A STRONG OFFENCE IS THE BEST
DEFENCE?
Russia’s strategy towards countering terrorism in the North Caucasus
11-08-2016
A STRONG OFFENCE IS THE BEST
DEFENCE?
Russia’s strategy towards countering terrorism in the North Caucasus
AUTHOR: FARSHID SYED KOUH KEIVANI
STUDENTNUMBER: S1751476
EDUCATIONAL INSITUTION: LEIDEN UNIVERSITY
MASTER: CRISIS AND SECURITY MANAGEMENT
THESIS SUPERVISOR: PROF. DR. M. DE HAAS
SECOND READER: PROF. DR. E. BAKKER
CASE: RUSSIAN FEDERATION
DATE: 11-08-2016
Table of Contents
Preface ... 1
Chapter 1: Introduction ... 2
1.1 Research area ... 2
Research question ... 3
Sub-questions ... 3
1.2 Relevance and the link to Crisis and Security Management ... 4
Academic relevance: ... 4
Societal Relevance: ... 5
1.3 Theoretical framework ... 6
Understanding Terrorism ... 6
Understanding Counterterrorism ... 8
The Framework of Hard and Soft Power ... 10
1.4 Research design ... 14
Methodology ... 14
Operationalization ... 17
1.5 Reading guide ... 20
Chapter 2: Internationally recognized practices ... 21
2.1 The context ... 21
2.2 UN Resolutions on Counterterrorism ... 22
2.3 Best practices in the Soft and Hard Power Framework ... 24
Chapter 3: Historical Characteristics of the North Caucasus ... 32
3.1 First Resistance Movements ... 32
3.2 Stalin’s Deportation Policy ... 34
3.3 Chechnya and the Call for Independence ... 35
3.4 The First Chechen War ... 36
3.5 The Second Chechen War and Aftermath ... 37
Chapter 4: Russia’s Counterterrorism Strategy ... 39
4.1 Legislation in the 1990s ... 39
4.2 Legislation in the 2000s ... 41
4.3 Counterterrorism Practices and Measures within the Hard and Soft power framework ... 46
Chapter 5: Differences and commonalities ... 49
Chapter 6: Conclusion and Discussion ... 51
Preface
Before you lies the thesis “A strong offence is the best defence? Russia’s strategy towards
countering terrorism in the North Caucasus”. It has been written to fulfill the master Crisis and
Security Management at Leiden University. This thesis is part of the Capstone Project,
supervised by Dr. Marcel de Haas, on the subject of “Terrorism in the North Caucasus”.
Terrorism is considered one of the greatest challenges facing the contemporary world. With the
recent attacks in Paris and Belgium it seems that this phenomenon has reached our doorstep. I
find it of paramount importance to understand the motives behind terrorist attacks and to
develop measures to counter it.
I have always been fascinated with Russia and her deep history, which goes back all the way to
the eighth century A.D.. From the early Slavic people that first settled Western Russia, to the
Russian Empire and beyond. My grandma is Polish and lived in communist Poland. She used
to spend whole evenings sitting on the couch telling me stories about her experiences with
communism and Russians.
With this thesis my student days will end as well. I am looking back on a period in my life in
which I have learned to think from different perspectives, reflect on myself and the world I live
in. I am thankful to have had this opportunity.
I would like to thank some people that sincerely helped improving the quality of this research.
I am grateful to my supervisor Dr. Marcel de Haas for his constructive critique and to Dr. Edwin
Bakker in his role of second reader. Furthermore, I would like to thank my girlfriend for her
ongoing support. And last but not least, thank you babcia for your inspiring stories.
I hope you enjoy reading this thesis.
Farshid Syed Kouh Keivani
Chapter 1: Introduction
1.1 Research area
The rise of the Islamic State (IS) in the Middle-East has put the phenomenon of terrorism high
on the political agenda of many United Nations (UN) member states. The Security Council of
the UN – which consists of fifteen members including China, France, Russian Federation, the
United Kingdom and the United States – has ‘unequivocally’ condemned IS and stated that the
extremist group poses an ‘unprecedented’ threat to international peace and security (Security
Council Unequivocally condemns ISIL, 2015). The representative of the Russian Federation
argued that this statement is “(…) a step towards the creation of a broad anti-terrorism front
aimed at eradicating the root causes [of terrorism]”. For Russia however the fight against
terrorism is not solely an external issue.
Internally the Russian Federation faces (Islamist) insurgency groups which concentrate
themselves in the North Caucasus region. Islam has been part of the local culture for centuries,
but – in the past decades – extremism has taken hold and transformed the conflict from primarily
a struggle for independence by the Chechen movement, into a movement rebelling against the
power of the ‘infidel state’ and seeking to create a Muslim state (Yarlykapov, 2010:152; Cohen,
2012:4). The North Caucasus insurgency is responsible for attacks on infrastructure, trains,
planes, theaters, and hospitals in the region but also in the rest of the country (Cohen, 2012:4).
Despite Russia’s hard-line approach to the terrorist threat coming from the North Caucasus, it
has struggled to defeat the sources of violence and has received a fair share of criticism from
both scholars and human rights monitors alike. (Pokalova, 2015:180; Human Rights Watch,
2016). They argue that the strong focus on repressive measures will likely aid the insurgency’s
ability to mobilize the population and further add to the instability of the region (Vatchagaev,
2016; Cohen, 2012:1, Pokalova, 2015:182; Laub, 2014). Although during the presidency of
Medvedev the government tried to address the underlying root causes such as poverty, political
and economic inequality, these activities have since been reversed with Putin’s return to the
Kremlin (Vatchagaev, 2016; Pokalova, 2015:182). The challenges for governance and stability
further increases with the growing influence of IS in the insurgency (Vatchagaev, 2016). The
Russian government is now faced with the outflow of Russian citizens to the Middle East in
order to join IS (Vatchagaev, 2016). The risk of these ‘battle hardened’ radicalized fighters
situation in the North Caucasus (Pokalova, 2015:182). The way in which Russia deals with
counter terrorism challenges is therefore vital for the (future) security and stability of the region
and needs to be examined. As Pokalova (2015:179) puts it: “(…) if Russia does not diversify its
counter terrorist approach and does not address the factors that push people toward terrorism
in the first place, it is probably likely to face a constantly evolving, adapting, and expanding
threat of terrorism”.
The purpose of this thesis is twofold: (1) to examine the counter terrorism strategy of the
Russian Federation, and (2) to compare this to internationally recognized counter terrorism
practices in order to develop recommendations. On a more general level, counter terrorism
policy refers to laws, legislation, regulation, public documents and social programs, while best
practices refer to “(…) a technique, an activity, a strategy, a methodology or approach that has
been shown, through application and evaluation, to be effective/and or efficient in achieving a
desired result” (Omelicheva, 2011:6; Report on Standards and Best Practices, 2006). In order
to better understand the counter terrorism strategy and associated interventions a further
distinction will be made between soft en hard power instruments with regards to combating (the
causes of) terrorism. This approach will serve as the foundation and framework of this research.
