1
Challenges in disclosing ransomware attacks on
hospitals
A study about the implementation of disclosure strategies of Dutch
healthcare institutions during and after ransomware attacks in light
of the GDPR
1
Overview
Title: Challenges in disclosing ransomware attacks on hospitals
A study about the implementation of disclosure strategies of Dutch healthcare institutions during and after ransomware attacks in light of the GDPR
Assignment: Master Thesis
Date 09 January 2018
Word Count: 25,322 words (excluding references and appendices) Word Count: 36,835 words (including references and appendices)
Author: N. M. Mok
Student Number 1804480
Program: MSc Crisis and Security Management Faculty: Governance and Global Affairs University: Leiden University, campus The Hague
Supervisor: Dr. E. Tikk
2
Abstract
This study contains a research about disclosure strategies of Dutch hospitals during and after ransomware attacks. The framework of Kulikova, Heil, Berg, & Pieter (2012) is used to describe the different disclosure strategies. In addition to the descriptive function of the framework, it is evaluated on usability to design disclosure strategies. The research objective of this study is expressed in the following question:
“What are the cyber incident information disclosure strategies of Dutch healthcare institutions during and after a ransomware attack and how is this expected to change due to the GDPR?”
The following contributions to the current academic field of research and body of literature are identified:
1. The research provides insight on the cyber security challenges that healthcare institutions face and highlights the importance of incident information disclosure strategies before, during, and after ransomware attacks.
2. The research provides insight on the expected consequences of the GDPR on the Dutch healthcare industry and combines the expected developments of ransomware threats with the current and future digital vulnerabilities of the healthcare sector.
3. The research combines the scattered information and frameworks regarding incident information disclosure from numerous sector based scientific papers and provides insight in the overlap in identified gaps regarding this topic.
4. One of the main identified gaps regarding incident information disclosure identified in academic literature is the lack of evaluation of the proposed frameworks. This research used and validated one framework on the usability to design incident information disclosure strategies and proposed two additions to improve its usefulness.
Keywords
3
Foreword
Before you lies my thesis for obtaining the Master’s degree in Crisis and Security Management. The thesis summarizes many different thoughts, interests, and research directions that have passed my mind for the last half year. I found this topic highly interesting and – mostly to my own surprise – I enjoyed every step of the process that has resulted in this thesis.
I would like to thank Eneken Tikk for all her guidance, work, and advice throughout my process. I am confident to say that without her as my supervisor I would not have enjoyed this process half as much as I have. She did not only question the content of my thesis and my line of arguments - which definitely needed some questioning – but also questioned my role as researcher, my future plans, and the strengths and weaknesses of my technical background. She understood my struggles with the academic field an helped me overcome most of it. I am proud of the work I have done and grateful for the help she provided me to make it a piece and process to be proud of.
Second, I would like to express my gratitude to my interviewees. My own network in healthcare related cyber security experts is non-existent, so I had to approach people via LinkedIn. I am grateful that these four men were enthusiastic enough to grand me some of their time and many of their insights.
Finally, I would like to thank Chris, my friends, roommates, readers, and others who have helped and supported my throughout the entire process. Especially, I would like to thank those who spend their free time reading and trying to make some sense out of my creative structured sentences and argumentations. Finally finally, a special thanks to my brother and parents, who have been a great help and support all these years.
4
Table of Content
Foreword ... 3
List of Figures ... 6
List of Tables ... 6
1. Introduction ... 7
1.1 Background ... 7
1.2 Research objective and key concepts... 9
1.3 Thesis structure ... 10
2. The rise of ransomware and how it challenges the Dutch healthcare industry ... 11
2.1 What is cyber security? ... 11
2.2 What is ransomware? ... 12
2.3 How does ransomware challenge the Healthcare industry? ... 17
2.4 What is the legal framework that the healthcare industry has to deal with? ... 19
2.5 Conclusion ... 21
3. Challenges in incident information disclosure ... 22
3.1 Why incident information disclosure? ... 22
3.2 The academic discussion about incident information disclosure ... 25
3.3 Bringing incident information disclosure and healthcare together ... 28
3.4 Adding ransomware to the equation ... 30
3.5 Conclusion ... 30
4. Putting an incident information disclosure framework into practice ... 31
4.1 The incident information disclosure framework ... 31
4.2 How the incident information disclosure framework will be used ... 34
5 The implementation of incident information disclosure in the healthcare industry ... 36
5.1 The different incident information disclosure strategies ... 36
5.2 A comparison of the strategies ... 41
5.3 Identified limitations of the framework ... 49
5.4 Validity and reliability of the research ... 52
5.5 Conclusion ... 54
6 Conclusions and recommendations ... 56
6.1 Result conclusions ... 56
6.2 Research contribution ... 57
6.3 Recommendations for further study ... 57
7 Bibliography ... 59
Appendices ... 65
5 Appendix A.1: The overview of the interviews. ... 65 Appendix A.2: The standardized interview guide. ... 65 Appendix B: Transcript of the interviews ... 67
Appendix B.1: Interview met Interviewee A - Managers ICT Healthcare institution A – 25-09-2017 ... 67 Appendix B.2: Interview met Richard Broekhuizen Afdelingsmanagers ICT Applicatiebeheer Franciscus Gasthuis – 22-09-2017 ... 71 Appendix B.3: Interview met Juriaan Rijnbeek - Chief Information Security Officer Leids
6
List of Figures
Figure 1: An example of how most of the crypto ransomware works (Deloitte, 2016) 14
Figure 2: Global growth of ransomware (Reesalu, 2016) 15
Figure 3: The IRMA wheel (Jaatun, Albrechtsen, Line, Tondel, & Longva, 2009) 23 Figure 4: A detailed picture of the detection and resolve phase (Jaatun, Albrechtsen, Line, Tondel, &
Longva, 2009) 24
Figure 5: The Learning phases in more detail (Jaatun, Albrechtsen, Line, Tondel, & Longva, 2009) 24
List of Tables
Table 1: Treat Actor Motivation Matrix 17
Table 2: Incident Information Disclosure Challenge Matrix as designed by Kulikova et al (2012) 32
Table 3: Summary of the relevant questions and dimensions 35
Table 4: The framework of the Healthcare institution A 36
Table 5: The framework for the Fransiscus Gasthuis Vlietland 38
Table 6: The Framework for the Leids Universitair Medische Centrum 39
Table 7: The framework of the Healthcare Institution B 40
Table 8: The answers of the Hospitals about regulatory compliance 42 Table 9: The answers of the Hospitals about the reputational aspect 44 Table 10: The answers of the Hospitals about the cost-efficiency aspect 45 Table 11:The answers of the Hospitals about the prevention aspect 46 Table 12: The answers of the Hospitals about the harm mitigation aspect 48 Table 13: The framework with the suggestions to improve the framework implemented 52
7
1.
