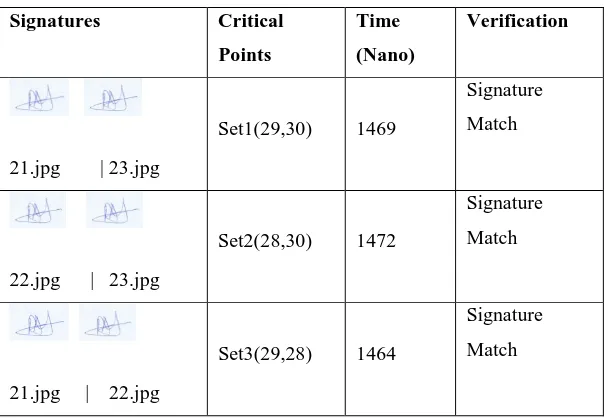
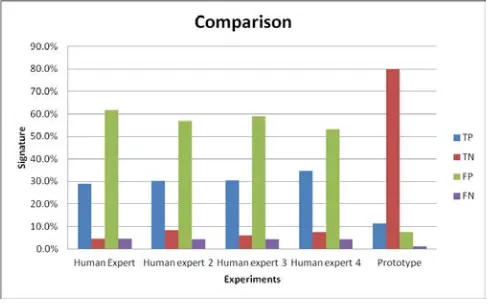
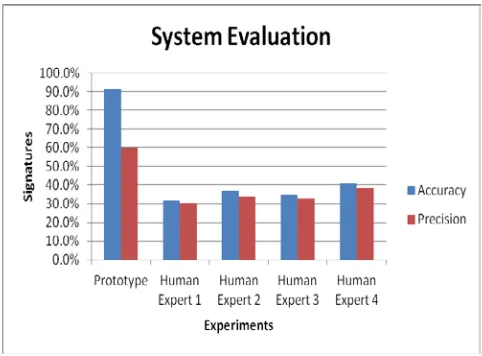
Identity Theft Mitigation in Kenyan Financial Sectors (SACCOs): Handwritten Signature Verification
Full text
Figure



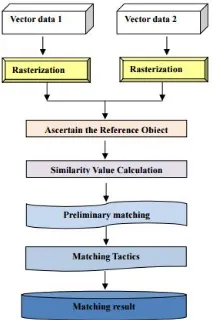
Related documents
The vehicles shall be three to Five (3-5) yrs old from the date of manufacture, whether locally assembled or Second hand “New” import at the time of commencement
• Placing identity theft indicators on taxpayer accounts to track and manage identity theft incidents. • Using business filters to analyze returns filed on identity theft
I am an identity theft victim and a copy of my police report (or other investigative report or complaint to a law enforcement agency concerning identity theft) of identity theft
In addition to names, addresses and telephone numbers that they can easily find, identity thieves are especially looking for other information that they can connect to, such as
In the absence of both learning and comparative advantage, the source of possible bias in conventional cross-section estimates of sectoral log wage differentials is the
The President’s Task Force on Identity Theft and The FTC’s Role in Identity Theft..
ATTACHMENT D RED FLAG IDENTIFICATION AND IDENTITY THEFT PREVENTION PROCEDURES IDENTITY THEFT RED FLAG PREVENTION/MITIGATION PROCEDURE
Thus our data suggest that patients with marked findings of intercanine expansion and/or overjet reduction during orthodontic treatment may be particularly at risk of changes in