Research question
In order to fulfill the purpose of this research outlined above, the following research question
will be answered:
“What is the role of soft and hard power instruments in the counterterrorism strategy of the
Russian Federation with regards to combating terrorism in the North Caucasus and how do
these activities compare to internationally recognized counter terrorism practices?”
Sub-questions
In order to answer the research question, the following sub-questions have been formulated:
Theoretical sub-questions:
1. What is terrorism and counterterrorism?
2. What are soft and hard power instruments?
Empirical sub-questions:
1. Which internationally recognized counter terrorism practices can be identified and
2. What are the relevant (historical) characteristics of the North Caucasus?
3. What counterterrorism policy has Russia adopted in the North Caucasus?
4. What are the main differences and commonalities between the internationally
recognized practices and the Russian counterterrorism practices?
5. What recommendations can be made with regards to Russia’s counter terrorism
policy?
1.2 Relevance and the link to Crisis and Security Management
Academic relevance:The Russian government faces a number of significant challenges in the North Caucasus. These
include ethno-nationalist separatism, the drive for religious segregation and purification, and
discontent with poor socio-economic developments and political conditions (Pokalova,
2015:174; Laub, 2014). During the past decades these grievances have manifested themselves
in the phenomenon of terrorism and are linked with poor governance and security issues
(Pokalova, 2015:174). Within the field of public administration governance takes a central role
and can be defined as the organized efforts to manage the course of events in a social system
(Burris, Kempa and Shearing, 2008:9). This thesis explores Russia’s governance challenge
within the counterterrorism domain and delineates between soft and hard power instruments in
order to gain more insight into the action’s Russia has taken to counter (the causes of) terrorism
and conflict. The concepts of terrorism and counterterrorism play an important role within the
study of crisis and security management and will be used as the common thread of this thesis.
While there have been many academic publications on the subject of terrorism – which has
resulted in an extensive body of knowledge – literature on counterterrorism is significantly less
abundant (Quinlan, 2015:225). Additionally traditional frameworks for analyzing counter
terrorism campaigns – which structure the debates around a military (or war) model or a
criminal justice model – are predominant. The framework of hard and soft power in the domain
of counterterrorism is a relatively new phenomenon and does not only include offensive hard
power tactics - such as increased policing and military operations – but also focuses on
population centric methods that target the root causes of terrorism at the societal level, including
capacity building, economic development and counter-radicalization efforts (Rineheart, 2010).
Also, many studies regarding counterterrorism practices which focus on the hard and soft power
approach mostly pertain to the United States and several European countries (Aly, Balbi and
Jacques, 2015:6-7). This thesis will build on this body of knowledge by focusing on the case of
recognized practices. Furthermore, this thesis aims to contribute to the existing literature on
counter terrorism practices by analyzing and characterizing the Russian Federation’s counter
terrorism policy through the framework of the soft and hard power approach.
Societal Relevance:
The widespread phenomenon of terrorism in the North Caucasus has led to a multitude of
violent attacks on – among others – infrastructure, citizens and law enforcement agencies.
However, terrorism as an instrument does not solely focus on inflicting physical and material
damage, but rather seeks to spread fear within society in order to intimidate and to achieve
certain political goals (Bakker and de Graaf, 2014:2). This anxiety and fear can have a negative
impact on society by causing “a shift towards dogmatic reasoning which is characterized by ‘us versus them’ thinking, stereotyping, discrimination and a lack of nuance that contributes to
harsh, system defending reactions that might do more harm than they do good” (Bakker and
Veldhuis, 2012:4). An example of this can already be observed in Russia where ethnic Russians
have adopted the term of Kavkazofobiya (fear of the Caucasus) resulting in the popular Russian
sentiment that North Caucasians are crazed and fanatical terrorists that are suspicious,
dangerous and unwanted (Foxall, 2015:4-5). This partly stems from the perception that the
North Caucasus Republics are implicated (proximately or otherwise) in the gravest of national
crises that Russia has faced since the collapse of the Soviet Union (Foxall, 2015:5). This ‘us
versus them’ thinking can cause rising tensions within society, polarization and radicalisation
and overlooks the fact that North Caucasians are Russian citizens that possess the same legal
rights as all other citizens under the Russian Constitution. On a societal level it is therefore
necessary to limit these negative consequences of terrorist actions. Societies are, however,
unlikely to completely eliminate terrorism. As Lesser, Arquilla and Hoffman (1999:126) have
argued “terrorist risks cannot be eliminated, only contained and managed”. This notion calls
for good governance that is linked to a comprehensive counterterrorism strategy. By analyzing
the Russian Federation’s counterterrorism approach and by comparing it to internationally
recognized practices, this thesis aims to raise awareness among Russian policymakers on
alternative practices within the counterterrorism domain. On a political level this knowledge
gives insight into how policy makers can improve policies geared towards countering terrorism
by putting developed measures into perspective. Additionally, this knowledge can be of added
value to other policy makers who want to understand the different ways in which governments
1.3 Theoretical framework
In this section the theoretical background of this study will be outlined, specifically explaining
the framework of the hard and soft power approach within the counterterrorism domain. This
theoretical framework will be derived from related concepts. First, ‘hard power’ and ‘soft
power’ has to be defined, but this in turn calls for a definition of ‘terrorism’ and ‘counterterrorism’ itself. Therefore, these concepts will be elucidated in the following
subsections of this chapter.
Understanding Terrorism
“Tell me what you think about terrorism, and I tell you who you are”
-J. Bowyer Bell, MIT historian (1989)
Terrorism studies has been an active field of research since the late 1960s and has inspired
debates across many academic disciplines, including political science, sociology, law, and
psychology (Sandler, 2014:257). The search for a universal definition of terrorism by academics
has proven to be greatly problematic. There are now over 200 definitions in existence within
the terrorism studies literature and in practice (Jackson, 2015:488). Schmid (2004:384,395)
argues that the lack of a clearly definable general use of the term can be attributed to four main
reasons. The first reason pertains to the contested nature of the concept. Within academia
terrorism is known as an essentially contested concept for which there is no generally accepted
definition (Schmid, 2004:384). This lack of consensus on what constitutes terrorism can be
linked to the subjective and political sensitive nature of the concept, and can perhaps be best
empitomised by the phrase that “One person’s terrorist is another person’s freedom fighter”
(Golder and Williams, 2004:272). This means that what is considered a terrorist act is not an
independently verifiable fact, but an interpretation that changes over time, place and observer
(Jackson, 2015:488). As Schmid en Jongman (1988:101) put it: “The nature of terrorism is not
inherent in the violent act itself. One and the same act (...) can be terrorist or not, depending
on intention and circumstance”. The second reason for why terrorism is contested pertains to
the notion that the definition question is linked to (de-)legitimization and criminalization
(Schmid, 2004:396). Terrorism is a pejorative term that – when used as a label for certain acts
of political violence – can reflect negatively on actors, de-legitimizing or criminalizing their
conduct. This stigmatization hinders any meaningful debate with or about the actors that carry
madness, the application of terrorist shuts the door to discussion about the stigmatized group
or with them, while reinforcing the righteousness of the labelers, justifying their agendas and
mobilizing their responses”. The third reason pertains to the many forms and manifestations of
terrorism that exist (Schmid, 2004:396). The distinction is mostly based on ideology and
includes left- and right- wing terrorism, religious inspired terrorism, ethno-nationalist and
separatist terrorism, and single-issue terrorism. All these different categories make it
problematic to develop a universally agreed upon definition. Furthermore, the type of terrorism
that will dominate the socio-political discourse within a certain country depends on the part of
the world one lives in and – given the selectivity of our perceptions – tends to shape one’s
perception of all other forms of terrorism (Schmid, 2004:396). The last reason has to do with
the changes in meaning of terrorism over the course of more than 200 years of its existence.