Introduction
On the 12 of May 2017, a large scale untargeted ransomware attack infected computers in 150 different countries (Lord, 2017). Both private computers and critical infrastructures like a Spanish telecom company, the Deutsche Bahn and the British National Health Service were attacked. This attack was carried out by malware known as the ransomware WannaCry. The WannaCry ransomware is considered to be the largest ransomware attack in the history of cybercrime. WannaCry frightened the world as it was able to infect multiple critical infrastructures, including sixteen hospitals in the United Kingdom. However, this was not the first time healthcare systems got attacked by
ransomware and it will certainly not be the last (Demuro, 2017).
Ransomware is a very lucrative and growing part of cybercrime and this trend is not likely to change. In 2016, 5.5 percent of all the reported cyber-attacks were considered ransomware, however in the first part of 2017 this number had already increased to 10.5 percent (Deloitte, 2016). In addition to the overall rise in ransomware, there are sectors that are more targeted than other. The healthcare sector is one of the sectors that faces most attacks and there is no indication that this trend will slow down any time soon (Beek, McFarland, & Samani, 2016).
Although various reasons drive attacks on specific target groups, experts agree on reasons why the healthcare industry is often targeted. One of these reasons is believed to be the dependence of the healthcare facilities on reliable patient data that makes them such a popular target. If access to patient information is denied or delayed, execution of care and/or surgeries can be obstructed. It is therefore assumed by cyber criminals that hospitals have a higher incentive to pay the demanded ransom. (Demuro, 2017) (Beek, McFarland, & Samani, 2016) (Gammons, 2016).
Second, the General Data Protection Regulation (GDPR) is expected to intensify the rise in
ransomware attacks in the healthcare sector even more (Kruse, Frederick, Jacobson, & Monticone, 2017) (Pope, 2016) (Zerlang, 2017). The GDPR is a European wide regulation – that will be
implemented in May 2018 - aimed to strengthen and unify data protection within the European Union.
The GDPR acknowledges ransomware as a data breach, which is the reason for the expected increase in ransomware that targets the healthcare sector (European Parliament and Council, 2016). This can have far-reaching consequences for the operability of the healthcare institutions. Not only is it important that healthcare institutions are aware of this, but it is also an opportunity for the academic community to study the transition that many (healthcare) institutions and governments experience or face due regulations in cyber space.
The GDPR will bring two main changes for industries and sectors. The first is the obligation to disclose data breaches. The second is the possibility to be prosecuted if one fails to meet this obligation (Zerlang, 2017) (Green, 2017). The prosecution follows the incorrect or absent disclosure. It is important that – in order to prevent prosecution – the disclosure strategies are adequate and correct. Therefore, this study focusses on how hospitals deal with ransomware attacks, how they shape their disclosure tactics and how the current practices could change due to the GDPR. Due to the limited size of this study, it will be delineated to the Netherlands and the Dutch healthcare industry. Before the research objective will be discussed, first some background information about the GDPR and the expected challenges for the healthcare sector will be provided.
1.1
Background
8 1950s with The Convention for the Protection of Human Rights and Fundamental Freedoms, drafted by the - then newly formed - Council of Europe (Weston, 2016). The convention set out basic principles that form the foundation of many laws in the EU today. One of these principles underlined that everybody ‘has the right to get respect for their private and family life’. Although this form of respect might seem trivial and basic, this principle forms the basis of many of the privacy issues that are debated these days.
The right to respect was critiqued by many for being ambiguous and uncontrolled. The critique on the vagueness of the principle together the rise in the use of computers led the Council of Europe’s Convention to the protection of individuals with regard to automatic processing of personal data (Weston, 2016). Although computers were used to process citizens data, its use was not widespread and the regulation of automatic processing of personal data was sufficient for over fifteen years. A change in the use of computers came in the 1980’s and 1990’s when the availability and therefore the utilization of computers became a widespread phenomenon. This drastically changed the way data was collected and processed. It changed how data could cross borders and was used within the EU. The fact that data could cross borders within the blink of an eye created a lot of trouble for the member states. Data protection laws of one nation were not necessarily compatible with the data protection laws of other nations, making it hard for governments and companies to use and share data (Weston, 2016)).
The problems with data crossing borders eventually led to the Data Protection Directive of 1995, were the EU obligated its member states to live up to minimum standards of data protection. The Data Protection Directive brought the EU member states laws closer together and eased the way EU data internally crossed borders. However, the implementation of the Data Protection Directive of 1995 differed per country, leaving the EU again with different regulations that slowed down technological progress and the free flow of data. The Data Protection Directive that was meant to lead to the free flow of data has turned out not to be sufficient and this situation eventually led to the creation of the GDPR (EU, EU GDPR, 2016) (Weston, 2016).
There are a view differences between the Data Protection Directive and the GDPR that make sure that the GDPR will unify the EU data protection laws. The most important difference is that the GDPR is a legally stronger instrument in so much as it is a regulation and not a directive. Where a directive is a minimum set of requirements, is a regulation effectively a law that all member states have to comply with (EU, EU GDPR, 2016).
Second, the fact that the GDPR states that anybody who holds data of EU citizens is bound to comply with the GDPR. Facebook, Gmail, app providers, and other companies that collect data with the purpose to sell it are now bound to the GDPR. The GDPR therefore does not only cover EU member states, but also forces companies to follow its rules (European Parliament and Council, 2016). In addition, member states have more rights (and obligations) to monitor how companies and governments collect, process, and use personal data.
Finally, the GDPR puts the individual in a central position and will make it the owner of her/his data. As a result, organizations must provide insight on how data is obtained and processed in an, for any individual, understandable way. Not being able to provide this insight will be seen as uncompliant and can bring severe (financial) consequences (Green, 2017) (EU, EU GDPR, 2016).
9 retribution by the authorities burdened with the task to enforce the GDPR (EU, EU GDPR, 2016) (Zerlang, 2017).
Due to the sensitivity and value of the data processed by healthcare institutions, some experts are convinced that they will experience a rise in attacks (Demuro, 2017) (Kruse, Frederick, Jacobson, & Monticone, 2017). Cyber criminals will take advantage of the fact that their ransomware demands are far easier to meet than prosecution that will follow when healthcare institutions fail to provide insight on the legitimacy of their data distribution.
The way healthcare intuitions respond to ransomware attacks plays an important role and this will become more important when the GDPR becomes active. Looking at the response strategies and how this will change due to the implementation of the GDPR is therefore a useful research that can give insight on the way targeted industries and institutions handle this rising threat.
