradesh with respect to quality improvement at
preparing the quality teachers who are committed to teaching profession.
Some specific examples of solutions for the resulting equations are given, and a particular application to the case of constant mean curvature surfaces under
(13) was applied to snowmelt samples collected at different elevations (lower than 2800 m a.s.l.) in order to estimate the average isotopic composition of high-elevation snowmelt,