The semantic focus of the term has shifted numerous times. This makes any definition – fixed
in time – problematic (Schmid, 2004:397). First described as the ‘reign of terror’ by the
authorities after the French Revolution, the term ‘terrorist’ was not used in an anti-government
sense until late 19th century. The reasons outlined above make clear that the way in which the
concept of terrorism has to be understood is by looking at how it has been discursively
constructed through language and social practices (Jackson, 2015:488). This idea of social
construction is therefore important when considering different definitions of terrorism.
Terrorism exists in the eye of the beholder and if and how actors apply the label depends on
who they are and what their purpose is.
Although developing a precise definition of terrorism is problematic, it is nonetheless desirable
to have a certain degree of conceptual clarity, were it only that an unclear concept can lead to
academics talking past each other and policy makers developing policies based on displaced
ideas. Throughout the years numerous attempts have been made to reach an academic consensus
definition (Schmid, 2011:73). From these attempts certain main components of the concept of
terrorism can be identified. Firstly, terrorism is described as an instrument or tactic to achieve
certain goals that can be – among others – religious, nationalist or reactionary in nature
(Schmid, 2011:76). Other important components are the use of force and the spreading of fear.
The victims of violence are not the primary targets. Terrorist violence is usually aimed at a
wider target audience in order to generate power in political conflict (Schmid, 2011:76). In
sum terrorism is a politically motivated tactic that involves the threat or use of force or violence
in which the pursuit of publicity and the spreading of fear plays a significant role (Schmid,
In practice it is just as problematic to reach an (international) political and legal consensus of
what constitutes terrorism (Schmid, 2011:85). As a result every country defines terrorism in a
different way, due to context specific complexities and threats. Most importantly, due to the
lack of any outer legal boundaries set on the international level, states adopt definitions of
terrorism unilaterally (Kuznetcov and Kuznetcov, 2013:132). This is no different in the Russian
Federation which is predominantly faced with domestic terrorism that has its roots in the North
Caucasus region. Different authors have argued that the North Caucasus is the biggest security
concern to the Russian Federation since the collapse of Soviet Union (Thumann, 2001:194). It
has been plagued with a rise of violence that has been linked with separatism and with the global
jihadist movement. It is not surprising, therefore, that the terrorist threat for Russia emanates
from this region.
Understanding Counterterrorism
The phenomena of terrorism and counterterrorism are strongly intertwined. After all, a
successful counterterrorism approach demands an understanding of the factors that make
terrorism possible (Law, 2009:7). Schmid (2011:29) draws an interesting analogy in which the
author calls counterterrorism the cure to the disease of terrorism. Although the phenomenon of
terrorism cannot be completely eliminated, steps can be taken to disrupt, dismantle and defeat
organizations that use terrorism (Rineheart, 2010). In the abstract counterterrorism is about
devising methods to limit the actions of terrorist groups and to cause these groups to stop using
violence to achieve their political objectives (Eijkman and Schuurman, 2011:2; Omelicheva,
2007). However, as is the case with the concept of terrorism, counterterrorism is a complex and
multifaceted subject that does not lend itself to being readily defined and is – as a result – not a
formula for guaranteed success (Eijkman and Schuurman, 2011:2). Although difficult to define
it is nonetheless a prerequisite to a methodical examination of governments’ responses to give
at least a definition of the respective conceptual requirements for counterterrorism
(Omelicheva, 2007).
There are a considerable amount of approaches to engaging with terrorism (Schmid, 2011:190).
These approaches have been divided into different categories such as anti-terrorism,
counterterrorism, terrorism consequence management, responding to terrorism, coercive
counter terrorism and discouraging terrorism (Schmid, 2011:190). Prior to the response of the
terrorism – mostly conceptualized as pre-emptive or proactive, while anti-terrorism was seen
as a more reactive engagement with terrorism. Since then – Schmid (2011:190) argues –
counterterrorism has ‘won over’ anti-terrorism and is now used to include a broad variety of
responses to terrorism, both proactive/offensive and reactive/defensive.
A proactive or offensive approach targets terrorists, their resources, or their supporters directly
in order to weaken the operational capabilities of terrorists and to inhibit terrorist attacks
(Sandler, 2014:13). The focus lies on actively preventing, deterring and combatting terrorism
and on reducing terrorist incidents (Schmid, 2011:620). These measures – among others – can
consist of engaging in military action (for example operations by the host government against
the resident terrorist group), assassinating terrorist leaders, freezing terrorist assets, preventive
detention, counter-radicalisation, surveillance and retaliating against a state-sponsor. Reactive
or defensive measures on the other hand try to protect potential targets against attacks or try to
ameliorate the damage or restore order in case of an attack (Sandler, 2014:13). These kind of
measures are usually instituted after a ‘successful’ or ‘innovative’ terrorist attack and may
involve – among others – deployment of security personnel, installation of technological
barriers (for example bomb-sniffing-devices, metal detectors), stiffer penalties for terrorism
offenses, and the hardening of targets (for example defensive perimeters around government
buildings). Thus, counterterrorism can envelop a range of responses across several government
departments, and can span across a wide range of domains, including politics, economic and
social, psychological-communication-educational, military, judicial and legal, police and
prison system, and intelligence and secret services (Schmid, 2011:190). At a policy level
counterterrorism can therefore potentially encompass a host of different strategies for dealing
with terrorism (Eijkman and Schuurman, 2011:2). However, the strategies adopted will vary
among countries as counterterrorism policies are subject to change according to the nature of
the terrorism threat (Rineheart, 2010).