1.2
Research objective and key concepts
The key ingredients for this research are ransomware attacks on Dutch hospitals, the incident information disclosure issues that need to be made when a hospital faces a significant ransomware attack, and on which motivations the decisions are build. The exploratory part of the research will focus on which academic models can be used to explain hospitals incident information disclosure strategy and how these models can help hospitals to design one if such a strategy does not exist yet. Cyber security is a relatively new domain that touches upon the core businesses of people and institutions. This study will contain of an in-depth literature study and interviews with an amount of Dutch hospitals to provide insight on how Dutch hospitals deal with the current and growing ransomware threat. By taking these steps, this study will answer the following question:
“What are the cyber incident information disclosure strategies of Dutch healthcare institutions during and after a ransomware attack and how is this expected to change due to the GDPR?”
The research question contains ambiguous key concepts that need explanation. To prevent confusion, important definitions that will be used in this study regarding ransomware are defined. Many different articles, books, and institutions use different definitions of the key concepts of the research question. Therefore, the definitions that have been chosen are the definitions that are used by the authors whose research form the keystones of the literature research of this study.
Cyber incident: Coombs (2015) describes an incident as a localized disruption with the potential to disrupt the larger organizational routine and cause a crisis situation. A cyber incident is therefore considered to be a disruption in the information or operational information system of an institution with the potential to harm (parts of) the institutions operations. What the precise definition of a cyber incident entails depends on de interpretation of the institution involved.
An incident itself is not considered a crisis, but it has the potential to cause a crisis or a crisis
situation. Since a crisis can be the result of a cyber incident - and therefore often used in this study - it is important to define the concept of crisis. The term and concept “crisis” is defined as followed: Crisis: ‘the perception of an unpredictable event that threatens important expectancies of
10 Healthcare institution: With health care institution a public, private, or non-profit organization that provides healthcare and healthcare related services to people whose physical or mental health is compromised in any way is meant (OregonLaws.org, 2007).
Ransomware attack: A cyber-attack that installs malicious software on a computer or IT-system that is designed to extort ransom payment from its targets by either encrypting of blocking access to files (Demuro, 2017).
Ransomware is a specific form of a cyber-attack. To clarify the origins of ransomware, one need to define and explain what the larger and overarching term of cyber-attack entails. The term and concept “cyber-attack” will be used a lot in this study and is defined as followed:
Cyber-attack: ‘An assault on system’s security that derives from an intelligent threat to evade security services and violate the security policy of a system. Attack can be active or passive, by an insider or by outsider or via attack mediator’ (Jordan, 2008).
1.3
Thesis structure
This study will start with a theoretical section that are presented in chapter 2 and chapter 3. Chapter 2 will provide an in-depth literature study on ransomware focussing on what it is, how scholars expect it to develop in the (near) future, and the role of ransomware in the healthcare industry. Chapter 3 provides an in-depth literature study on incident information disclosure. First, the role of disclosure in incident response will be described. Second, a literature overview, including knowledge gaps and further research that has been identified by scholars working in this academic field. Chapter 4 discusses the theoretical framework that was used to test if academic literature can help improve the incident information disclosure strategies of Dutch hospitals.
11
2.
The rise of ransomware and how it challenges the Dutch healthcare industry
Cybercrime is a fast developing security threat to both the private and the public sector. Globally there is the emergence of a cyber-crime sector that develops and executes all kinds of cyber-attacks like theft of intellectual property or identity, cyber-espionage, malware and DDoS attacks (Symantec, 2017). Experts see increasing numbers, but also a rise in the sophistication of these attacks. An increase in sophistication means that the attack is more effective, also it makes it also harder to prevent and enables the attacker to infect more complex systems and infrastructures. Different forms of cybercrime are different in nature and require different forms and ways of cyber security and cyber security policy. Due to that, looking at the security implications of ransomware is an important but useful step. However, other types of cybercrime require similar research as well. Since the mid-2000s, ransomware has been a prominent threat to individuals, small to medium sized businesses, enterprises and critical infrastructures. In the first months of 2016, the Internet Crime Complain Centre, a US multi-agency task force consisting of the FBI, the National White Collar Crime Centre and the Bureau of Justice Assistance, received 718.000 reports of corporations who had fallen victim to ransomware (Lord, 2017). The United Stated has been a target for cyber criminals who exploit ransomware, but are not an exception. In the Netherlands, ransomware accounts for over 12 percent of the total amount of cyber-attacks with over 300 000 reports per month (NCTV, 2017). Since not nearly all ransomware attacks are reported, the estimation of the real number of victims is much higher.To be able to anticipate on these growing threats, it is important to understand them and where it comes from. This chapter will therefore provide information on what ransomware is and the role it has played regarding healthcare. To provide a clear picture, first the overarching concepts of cyber space and cyber security will be discussed. Secondly, a more in-depth analysis of ransomware will be provided followed with an analysis of the ransomware threat in the Dutch healthcare industry. Finally, the chapter will be closed by a paragraph about the laws and regulations the healthcare industry has to take into account regarding ransomware.
2.1
What is cyber security?
Ransomware is just a small, but not insignificant, part of the cyber domain. The cyber domain has been exponentially growing in the past decades, which is best illustrated by the central role that the internet, one of the key components of cyber space, fulfils in modern day society. With both the growth of the domain and society’s dependency on cyberspace, there is a growing need to secure it. The sector that is burdened with this task is called the cyber security sector.
The cyber domain is, as everything in life, a sum of many historical processes and to understand this domain it is important to shed some light on where cyber space came from. These processes started half a century before the use and comfort of cyber space reached the public domain and was
adopted by many parts of society (Warner, 2012). The exponential growth that has been the result of the worldwide adoption of the cyber domain is enabled by the technological advances that changed the way how data and information is stored and transmitted. These changes are often referred to as the proliferation of information and communication technology (Kello, 2013).
12 these messaging applications in such an overwhelming way that the time we are living in now is referred to as ‘The Information Age’ (Choucri, 2014).
Due to the complexity of the concept of the cyber realm and the fact that it has characteristics that cannot be found in other domains it is considered to be a domain of its own. There are three characteristics that distinguish the cyber domain from others: It is considered to be contested by scholars, the fact that it is relatively new and dynamic and it changes the way actors can interact and therefore the relevance of the actors involved (Herzog, 2011) (Knight, 2017).
The first characteristic, the fact that cyber space is seen as contested, is a believe that mainly circles in the academic domain. The technology that has made the cyber domain possible pushed many ways of societal change. Examples of change happened via the disruption in power structures and the way border have disappeared. This has made they cyber domain contested, meaning that it is a domain where no actor is currently able or willing to exercise full authority (Kello, 2013) (Solms & Niekerk, 2013)
The second characteristic of the cyber domain, the fact that it is new and dynamic, makes that some scholars claim that research and conclusions about this domain are provisionally. They claim that phenomena that are observed are still so new that hard conclusions cannot be drawn from it, let alone predict in which ways the current developments will evolve (Kello, 2013). Nazli Choucri (2014), a professor of Political Science at MIT, states that is it is not unlikely that the lines within the cyber domain have to be completely redrawn in the near future due to an unforeseen game changer. In addition, the fact that the cyber domain is controlled by both the private and academic sector, make it hard for policymakers to get grip on this domain. To make informed and effective policy, both ownership and expertise are required and both are, although developing, still lacking in many governments (Choucri, 2014).
Finally, the characteristics of the cyber domain have changed how actors interact with each other and how the power structures work within these interactions. With the rise of nation states, the burden of security became one of the main tasks of the nation state. However, in the cyber domain power is distributed among many actors, giving the nation states a role among many instead of a security monopoly (Herzog, 2011). Academia, the private sector, organized groups and even individuals have more capacity, knowledge and space to move in the cyber domain than could ever be possible in the off-line world. This, together with the extreme interconnectedness that is possible in cyber space, has complicated many concepts that defined the nation states and the power
structures in which they operate. Concepts of jurisdiction, accountability and (territorial) sovereignty have to be redefined and until that is done, policymaking in the cyber domain will remain a challenge (Tsagourias, 2016).
Cyber security is, in this study, defined as the “the protection of the cyber domain, including the physical objects on which it relies and those that operate in it” (Solms & Niekerk, 2013). Cyber-attacks happen in many ways and exist in many forms. One of these forms is ransomware, which is the cyber threat that his study focusses on. The next chapter will elaborate more on what
ransomware is, who uses it and what the threats are for the healthcare industry.
2.2
What is ransomware?
13 in-depth explanation of ransomware will be given and second the different threat actors will be explained.
2.2.1 Ransomware
The name ransomware is derived from the words ransom and malware, and as the name suggest is a type of computer malware designed to extort ransom payment from its targets (Demuro, 2017). While ransomware is perceived as one of the biggest cybercrime threats since 2005, the first known ransomware attack has occurred much earlier and in fact, targeted the healthcare sector. In 1989 an AIDS researcher by the name of Joseph Popp carried out the first ransomware attack by distributing 20 000 floppy disks to AIDS researchers all over the world. On the floppy discs he installed a program that displayed a message demanding payment for a software release. Popp was arrested and
declared mentally instable, which meant the end of his career in both AIDS research as writing computer malware (Lord, 2017). However, ransomware did not fall with Popp and has developed much since it first saw the light of day.
Looking at ransomware nowadays, there are two different categories; Locker and Crypto. Locker ransomware does not encrypt the files of the victim but (temporarily) blocks access to the computer in combination with scare tactics to generate payment. Upon infection, the computer displays a message stating that the computer has been used to commit some sort of crime like the viewing of child pornography. If the ransom demand is not met, the victim will face criminal charges and/or public shaming (Deloitte, 2016).
Crypto ransomware encrypts victims’ files and/or data by using multiple methods of cryptography. There are many types of ransomware in circulation that all act by disabling specific programs or functions of the computer. After the infection, a message will be presented demanding a ransom payment in exchange for the key to unlock the computer, programme or function (Pathak, 2016). There is no guarantee that the key will be received after the ransom payment, however in the vast majority of the payments the key will be disclosed after payment is received (Reesalu, 2016).
Crypto and Locker ransomware are used on different target groups. Locker ransomware is more used to target individuals who have, compared with enterprises or institutions, little knowledge and recourses to protect or defend themselves. Crypto ransomware is used to target victims who rely on their data to execute their daily activities. This can be anything from small businesses to government institutions. The threat that healthcare institutions face comes from this type of ransomware since it is the hospital data that is the true value of the business (Pope, 2016). Due to the fact that Locker ransomware plays a negligible role in the ransomware that is used to target the healthcare sector it will not be taken into account in this study. From now on, the term ransomware is used in the meaning of Crypto ransomware, where the device is still accessible but the data is encrypted or corrupted.
14 Ransomware is a method used to obtain revenue direct and on a large scale. This method has proven to be effective and therefore it is seen as the main contributor to the fact that the amount of
ransomware attacks worldwide is rising. Experts see a trend in which cybercriminals are realizing that small and easy to replicate attacks can be carried out against a large variety of corporations, thereby producing a substantial revenue (Lord, 2017). These low barrier attacks increase the earning
prospects for cybercriminals as only a small percentage of victims need to pay the ransom to provide a vast amount of money (Demuro, 2017).
The trend of more diversity in victims is likely to persist due to the fact that ransomware, as many security issues, also has a big societal component. First of all because people tend to pay the ransom, which makes them more attractive to become a target again. Globally, around 34% of the victims pays the ransom. However, these numbers differ across countries. In the United States, around 64% of the victims pay the ransom demand. Many writers point out the connection between the fact that the US is the most targeted country in the world and also has the highest percentage of victims paying the demanded ransomware1 (Symantec, 2017) (Demuro, 2017).
The second social component of the ransomware issue is the rise of ransomware-as –a-service (RaaS) products (Reesalu, 2016). Potential attackers do not longer need to rely on their own technical abilities, knowledge and resources to carry out ransomware attacks. Purchasers can anonymously shop on the Dark Web, pay with Bitcoin and carry out and attack without knowing the slightest about the technical components of ransomware. This makes it widely accessible and easy to exploit
(Robinson, 2016).
Finally, the amount of successful ransomware is on the rise. By far the greatest amount of
ransomware attacks are distributed via so-called phishing emails. These official-looking emails can be extremely hard to distinguish from the real official emails. People click on the link in the email and before they realize, their device has been infected (Symantec, 2017). The fact that the success rate of a ransomware attack depends on the human ability to distinguish an official-looking email from an official email makes it very hard to secure a device or system. As cyber criminals learn and phishing
1Many sources use the United States as example when talking about the connection between the amount of times persons or companies in a county are targeted by ransomware and the percentage of victims that pay the ransom. However, it needs to be point out that this is not proven and that other factors, such as amount of connected devices, data protection laws and the fact that bitcoin as a payment method became available and widely used, also play a significant role.
15 emails are becoming harder to identify, the percentage of successfully carried out ransomware attacks is likely to rise.
These and many more factors contribute to the rise in the use of ransomware. As more ransomware attacks are carried out successfully, distributing ransomware gains more publicity and therefore the attention of technical individuals who are looking to earn quick money. Although there are
mechanisms and policies designed and put into place, experts expect this rising trend to continue in the future (Symantec, 2017) (NCSC, Cyber Security Assessment Netherlands 2016, 2016) (Lord, 2017).
Figure 2 shows the global rise of ransomware attacks mentioned in in the media from 2013 until early 2016. Besides the overall rise in attacks, the peaks, who represent the major events, also show an increase in the amount victims.