As was stated before a terrorist act is not an independently verifiable fact, but an interpretation
that changes over time, place and observer. As such, policy prescriptions for addressing threats
that emanate from terrorist organizations will differ according to political context, the current
threat environment, and the government implementing the counterterrorism measures
(Rineheart, 2010). Due to the complexities that surround counterterrorism there is no formula
for guaranteed success when developing and executing a strategy. This is reflected by the
disastrous attacks throughout Russia and the North Caucasus which have resulted in a high
Moscow theatre siege in 2002, the Beslan school hostage taking in 2004, the Nalchik bombing
in 2005, the Moscow metro bombing in 2010, the Moscow Domodedovo Airport bombing in
2011 and the Volgograd bombing in 2013 (Yemelianova, 2014:8). The ability to learn from
past crises is therefore important in the counterterrorism domain. Additionally, Russia can
potentially learn from experiences of other states in the domain of counterterrorism. Lessons
learned in counterterrorism policies and practices in different countries can offer valuable
insights to those officials responsible for setting policy for the North Caucasus (Forest, 2007:1).
After all, a comparative perspective can lead to a clearer understanding of the complex world
of (counter-) terrorism and the place each actor takes within it (Forest, 2007:1).
The Framework of Hard and Soft Power
In the (counter-) terrorism literature a number of frameworks have been developed in order to
organize the wide range of states’ responses to terrorism (Omelicheva, 2007). An analytical
distinction can be made between multiple paradigms that give insight into counterterrorism.
Although this thesis focuses on the framework of hard and soft power, it is important to
acknowledge the other models that exist. It has been common – for example – to classify states’
responses to terrorism within the military (or war) model or a criminal justice model
(Omelicheva, 2007). In the former, the military is primarily responsible for dealing with the
terrorist threat and developing counterterrorism strategy accordingly (Rineheart, 2010). The
engagement with terrorism is seen in terms of an enemy-centric war in which terrorists need to
be ‘eliminated’. In the latter, the police is afforded the means to subdue terrorist actions
(Omelicheva, 2007). Terrorism is regarded as a criminal act, where perpetrators are arrested
and punished in accordance to the rule of law. In this model emphasis is placed on the criminal
nature of the act of terrorism and not on the political or ideological motive (Crelinsten, 2014).
Furthermore, what both these models have in common is their coercive approach, which relies
on the state’s monopoly on the use of violence (the exercise of hard power) (Crelinsten, 2014).
Additionally, models exist that adopt a more conciliatory approach, which is focused on
prevention and aims to reduce terrorism’s appeal (Schmid, 2011:190,616). Conciliation may
consist of measures aimed at accommodation (persuading terrorists) or addressing the
underlying conditions of terrorist violence (Schmid, 2011:616; Crelinsten, 2014). Models that
have been derived from this softer approach include – among others – the communication model
and the defensive model. In the communication model counterterrorism is seen as a form of
communication, where the emphasis is placed on the different kinds of messages, audiences
2014). In the defensive model terrorism is seen as a physical threat and measures are aimed at
protecting targets by – for example – target hardening (making potential targets less attractive
or more difficult to attack) (Crelinsten, 2014). A conciliatory approach – which focuses on
prevention and aims to reduce terrorism’s appeal – has played a relatively minor role in Russia’s
counterterrorism policy, while coercive measures have been applied more frequently
(Omelicheva, 2011). Nevertheless, some authors – including Pokalova (2014:180) – have
identified certain elements that stem from a more conciliatory approach, for example engaging
with opposition groups in the North Caucasus. It is therefore important to look at both the
coercive as the conciliatory approach when looking at Russia’s counterterrorism policy in the
North Caucasus.
A framework that has incorporated both these approaches, draws on the distinction between
‘hard power’ and ‘soft power’ and has been popularized by Joseph Nye (2004; 2009; 2011).
Both concepts originate from the field of International Relations, where power plays a central
role and is described as “(…) one’s ability to affect the behavior of others to get what one wants”
(Nye, 2009:160). Although, commonly used to gain insight into foreign policy, this framework
is equally applicable to domestic counterterrorism as this concept blurs the distinction between
foreign and domestic policy dimensions (Omelicheva, 2007). Nye (2009:160) argues that
exerting power can be done either through coercion or through attraction. The former is linked
to offensive hard power instruments and emanates from hard resources such as the use of force
or money. While the latter pertains to soft power measures which concern co-optive means of
framing the agenda, persuading, and eliciting positive attraction in order to obtain preferred
outcomes.
Hard power includes using military force, legal-repressive means, and economic measures. The
military component pertains to military resources and aims to (1) produce preferred behavioral
changes in targets through physically fighting and destroying the enemy; (2) by threatening in
coercive diplomacy; (3) by protecting; (4) or by providing different forms of assistance to allies
(Nye, 2011:34-35). The first aspect pertains to physical coercion through the use of military
force. This takes the form of a deployment of military personnel with the mandate to use force.
The second aspect pertains to the threat of military coercion and takes the form of a warning
issued by an agent towards a target, with regards to a deployment of military personnel with the
mandate to use force. The third aspect revolves around physical protection and takes the form
of a deployment of military personnel with the mandate to protect civilians, critical
This aspect takes the form of a deployment of military personnel with the mandate to train other
agents in order to engage with targets.
Furthermore, the legal-repressive component refers to policing and the development of a regime
of laws to coerce the behavior of targets (Omelicheva, 2007). This can take the form of an
existing set of laws that criminalizes – for example – violent extremism. Additionally, policing
refers to raids and arrests made by law enforcement agencies.
The economic component focuses on getting desired outcome through payment and consists of
a financial incentives aspect and economic sanctions aspects (Nye, 2011:19). The financial
incentives aspect takes the form of payment or economic inducement between agents and
targets or agents and other agents in order to get those actors to do what they initially did not
want to do. Economic sanctions take the form of issuing warnings to take money away from
targets or other agents or depriving a target or other agent of funds. Although payments may
seem more attractive to an actor, it can be turned into a negative sanction by the implicit or
explicit threat of its removal (Nye, 2011:19).
Nye (2011:23) defines soft power as: “(…) the ability to affect others through the co-optive
means of framing the agenda, persuading, and eliciting positive attraction in order to obtain
preferred outcomes”. Soft power is therefore not only about exerting influence and it is more
than just persuasion or the ability to move people by argument (Nye, 2004:20). It is also about
the ability to attract, with the aim of drawing attention and persuading an actor – by appealing
to shared values and culture – to go along with one’s purposes without any explicit threat. Soft
power resources are assets that produce this attraction. Attraction refers to drawing positive or
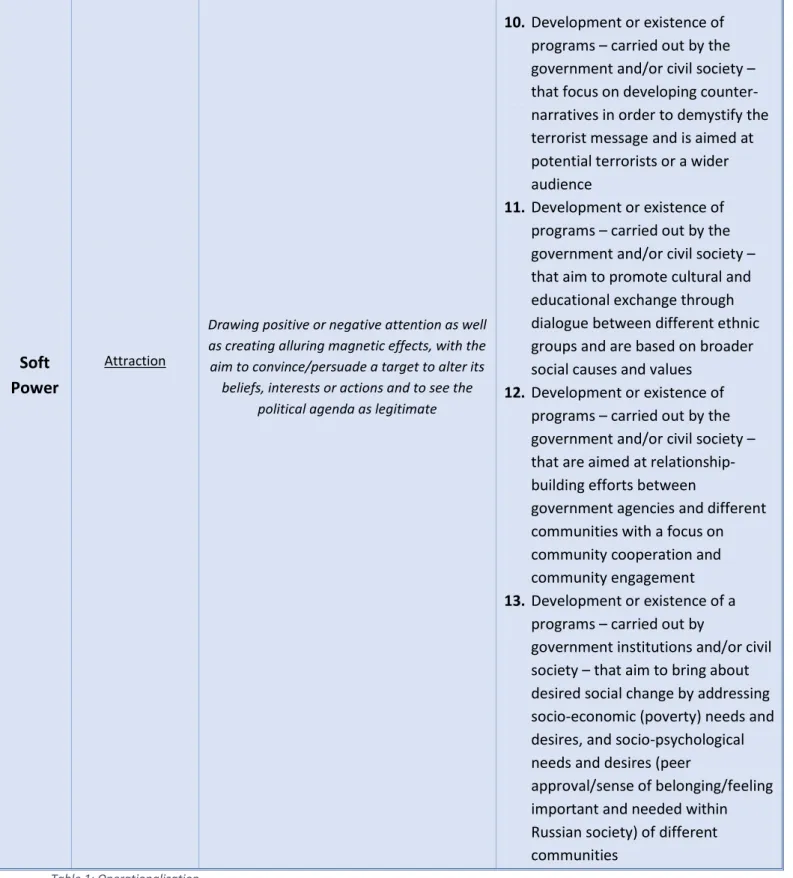
negative attention as well as creating alluring magnetic effects. The aim is to convince/persuade
a target to alter its beliefs, interests or actions and to see the political agenda as legitimate. Soft
power relies on three resources, namely culture (when values and interests have a widespread
appeal and are understood and shared by others), values (when they are attractive and morally
good), and policies (when they are seen as inclusive, legitimate and provide public goods rather
than being self-serving) (Nye, 2009:161). These types of resources – that are associated with
soft power – are often intangible factors, while resources associated with hard power include
tangibles such as the use of force and money (Nye, 2009:161). Additionally, within the soft
power approach public diplomacy plays an important role, which is directed towards civil
society. Soft power is therefore not only accessible to governments, but can also be employed
Balbi and Jacques, 2015:5). Civil society can play a critical role within the counterterrorism
domain (Rosand, 2008:5). It gives marginalized and vulnerable people a voice and provides an
outlet for grievances. Although Nye’s discussion is conducted in the context of United States
foreign policy, the analytical distinction of soft and hard power is equally applicable to other
countries and in different domains (Nye, 2011:13; Aly, Balbi and Jacques, 2015:5). In the
domain of (counter-) terrorism different measures can be categorized under the soft power
umbrella (Aly, Balbi and Jacques, 2015:5). Soft counterterrorism is proactive and pertains to
preventive measures that attempt to address the conditions conducive to the spread of terrorism
(root causes and support for terrorism) (Eijkman and Schuurman, 2011:2). Countering violent
extremism has been – more recently – incorporated into soft power approach, which
encompasses measures as varied as de-radicalisation programmes, educational programmes,
community empowerment and the development of counter-narratives (Aly, Balbi and Jacques,
2015:5). Further examples of the soft power approach can be diplomacy, negotiation, and social
reform (Omelicheva, 2007). These kind of measures either directly or indirectly improve
relations between actors or bring about desired social change. Hence, these measures can take
the form of different kind of programs carried out by government institutions and/or civil
society that aim to address the spread of violent extremism by – for example – counter
narratives, aim to promote cultural and educational exchange through communication, are
aimed at relationship-building efforts between agent and target, and aim to bring about desired
social change by addressing the needs and desires of those susceptible to violent extremism.
The distinction between hard and soft power is illustrated by Nye (2004:21) by using a
power-spectrum, which goes from tangible power of coercion at one end to the intangible power of
attraction on the other end:
Figure 1: Power-spectrum (Nye, 2004:21)
It is important to note that hard and soft power are not two entirely distinct forms of power.
There is no clear demarcation. Both can overlap, with soft instruments that can be used in hard
power – the behavior of protecting and providing assistance to allies can engender soft power
(Nye, 2011:26).
Incorporating soft power into a government strategy can be difficult for three reasons. The first
one pertains to the notion that success – in terms of outcomes – is more in the control of the
target than is often the case with hard power (Nye, 2011:55). Secondly, soft power is a long
term investment, and politicians are impatient to see a prompt return on their investments.
Thirdly, soft power instruments are not fully under control of the government, due to culture
and values being imbedded in civil society (Nye, 2011:55). Nye also coined the term smart
power in which soft and hard power are combined into one strategy (Nye, 2011:24). As Nye
(2011:11) puts it: “Smart power is the combination of the hard power of coercion and payment
with the soft power of persuasion and attraction”. In practice and academics there seems to be
the recognition of the need to incorporate a multifaceted approach that combines hard and soft
instruments into a single framework (Aly, Balbi and Jacques, 2015:5). By applying smart power
governments can consider more contexts in which terrorism arises, such as social, economic,
political and historical contexts. Combining the full range of power resources effectively can
be difficult (Nye, 2011:25). As was stated before hard and soft power sometimes reinforce and
sometimes undercut each other and a good contextual understanding is needed in order to
distinguish how these concepts interact in different situations.
1.4 Research design
This section discusses the methodology that will be used for this research and explains how it
will guide data collection, data exploitation and data assessment. The type of research and the
data collection methods will be described, paying special attention to the validity and reliability
of the study. Afterwards, the concepts discussed in chapter 1.3 (theoretical framework) will be
operationalized, by developing indicators that measure these concepts within the empirical
setting.
Methodology
Answering the research question is difficult due to (counter-) terrorism being a social construct,
which is defined within a particular historical-cultural context and shaped by the assumptions
embedded within it. It is therefore important to be mindful of the context of terrorism within
the Russian Federation and more specifically the North Caucasus region. Although (counter)
terrorism is both a global and a nationwide phenomenon and while comparisons will be made
research to analyze and make statements about (counter-) terrorism on a global and national
level. Terrorist activities in the Russian Federation are most common in North Caucasus region,
and hence the primary focus of this research. The single case study design has therefore been
chosen to examine Russia’s counterterrorism policy in this region. A case study makes it
possible to conduct a thorough and in-depth exploration of Russia’s counterterrorism policy
and provides detailed answers. Additionally, - due to the case study method and (counter-)
terrorism being a context specific phenomenon - the findings of this research will be difficult
to generalize to any broader level. This will impact the external validity negatively. However,
this is somewhat mitigated by limiting the aim of this research to only making statements that
concern the main unit of analysis namely Russia and within that context the Northern Caucasus.