The effectiveness of ransomware as a tool to gain revenue is roughly due to two factors: the fact that it exploits both the embarrassment of the victim as the victims’ urgency to access the files to force them to pay the ransom demand. These two factors make the healthcare organizations are appealing targets to the hackers who use this type of malware to make fast and easy money (Perakslis, 2014). Cybercriminals know this and the healthcare industry is targeted more by ransomware than any other industry. Researchers estimate that in the year 2015 alone, approximately 24 million US dollars in ransom was paid by healthcare organizations to ransomware hackers. The next paragraph will show more in-depth information about different ransomware attacks that have happened to
healthcare institutions worldwide. Furthermore, it will provide a closer look on how Dutch healthcare institutions are handling their cyber security and protect themselves against ransomware threats.
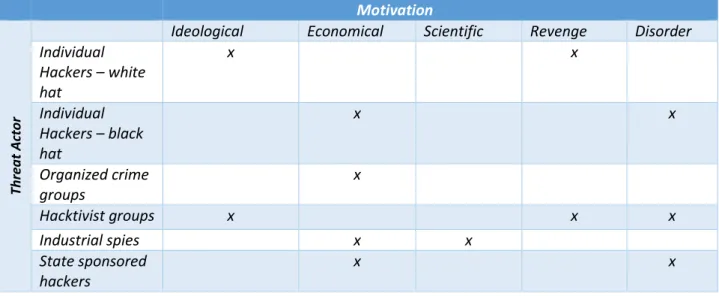
2.2.2 Threat actors
There are different types of threat actors and each of these types has its own motivation. Due to the fact that cyber space does not know state borders, prosecution or legal action against these actors has proven to be difficult if not impossible. Knowing who they are and what they are after is
therefore important to know to implement the right defence mechanisms (Sommer & Brown, 2011). In general, the current literature on cyber threats distinguishes the following groups of cyber
16 adversaries who are likely to target the healthcare industry (PWC, 2011) (US-CERT, 2017) (Capasso, 2011) (Demuro, 2017):
Individual hackers
Individuals who attempt to take computer functions, programmes or files hostage for their own specific purpose and personal gain. In general, a distinction between white and black hat hackers is made. White hat hacker’s aim is to expose the greed and corruption inside big business and
institutions to show the public what is going on behind closed doors. Other white hat hackers might hack for fun and fame. If one of those white hat hackers finds a leak in the system she or he will notify the institution or company. White hat hackers are sometimes also revered to as ‘hacktivist’ as they use their hacking methods to make a stand against the establishment.
On the opposite side of the spectrum one can find the black hat hackers. The goals of black hat hackers are more clearly defined as their aim is primarily focussed on personal, mostly financial, profit. They are actively looking for ways to enter systems to exploit them. This group of hackers is most likely to use ransomware against a target.
Organized crime groups
These are groups that exploit computer systems and the internet for, mostly, economic fraud to usurp money, property or legal rights. Organized crime groups who use the internet to execute their activities do not differ from traditional organized crime groups in goals or how they function. The only thing that does differ are their choice of methods.
Some might call activist hacker groups like Anonymous, a semi-organized hacktivist group, an organized crime group. Others might argue that due to the fluid and unorganized structures hacker groups maintain they cannot be called organized crime but are rather individual white hat hackers who pursue alliances for specific targets or projects. During these study, hacktivist groups as Anonymous are considered an organized group.
Industrial spies
These are individuals or groups of people that use hacking techniques to obtain secret or confidential information for commercial purposes. The information industrial spies are looking for mostly consist of new science or technology methods, or healthcare specific, new methods to threat illness or produce medicines.
State sponsored hackers
These are individual hackers or groups who are sponsored by their own or another nation state to perform espionage or sabotage in other countries. Their interest lies most of the time in matters of national security or causing disorder to serve some political purpose.
17
Table 1: Treat Actor Motivation Matrix
Motivation
Threa
t
A
cto
r
Ideological Economical Scientific Revenge Disorder Individual
Hackers – white hat
x x
Individual Hackers – black hat
x x
Organized crime groups
x
Hacktivist groups x x x
Industrial spies x x
State sponsored hackers
x x
One of the most difficult parts of dealing with cybercrime is the fact that it is extremely hard to trace the individual or group that is responsible for the attack. This is due to two factors: on the one hand the features of cyber space and on the other hand the reluctance to report attacks. The features that cyber space entails, among others, the anonymity of the dark web, the anonymity of the payment methods and the fact that it is easy to hide one’s location makes it often impossible to appoint a perpetrator, let alone bring him or her to justice. As noted before, institutions are often not willing to share or report ransomware attacks out of fear to lose their good reputation. It is needless to say that if a ransomware attack is not reported, there will be no investigation that might lead to the identification of the attacker.
Due to the fact that tracing ransomware exploiters is extremely difficult, it is not possible to mark any of the in Table 1 presented threat actors as more or less likely to be behind ransomware attacks against healthcare institutions.
An example of a ransomware attacks that has been investigated is the, earlier mentioned, WannaCry attack. WannaCry targeted many different institutions worldwide and thereby gained much media attention. After months of investigation, it has been announced that North-Korea is most likely to be behind this attack (Sharman, 2017). Although there is a suspect in this particular case, this cannot be generalized by stating that most ransomware attacks against healthcare institutions are state sponsored.
2.3
How does ransomware challenge the Healthcare industry?
The past years, researchers have seen the use of ransomware attacks against healthcare institutions rise due to multiple reasons. As mentioned above, the need to maintain a good reputation and the urgency to access the data are among these reasons. Others are the vast increase of the Internet of Things within hospitals, the digitalization of almost all data used in healthcare institutions and the value third parties assign to medical records (Pope, 2016). A medical record is worth far more than the credit card number of the same individual2, therefore by targeting the healthcare industry hackers can make money twice using the same hack. Ransomware is sophisticated enough to steal
18 information and lock a computer or function, enabling the hacker to use or sell this data (Demuro, 2017). However, the worst-case scenario is still when ransomware purposefully shuts down important information system or medical equipment. This may prevent healthcare institutions to provide the medical aid patients need, risking (permanent) health damage or even death (Kruse, Frederick, Jacobson, & Monticone, 2017).
Widespread targeted and non-targeted ransomware attacks are becoming daily practice and the healthcare industry has given priority in securing its devices. This is an important step forward, however with, among other things, the high possibility of a human error hospitals cannot assume that they are a hundred percent protected.
When healthcare institutions face a ransomware attack, the impact fully depends on the nature of the infection and the security precautions and measures the institution has taken. The impact therefore can differ from a few hours work were infected computers need to be replaced and backups need to be restored to days of downtime resulting in a heavy ransom that is met. Approximately 90 percent of the healthcare institutions have faced some kind of data breach or ransomware attack between 2014 and 2016 (Kruse, Frederick, Jacobson, & Monticone, 2017). Most of these attacks where not successful or important enough to make the headlines, but some of them did. A few examples are listed below to show how eminent the current situation is and where it can lead to.
The first example is the ransomware attack on Hollywood Presbyterian Medical Centre in early 2016. This attack is the most famous ransomware attack on a hospital so far, due to the $17,000 ransom demand that eventually was met (Gammons, 2016). After ten days without access to electronic medical records the hospital transferred the bitcoins and got the key to decrypt the files. The second example does not stand out due to the amount of ransom that was paid but the magnitude of the attack. In March 2016 the MedStar Health IT system was successfully attacked. Medstar is a large non-profit healthcare organization in the United States and this attack affected ten of their hospitals and over 250 outpatient centres within minutes. All the hospitals and outpatient centres had their own downtime plan and where prepared for partially failing systems, but were not prepared for an attack with this magnitude (Gammons, 2016). The complete loss of data and
different downtime procedures made it very hard for the organization to recover. This attack shows that targeting a healthcare systems can be with far-reaching consequences (Gammons, 2016). The third example are the British hospitals that were shut down by the WannaCry ransomware in May 2017. This ransomware hit over ten thousand victims in almost 100 countries. WannaCry randomly attacked outdated and not upgraded systems worldwide, shutting down hospitals, telecom companies, shipping companies and many more. This attack shows that attacks are not always targeted but that hospitals can become victims from relatively simple but widespread ransomware attacks that use known security gaps in outdated systems or default passwords (Gayle, Topping, Sample, Marsh, & Dodd, 2017).
19 However, it is not certain how if any data of the targeted hospitals was obtained by the attackers (Stokmans, 2017).
2.4
What is the legal framework that the healthcare industry has to deal with?
The main responsibility of cyber security lies with the companies and institutions who are obliged to protect and secure their own systems and infrastructure. Looking at the laws and regulations regarding cyber security and cyber incident information disclosure, stakeholders have various opinions. The Dutch Coordination for Terrorism and Safety(NCTV) states that the Dutch legal system lacks the fundaments to deal with the problems that come with the technology we currently have (NCTV, 2017). According to them, different institutions report missing laws and regulations which put them in difficult positions regarding sharing of information or the extend in which institutions have to invest in their cyber security and safeguarding.
On the other hand, various industries have complained about how strict the regulations are and how this obstructs them in their work (NVZ, 2017) (NCTV, 2017). Privacy and accessibility are both parts of the cyber security laws and regulations and sometimes it is not clear when privacy is valued above accessibility or the other way around. Therefore, before any judgement about the Dutch cyber security laws can be provided, an overview of these laws is required. This paragraph will give an overview of the Dutch laws regarding cyber security of healthcare institutions and information disclosure in the case of a cyber incident. The laws and regulations are mostly related to information security and information disclosure and not necessarily on malware or more specific ransomware. Wbp and GDPR
The Law protection of personal data[Wet bescherming persoonsgegevens] or Wbp is a Dutch law that focusses on the protection of personal data gathered by companies or institutions. The Wbp provides the boundaries for which data can be used and how it must be stored, protected and shared. The Wbp knows a disclosure clause that states that if there was an actual data breach or an attempt to, the attacked institution must inform Dutch Data Protection Authority (CIP, 2017). On the 25th of May 2018 the Wbp will be replaced by the GDPR, a regulation very similar to the Wbp but European wide implanted. Many European countries have data protection laws, the GDPR aims to unify these laws and forces countries and companies to upgrade their protection. Under the GDPR, all the EU member states have the same privacy protection laws in place (CIP, 2017). The GDPR will bring three main changes.
First, in addition to stricter data protection measurements, the GDPR introduces sanctions for companies or governments which fail to protect personal data. These sanctions can rise to 20 million Euro or 4% of the annual worldwide group turnover, depending on which of the two is higher. Second, the GDPR will introduce is the obligation to report data breaches to the supervisory
authority of the country within 72 hours after notice (European Parliament and Council, 2016). Final, the GDPR underlines the rights of the individual whose data is being collected, stored and used. The organisations using data will have more responsibilities regarding the accountable use of this data. NEN 7510
20 NEN 7512: Standard for a base of trust that if patient data is shared the receiver must be
know and trusted and the identity of the sender and receiver must be stored together with the medium of sharing.
NEN 7513: Standard for a login database of everyone that has had access to an individual’s electronic patient dossier.
NEN 7521: Standard for who is allowed to access an individual’s electronic patient dossier. As the above mentioned laws, standards and regulations show, information security and privacy are prioritized. However, these laws and regulations only cover a very small spectrum of the cyber security, data security, access regulation and information disclosure that healthcare institutions have to deal with (NCTV, 2017). Due to the fact that many aspects are not covered yet, there are some urgent issues that need to be addressed. One of these issues in the healthcare sector is the organizational shift of many healthcare tasks from the national government to the municipalities. Municipalities are not (yet) included in the above-mentioned data security laws and regulations and therefore have no legal basis or requirements for shared patient medical data (NCTV, 2017). Another point is that municipalities struggle with the standards of cyber security and that their security is behind the standards that are required for handling patient data (Lee, 2017).
The second point of concern regarding the current state of legal affairs of cyber security is the fact that malware, and therefore ransomware, has no place in it (NCTV, 2017). With the change from Wbp to GDPR, the obligation to disclose information in case of a possible data breach comes to expire. If an institution faces a ransomware attack it is its own responsibility to seek help or inform institutions (Schippers, 2016). There are no obligations regarding information disclosure regarding data breaches or compromises unless the institution is certain dossiers or traceable personal data is leaked (Schippers, 2016).
In additions to laws and regulation, there are initiatives to support different industries that are facing ransomware threats. The government has initiated a few initiatives to help companies and
institutions to protect themselves and others by sharing information. The latter forms a big hurdle when it comes to improve one’s cyber security. Companies are reluctant to share information due to, among others, economical and reputational reasons. These initiatives have the goal to make sharing easier so sectors are not competing but collaborating in securing their businesses and organisations (NCTV, 2017). The next paragraphs will highlight the different options there are for sharing
information regarding cyber, and especially ransomware, attacks. ISAC Healthcare
Information Sharing and Analysis Centres (ISACs) are public-private partnerships which are established to share information about cyber threats and vulnerabilities per sector (NCSC, ISAC's, 2017). The purpose of the ISAC’s is to form sector wide alliances to “facilitate the exchange of threat-related information and joint resistance” of the Dutch critical infrastructures (NCSC, 2016). ISAC’s are permanent networks where participants meet regularly and build up trust to be able to share
confidential information that will help protect the sector against cyber threats (NCSC, ISAC's, 2017). Z-CERT
21 National Cyber Security Centre
The National Cyber Security Centre (NCSC) functions as the Dutch central information and expertise hub for the entire cyber security field. There are four main tasks that the NCSC fulfils: Response to threats and incidents, perception and action prospects, improving crisis management and cyber security collaboration platform (NCSC, What is the NCSC?, 2017). The NCSC facilitates the different ISAC’s and provides assistance to institutions that need it.