Hence, the case study is the most effective and compatible method of research for this thesis.
This research will make use of content analysis as well as discourse analysis. Content analysis
will be applied to analyze laws, legislation, regulation, public documents, and social programs
that the Russian Federation has developed in order to counter terrorism in the North Caucasus.
Additionally, policy documents issued by the Counter-Terrorism Committee Executive
Directorate (CTED) of the UN – concerning internationally recognized counterterrorism
measures – will be analyzed. By using content analysis data can be organized into major themes
and numerical comparisons among and within documents can be made, for example the
relationship of two or more statements within a set of documents can be analyzed and
statements from two or more different sources can be compared (“Content Analysis: A Methodology”, 1981:9). This makes it possible to identify and subsequently categorize and
compare the counterterrorism measures in terms of hard and soft power instruments.
Furthermore, alongside these official documents, other sources will be used such as news
releases, newspapers, books and journal articles. This will not only give better insight into
counterterrorism measures employed by the Russian government, but will also provide relevant
historical insights with regard to terrorism in the North Caucasus. An important advantage of
content analysis its concern with being objective and systematic (Hardy, Harley and Philips,
2004:20). Analytical categories are defined so precisely that other researchers can confirm or
corroborate the results, which has a positive influence on reliability. An important disadvantage
of content analysis is that it often disregards the contextual meaning of a document, due to it
being a study of the text and not if its relation to its context or the intentions of the producer of
the text (Hardy, Harley and Philips, 2004:20). In order to provide this broader context for
Discourse analysis focuses on the relation between text and context and is a useful tool for
studying the political meanings that inform written en spoken text (Hardy, Harley and Philips,
2004:20). It does not only look at the basic level of what is said, but also takes the social and
historical context into consideration. In this thesis special attention will therefore be paid to the
use of rhetoric by Russian politicians and policymakers in key positions of government, such
as the President. Language used by these actors shapes the response to terrorism in the North
Caucasus. In this way the intentions behind a policy or speech – with regard to hard and soft
power measures – can be investigated, while taking into account the surrounding social and
historical context of the region. It is important to note that discourse analysis is an exercise in
creative interpretation by the researcher that seeks to show how reality is constructed through
texts and is therefore subject to dispute, which can be problematic with regards to reliability
(Hardy, Harley and Philips, 2004:22). By using content analysis in combination with discourse
analysis this issue can – to some extent – be mitigated due to the objective and systematic nature
of content analysis. However, for content analysis to be compatible with discourse analysis it
is necessary to weaken the assumption that meaning is stable enough to be counted in an
objective sense (Hardy, Harley and Philips, 2004:20). When using content analysis within a
discourse analytic approach categories emerge from the data, with theoretical work providing
ideas – which can be found in the operationalization part of this thesis – for what to look for
and the research question providing the initial frame (Hardy, Harley and Philips, 2004:21).
Hence, applying both content and discourse analysis helps to deal with the full complexities
that surround counterterrorism and makes it possible to obtain a more comprehensive
explanation, which in turn has a positive effect on the internal validity of this research. Lastly,
two other limitations are important to note. Firstly, this research will not make use of
participants for interviews or questionnaires due to a lack of contacts with high ranking public
officials in the Russian government, the physical distance and the relative small scope of this
research. It will therefore be difficult to check if the findings of this research are agreeable. The
final limitation is the absence of Russian language sources, which is due to the researcher’s lack
of Russian language skills. Wherever possible Russian sources that have been translated into
English will be used. Although not ideal – due to the inevitability of translation loss – it is still
Operationalization
As was stated in the previous sections counterterrorism encompasses a range of actions,
decisions and general guidelines, observable behaviors of states and verbal pronouncements of
political leaders. In this thesis the framework of hard and soft power serves as the analytical
tool to organize the range of responses of the Russian government to terrorism in the Northern
Caucasus region. Furthermore, it can be used to classify the internationally recognized
practices in the counterterrorism domain and makes a comparison with the practices employed
by Russia possible. In order to identify hard and soft power measures within the Russian
counterterrorism policy this thesis will use the following indicators (see table, column
Theory Concept Definition Indicator(s)
Hard Power
Military force (instruments)
The ability to physically coerce with military; to threaten with military coercion; to physically protect with military; and to
provide military assistance
1. Deployment of military personnel with the mandate to use force
2. Warnings issued by the government towards potential terrorists with regards to the deployment of military personnel with the mandate to use force
3. Deployment of military personnel with the mandate to protect civilians, critical infrastructure, and federal/local government
institutions
4. Deployment of military personnel with the mandate to train other federal/local/private security personnel in order to engage with potential terrorists
Legal-Repressive power (instruments)
Policing and the development of a regime of laws to coerce behavior of targets
5. The development or existence of laws that criminalizes terrorism
6. Raids and arrests by law enforcement agencies
Economic power (instruments)
Getting desired outcome through financial incentives and economic sanctions
7. The use of payments between the government and potential terrorist groups or local/federal authorities in order to curb terrorism
8. Issuing warnings to deprive potential terrorist groups or local/federal agencies of funds in order to curb terrorism
Table 1: Operationalization Soft
Power
Attraction
Drawing positive or negative attention as well as creating alluring magnetic effects, with the aim to convince/persuade a target to alter its beliefs, interests or actions and to see the
political agenda as legitimate
10. Development or existence of programs – carried out by the government and/or civil society – that focus on developing counter-narratives in order to demystify the terrorist message and is aimed at potential terrorists or a wider audience
11. Development or existence of programs – carried out by the government and/or civil society – that aim to promote cultural and educational exchange through dialogue between different ethnic groups and are based on broader social causes and values
12. Development or existence of programs – carried out by the government and/or civil society – that are aimed at relationship-building efforts between
government agencies and different communities with a focus on community cooperation and community engagement
13. Development or existence of a programs – carried out by
government institutions and/or civil society – that aim to bring about desired social change by addressing socio-economic (poverty) needs and desires, and socio-psychological needs and desires (peer
1.5 Reading guide
This thesis consist of six chapters that are divided into a number of sections and proceeds as
follows. The first section of Chapter 1 provided a general introduction to the thesis by outlining
the background of the subject, by formulating the research question and by stating the academic
and societal relevance of this research. The section that followed focused on the theoretical
background of this study, explaining the framework of the hard and soft power approach which
will be used to analyze and characterize the counterterrorism policy of the Russian Federation
and internationally recognized counterterrorism practices. Afterwards, the methodology used
for this research was discussed. To this end data collection, data exploitation and data
assessment were explained. This further helped guide the research process towards answering
the research question. Additionally, the concepts of hard power and soft power have been
operationalized and can now be used as an interpretative framework for the empirical part of
this research.