2.5
Conclusion
Ransomware is a worldwide growing threat to healthcare institutions. Hospital shutdowns are the, occurring, worst case scenarios. However, data leaks that are increasingly associated with
ransomware attacks are a big concern as well. The Dutch healthcare institutions are a target but have not experienced downtime due to ransomware yet. Due to the different kind and different
magnitude of ransomware attacks, (Dutch) healthcare institutions must be aware of the possibility that their system or data is vulnerable for an unknown gap in their security.
22
3.
Challenges in incident information disclosure
Information disclosure has been present in ethical and medical debates since the Hippocratic Oath four centuries BC (Kantarjian & Steensma, 2014). The rise of cyberspace added a new dimension to this debate. Cyber security, data security, data sharing, and data collecting are just a few of the new struggles. One of the main difficulties of this part of medical service and treatment is the fact that it lies completely out of the familiar comfort of most of the healthcare providers that are concerned with the daily care of patients (Kruse, Frederick, Jacobson, & Monticone, 2017) (Sommer & Brown, 2011).
This chapter will focus on the academic debate and the development of incident information disclosure. First, it will be argued why incident information disclosure is so important and what role disclosure plays when dealing with incidents. The paragraphs that follow will describe cyber
incidents, especially ransomware, information disclosure in the healthcare industry.
3.1
Why incident information disclosure?
Looking at disclosure, a full picture about actions and motives of healthcare institutions can be provided. There are many aspects of an incident information disclosure strategy that will take you through the entire life cycle of a crisis. Therefore, disclosure strategies provide an interesting, diverse, and overarching angle to the response of a big ransomware attack.
There are many different aspects associated with incidents and incident response. This paragraph will reflect on the different aspects of incident response and provide an explanation why incident information disclosure is one of the aspects worth studying. The different aspects of incident response are discussed via de Incident Response Management (IRMA) method. The IRMA method is developed for sociotechnical environments that face a computer security incident like Distributed Denial of Service (DDOS), malicious code, unauthorized access (like ransomware) or incidents due to inappropriate usage. Important to note is that the IRMA is developed for companies whose ICT systems are significantly supporting, but are not part of their core business. In other words, the IRMA method is developed for organizations were organizational and human factors are leading and technology is merely there to support the organizational and human processes (Jaatun, Albrechtsen, Line, Tondel, & Longva, 2009).
Figure 3 shows the IRMA wheel with the phases and how they are interrelated. The IRMA framework exists three phases of incident response:
- Prepare: Plan and prepare for both the incident as the incident response
- Detect and recover: Detect the incident and restore as quickly as possible to normal operations
23 Figure 3 shows how the external dynamics connect with the wheel in the prepare phase. This means that incident response and the people who bear the responsibility do not operate in isolation. The external dynamics, placed on the outside of the IRMA wheel, can be various things. For example, the incident response team and the information security management must work together, learn from each other, and know how to find each other when an incident occurs. Or it can be that both the incident response team and the information security management team have regulations to take into account. Last it can be government, including the Dutch government, which stimulates sector wide cyber incident information sharing so that stakeholders can learn from each other and are collectively better prepared for attacks (Bai, Gopal, Nunez, & Zhdanov, 2014) (Skopik, Settanni, & Fiedler, 2016) (Z-CERT, 2017)
The “detect and recover” phase is at the heart of the incident response cycle. Here the incident has occurred and already resulted in a crisis or has the potential to become one. Figure 4 shows a more detailed version of the Detect and Recover phase.
24 In the detect and recover phase the incident is detected. In case of ransomware access to certain systems or hardware is denied to employees and a ransomware message is displayed instead. Following the wheel, the employee will then alert the ones responsible for this type of irregularity and the recovery phase will start with an assessment. After, steps are taken to solve the problem and a communication strategy is put in place to make sure that the communication both internally and externally is streamlined.
Figure 5 shows the different steps of the learning phase. Here, information is gathered and
evaluated. The final steps of the phase include improvements and recommendations that are likely to form the fundament of the prepare phase to react more efficient and effective when another big ransomware attack occurs.
Figure 3, Figure 4 and Figure 5, showcase different red markings. These red rectangles mark the phases during a full circle of a ransomware attack where incident information disclosure is part of the process. During the phases that are marked in red, incident information disclosure and information disclosure balances play an important role and therefore must be considered when designing or constructing an incident response strategy.
Figure 4: A detailed picture of the detection and resolve phase (Jaatun, Albrechtsen, Line, Tondel, & Longva, 2009)
25 Incident information disclosure is a part of the whole IRMA wheel that represents a full computer security incident cycle. In the “prepare” phase, incident information disclosure can help other parts of the healthcare institution to prepare for similar events. Shared information can help other
healthcare institutions to prevent such an event from happening. In addition, some regulations about incident information disclosure must be implemented for when an incident occurs. In the “detect and recover” phase, incident information disclosure is part of the assessment where information is gathered and staff is informed about the incident. If the situation escalates, third parties who possess more experience and knowledge about ransomware incident response might be alerted and hired to resolve the situation more efficiently. Communication is an important part of the “detect and
recover” phase and the step where it is most easy to see how incident information disclosure is most effective. External communication is an important part of the communication strategy an must carefully be taken into account.
Finally, in the “learn” phase, the incident information disclosure is evaluated. Who was informed, were this the right people via the right medium and the right content? Was the incident information disclosure sufficient, effective and efficient? Can it be improved and how?
By looking at incident information disclosure, the whole incident cycle can be investigated. It
provides insight at both strategical and operational levels since it concerns both the strategical upper layer of an institution and the employees who are in charge of the operational part of an healthcare institution and its patients. Finally, by looking at disclosure, both the communication processes internally and externally can be taken into account during the ransomware attack, but also during the preparation and learning phases before and after an attack.
3.2
The academic discussion about incident information disclosure
This paragraph will provide an overview of the literature about incident information disclosure. It will be presented as a timeline to show the developments of research done in this field of expertise. Some gaps identified by the different authors will be identified and used as motivation behind the research done for this study.
An incident itself is not considered a crisis but has the potential to cause a crisis or crisis situation. A crisis can sometimes be the result of a cyber incident. Therefore, in literature there will be often referred to crisis, crisis situations and incidents. These terms are used in the context of the articles that be described and therefore the use of these terms might not seem consistent. The choice to stay close to the reviewed literature is made at the expense of the consistency in use of these closely related terms.
Organizational disclosure strategies have been given attention by scholars since the late 1980’s, when the scholar James Benson challenged his fellow academics to focus their research not only on crisis and what was disclosed about that crisis, but also on communication within crises. This challenge included developing a range of crisis response strategies for organizations to use during particular or specific crisis situations (Benson, 1998). In following years, scholars designed theories about what to disclose in which situation and for what reason.