The subsequent chapters will cover the empirical part of the thesis by highlighting research
findings and by analyzing the data. Chapter 2 gives an overview of the internationally
recognized counterterrorism practices by outlining practices which have been compiled by the
UN’s Counter Terrorism Committee (CTC) and Counter-Terrorism Committee Executive
Directorate (CTED). This chapter concludes by categorizing the instruments identified within
the soft and hard power framework. Chapter 3 will describe the relevant (historical)
characteristics of the North Caucasus in relation to the (causes) of terrorism and focusing on
the role that nationalism and religion have played. Chapter 4 will look at the actual definition
of terrorism and counterterrorism used by the Russian Federation and provide an overview and
analysis of the legislation, laws and regulations, policy documents, social programs that have
been developed the collapse of the Soviet Union. This will result in a list of soft power and hard
power measures that the Russian government has deployed in the North Caucasus region
throughout the years. Chapter 5 will compare the Russian practices with the internationally
recognized practices in order to identify the main commonalities and differences. This chapter
will conclude with a number of recommendations which can be made with regards to Russia’s
counterterrorism policy. Finally, Chapter 6 will report the conclusion and discussion. The
conclusion will relate directly to the research question and will be substantiated by the empirical
and analytical insights gained from the previous chapters. The discussion will contain
Chapter 2: Internationally recognized practices
This chapter provides an overview of the internationally recognized counterterrorism practices
by outlining practices which have been compiled by the Counter Terrorism Committee (CTC)
and Counter-Terrorism Committee Executive Directorate (CTED) of the UN. The observations
made in this chapter will serve as the basis for categorizing these practices within the hard and
soft power framework. The categorization of practices will take place at the end of this chapter.
2.1 The context
The UN places great importance on its objective of maintaining peace and security in the world
by addressing global threats, including terrorism (Setty, 2011:10-11). As an intergovernmental
organization that consists of 193 member states, it strives to harmonize the efforts of different
countries so that common objectives can be attained. It was due to this harmonization that the
international community attempted to establish an internationally accepted definition of
terrorism multiple times. However, due to the sensitive political nature of the term and the
perceived subjectivity of the definition, certain elements of a proposed definition were rejected
by various nations whose interests were not served (Setty, 2011:9). It is therefore that the UN
has refrained from giving an exact definition of what constitutes terrorism, nor do they try to
identify specific terrorist groups. After all – as was stated in the theoretical framework – what
constitutes as terrorism or terrorist groups depends on the country defining it and the regional
context. As a result, countries are free to develop their own laws and practices to counter
terrorism within the UN’s counterterrorism framework. However, after the terrorist attacks in
the United States on September 11, 2001, the UN tried to harmonize these efforts by adopting
resolutions with a binding character. Although countries are still free to implement their own
laws and practices, they must adhere to certain terms within these post 9/11 resolutions.
However, according to Rosand (2004) this can still lead to a situation were “(…) a state is not
prosecuting an individual or group for acts that the majority of countries (…) believe are
terrorist acts, but that the country in question does not”.
Before continuing it is important to clarify what constitutes an internationally recognized
practice. In the context of this thesis an internationally recognized practice refers to statements
of a generally accepted approach by several nations that has been shown to be effective in
achieving a desired result (Report on Standards and Best Practices, 2006:III). In this regard the
UN multilateral system, with 193 member states, serves as an appropriate source for identifying
community. Additionally, the UN has focused extensively on developing measures concerning
countering terrorism since 9/11 attacks in the United States. The Counter-Terrorism Committee
Executive Directorate (CTED) of the UN assists the Counter-Terrorism Committee (CTC) with
bolstering the ability of member states to prevent terrorist acts both within their borders and
across regions (Our Mandate, 2016). One of the areas that the CTED and CTC focus on is
encouraging “(…) countries to apply known best practices, codes and standards, taking into
account their own circumstances and needs” (Our Mandate, 2016). Under Chapter VII of the
UN Charter the Security Council has the power to make binding recommendations, decide upon
measures with respect to threats to peace and security and can enforce these measures on
member states (Article 39 of the Charter of the United Nations, 1945:18). Therefore, resolutions
adopted by the Security Council can be seen as a “generally accepted approach by several
nations” when looking at best practices. The resolutions discussed in this chapter provide a
blueprint for UN best practices on countering terrorism and are therefore important to discuss
when looking at best practices.
2.2 UN Resolutions on Counterterrorism
Resolution 1373 was the first binding resolution of the UN Security Council and was
unanimously adopted on September 28, 2001 (Rosand, 2004:546). Rosand (2004:546) argues
that this resolution is the cornerstone of the UN’s efforts in countering terrorism due to the
change of focus from specific acts of terrorism – in the context of state-sponsored terrorism –
to the global terrorist threat posed, not by states, but by non-state terrorists and terrorist groups.
Additionally, this resolution imposed a series of obligations, requiring states to take various
measures to enhance their capacity to combat terrorism (Rosand, 2004:547). This obligatory
character of the terms within the resolution can be illustrated by the mandatory language used
in the beginning of the text: “The Security Council (…) decides that all states shall”
(S/Res/1373, 2001). The binding character of this resolution illustrates the will of the Security
Council to enforce effective measures on member states and to harmonize counterterrorism
practices. The UN urged member States to implement the following measures in order to
strengthen the legal and institutional ability to counter terrorism. These measures include the
(1) preventing and suppressing the financing of terrorist acts; (2) criminalizing, either directly
or indirectly, terrorist funding; (3) freezing assets of persons who commit/attempt to
commit/facilitate/participate in terrorist acts; (4) prohibiting citizens from aiding terrorists
financially; (5) and lastly states should prevent the movement of terrorists by border controls.
domestic laws and regulation” (S/Res/1373, 2001). Although these measures have not been
presented as best practices at the time, they illustrate the UN’s first steps towards a more
comprehensive counterterrorism policy.
This new approach towards countering terrorism has not only led to legislative changes, but
structural changes as well within the UN. The adoption of Resolution 1373 and the subsequent
adoption of Resolution 1377 on November 12, 2001, established the Counter-Terrorism
Committee (CTC). The CTC consisted of the fifteen members of the Security Council and was
invited to “(…) explore ways in which States can be assisted (...), by the promotion of best
practices in the areas covered by Resolution 1373” (Rosand, 2004:548; S/Res/1377, 2001). The
CTC was tasked with monitoring the implementation of the resolution and to urge states to
report on actions they had taken in the counterterrorism domain. In order to assist CTC in its
mandate the CTED – as an capacity building body – was established with the adoption of
Resolution 1535 in march 2004 (S/Res/1535, 2004). The CTED was seen as a revitalization of
the CTC, which provided additional resources. For example the CTC established an Information
and Administrative Office (IAO) and an Assessment an Technical Assistance Office (ATAO)
(Rosand, 2006:410). These offices were tasked with making an inventory of best practices.