26 incident information disclosure strategy, it is important to look at different and specific types of crises (Kaufmann, Kesner, & Hazen, 1994). They present a framework that can be of use while
designing an incident information disclosure strategy based on five questions assessing harm done by disclosure and non-disclosure.
Furthermore, researchers started to decompose the different aspects of disclosure to shine light on what incident information disclosure means for a company. Here, two main directions can be identified: One that focusses on incident information disclosure in the light of reputation, and one that focusses on the different types of people that organizations can disclose incident information to. Cormier and Magnan (1999) defined types of organizational information disclosure and try to find a correlation between different types of disclosure and their effect on the organization. They define three types of disclosure of non-crisis situations: Environmental impact information disclosure, social impact information disclosure, and financial information disclosure – noting that the latter is often required if the company is owned by external shareholders (Cormier & Magnan, 1999). The first two are often not required and Cormier and Magnan describe the disclosure of such information
therefore as ‘a strategic tool that provides economic benefits’ and with a positive impact on the firms value. Although Cormier and Manan (1999) describe information disclosure in non-crisis situation, they have opened the academic debate on the motivations behind corporate information disclosure. The academic literature on the motivations behind corporate information disclose largely focus on reputational management (Merkl-Davies & Brennan, 2007). This trend shows in both non-crisis situations studies and crisis studies (Coombs W. T., Crisis Communication and its Allied Fields, 2010). In his article, Coombs analyses different studies regarding motivations of incident information disclosure that have been done from the late 1990’s until 2007. He states that incidents threaten the reputation of an organisation and this threat influences how possible shareholders or customers approach the organisation. Coombs shows that scholars focus on how to deal with the public and which kind of strategies exist when dealing with incident information disclosure. Coombs also identifies a big gap in the current incident information disclosure. He states that most of the theories and frameworks that focus on how to preserve ones reputation during crises are not tested or validated. According to him, scholars must invest in validate these frameworks for it can be helpful prior to a crisis situation instead as an evaluating tool (Coombs W. T., Crisis Communication and its Allied Fields, 2010).
A second direction of information disclosure focusses on the public receiving the disclosed information. The main focus lies with different stakeholders and how they could be addressed. Solomon, Solomon, Norton and Joseph (2000) are the first to look at incident information disclosure towards internal stakeholders of a company instead of addressing the public, or external
stakeholders. They argue that the content of information disclosure internally and externally could be different, and also how and when information is shared via a chain of command. When looking at internal stakeholders, what is disclosed is therefore more important than how (Solomon, Solomon, Norton, & Joseph, 2000).
27 Their five-stage CERC model assumes that a crisis situation will develop itself in predicable ways, allowing crisis managers to anticipate on the crisis communications and stakeholder needs. Due to the predictability of the progression of most crisis situations, Reynolds and Seegers (2005) state that crisis communication must happen long before the crisis occurs and long after the immediate threat has subsided. The CERC model emphasises the responsibility of companies and governments to inform the public about risk in advance. This approach is founded within responsibility and will also make crisis communication easier when the event occurs.
In the second chapter of The Handbook of Crisis Communication, Coombs (2010) state that after 2005, the research on crisis communication diversified. Different researchers started to look at crisis communication and incident information disclosure from different fields, angles, and research methods. He calls this both a blessing and a curse, noting that this impressive growth in research ‘is ushering a renaissance in crisis communication’ and offers a variety of new insight. The curse lies in the idea that knowledge and insights are scattered across multiple journals, disciplines and hidden as parts in articles, making it very difficult to accumulate and integrate the different lessons and
obtained knowledge across different fields (Coombs W. T., Crisis and Allied Fields, 2010). Another argument that Coombs (2010) makes in this chapter is that crisis communication and incident information disclosure research focusses too much on case studies where the lessons learned are too specific and therefore do not contribute to the body of knowledge. According to him, crisis communication research must aim to be helpful before a crisis and not just afterwards (Coombs W. T., Crisis and Allied Fields, 2010).
However, there are some articles where these critiques do not apply. In 2012, Kulikova, Heil, Berg, & Pieters published an article about cyber incident information disclosure. In this article, they explain how they designed a framework for incident information disclosure after and during cyber-attacks that could help companies to design their disclosure strategy. The framework works on both a tactical and a strategic level, leaving room for both operational decisions as motivations behind certain choices (Kulikova, Heil, Berg, & Pieters, 2012).
28
3.3
Bringing incident information disclosure and healthcare together
Incident information disclosure is a balance of what to disclose and to whom (Kulikova, Heil, Berg, & Pieters, 2012). However, this is not the only aspects to be considered when looking at incident information disclosure. Looking at the healthcare industry, disclosure has been a part of the medical debate since the beginning of the profession (Lin & Clark, 1994). However, the healthcare industry developed, grew and different parts of information disclosure entered the domain. Information disclosure that concerns both the patient, and other stakeholders like governments, health insurance companies, the media, researchers, security companies, consultants and many more (Kruse,
Frederick, Jacobson, & Monticone, 2017). Information disclosure in the healthcare industry is therefore an issue of both patient data and privacy.
By dissolving the different aspects of information security, a clear demarcation can be made about the type of information security and therefore information disclosure will be taken into account in this study. It is argued that information disclosure is bigger than privacy and that incident
information disclosure issues - like privacy - are not necessarily to be taken into account. This argument will be supported by different authors who have looked at different levels of patient information and its digital security.
One of the first authors to write about the increased responsibility of the healthcare industry for their electronical patient data were Bishan Lin and Lawrence Clark in 1994. They argue that a rise in electronically stored patient information data contributes to the efficiency of the healthcare information systems, but bring potential implications for how hospitals secure their patient data. According to them, healthcare institutions must understand the importance of the security of their patient data and include questions of privacy, integrity, ownership, and impact in their security policies.
Discussing the problems and the questions they identified, Lin and Clark (1994) see two management issues regarding the safety and security of hospitals data; information control and security policy. Information control in healthcare information systems is dealing with questions on how to ensure that sharing any information happens on a controlled basis (Lin & Clark, 1994). Within the idea of controlled information accessibility and sharing, three control elements take a central position: accessibility, confidentiality, and integrity.
Accessibility means that end users - i.e. healthcare providers - can access the data they need, when they need it. Accessibility in itself has two components: access privilege and access restriction. Both determine who can and who cannot access someone’s patient data. Confidentiality entails the code that patient data can only be used in the best interest of the patient. Sharing of data must therefore be legally and regulatory supported. Integrity refers to the believe that patient data must be accurate and consistent. If patient data is stored electronically, all the information must be in the electronical dossier and only the healthcare providers who have required knowledge must be able to access and change that information (Lin & Clark, 1994).