Additionally, the Security Council strived for a more proactive role for the CTC. Both the CTC
and the CTED were therefore tasked with encouraging “(…) countries to apply known best
practices, codes and standards, taking into account their own circumstances and needs” (Our
Mandate, 2016). Through active dialogue with member states the CTC and CTED are able to
assess which practices a country has employed, as member states are obliged to report to the
CTC on the actions taken with regard to countering terrorism. (Rosand, 2006:410). The CTC
can then analyze the filed reports and make suggestion for improvements if necessary. This has
enabled the CTC to make a comprehensive inventory of the capacity building needs of different
countries throughout the years. As such Resolution 1373 marked the beginning of setting up
standards of best practices with regards to countering terrorism.
The adoption of Resolution 1624 in September 2005 can be seen as an evolution of best
practices by focusing on the incitement to commit acts of terrorism (S/Res/1624, 2005). This
Resolution covers multiple themes which range from human rights to economical
destabilization. Additionally, freedom of expression is pointed out by stating that although
counter-incitement initiatives should be examined, universal standards should be protected – in
particular the right to freedom of expression and judicial protection. Hence, criminalizing public
built upon the terms set in Resolution 1373 (S/Res/1805, 2008). The main focus of this
resolution was the incorporation of the human rights aspects of counterterrorism, which – until
that point – were not incorporated into the CTC’s and CTED’s communication with member
states.
Furthermore, the CTC seeks active cooperation with international organizations in its efforts to
develop best practices. The best practices therefore incorporate measures that have been
developed by various United Nations entities and international and regional organizations,
including the International Monetary Fund (IMF), INTERPOL, United Nations Alliance of
Civilizations (AOC), the European Union, the Organization of African States (OAS) and the
Organization of the Islamic Conference (OIC).
2.3 Best practices in the Soft and Hard Power Framework
Since Resolution 1373 the CTC and CTED have developed multiple directories in which best
practices are compiled of relevance to the various provisions of the resolutions. The ‘Technical
Guide to the implementation of Security Council Resolution 1373’ (2009) further clarifies these
measures. Within the directories two major recurring themes can be identified, namely (1)
terrorist financing and (2) law enforcement and legal practices. In this next section best
practices with regards to each of these themes will be listed and explained. This will be followed
by categorizing the instruments identified within the soft and hard power framework.
Terrorist Financing
(1)Criminalization of Financing of Terrorism and Associated Money-laundering
(1.1)Anti-money-laundering law in force
(1.2)Law specifically criminalizing the provision or collection of funds with intention of use for terrorist acts
(1.3)Law criminalizing the financing of terrorist organizations and individual terrorists
(2)Freezing Terrorists’ Assets
(2.1)Provision for the freezing of funds and assets of terrorist, whether of licit or illicit origin
(2.2)Guarantees of due process
(3)Reporting suspicious transactions related to terrorism
(3.2)Reporting obligation for financial institutions and other intermediaries
(3.3)Penalties for non-compliance with the reporting obligation
(3.4)Legislation relating to customer identification and record keeping (4)Institutional and other measures necessary in systems for combating
money-laundering and terrorist financing
(4.1)Establishment of a financial intelligence unit or equivalent (4.2)Regulation of alternative remittance systems/money transfer
services (informal money transfer systems, wire transfers, cash couriers)
(5)Non-profit or organizations
(5.1) Regulation of charitable organizations (6)Criminalization of assistance
(6.1)Criminalizing of any form of assistance (transport, lodging etc.) (6.2)Assistance criminalized with adequate precision to give fair notice
of the conduct prohibited and to avoid misuse to suppress lawful
demonstration or dissent
Table 2: Terrorist financing
Terrorist financing refers to the prevention and suppression of the financing of terrorist acts and
focuses on undermining the flow of resources of terrorists (Technical Guide to the
implementation of Security Council Resolution 1373, 2009:p.7-14; Directory of international
best practices, codes and standards, 2001; S/Res/1373, 2004). Point (1) refers to undermining
the financial infrastructure of terrorist organizations by criminalizing the financing of terrorism,
terrorist acts and terrorist organizations, whether the funds were derived illegally (e.g. drug
dealing, robbery, hostage taking) or legally (e.g. donations). Anti-money-laundering refers to
concealment, disguise, conversion, transfer of property, knowing that this property is the
proceeds of crime. Punishing money-laundering should contribute to the suppression and
prevention of the financing of terrorism.
Point (2) refers to blocking, restraining or taking control of specific funds or assets by removing
the control the owner has over the funds or assets. In this way they cannot be used for an
unlawful purpose. An important part of this best practice is that states should employ this
measure in respect the rights of all the persons involved. Financial institutions and non-financial
business and professions play a big role in preventing and suppressing the financing of
Point (3) states that it should be mandatory for these organizations to report any suspect
transactions to the authorities. Organizations that fail to report will receive penalties. Countries
have to register or license persons and legal entities that provide the service where funds are
moved (geographically) from one location to another. In this case one can speak of a formal
money transfer system. Additionally, regulations must be developed for the activities of cash
couriers, which refers to persons that carry cash across national borders, shipment through cargo
and mailing by a person (cross-border movement).
Point (4) refers to creating competent institutions that possess the powers and resources to
combat money-laundering and the financing of terrorism. Institutions like these are seen as an
intermediary between the authorities and private sector that receives, analyzes and disseminates
reports on suspicious transactions/activities.
Point (5) pertains to monitoring and regulating charitable organizations, which terrorists can
use to raise and transfer funds, provide direct logistical support to terrorists or serve as a cover
for their operations. More specifically the state has to assess the sector’s risk of abuse for
terrorist financing. However, regulation has to be proportionate as Non-Public Organizations
(NPO’s) often play a positive role in a state’s development and provide valuable humanitarian
work.
Lastly, point (6) refers to criminalizing various forms of assistance to commit terrorist acts.
States should be specific and list which forms of assistance (lodging, transport, provision of
facilities/equipment) are criminalized, while ensuring conformity with the principle of legality.
When categorizing terrorist financing within the hard and soft power framework one could
argue that these measures focus on depriving potential terrorist groups of funds and are
therefore economic instruments – as they aim undermine the financial structure of terrorist
organization. At first view it may seem that these best practices can be categorized as hard
power. Such an assessment, however, does not represent the whole picture. Point (1) of this
best practice emphasizes “criminalizing the financing of terrorism” through a set of laws aimed
at punishing money laundering and depriving terrorist of funds that have been derived legally
or illegally. Therefore, point (1) falls under the development of laws that criminalize terrorism
and is a legal-repressive instrument which falls under hard power. Point (2) speaks of “(…)
blocking, restraining or taking control of specific funds or assets by removing the control the