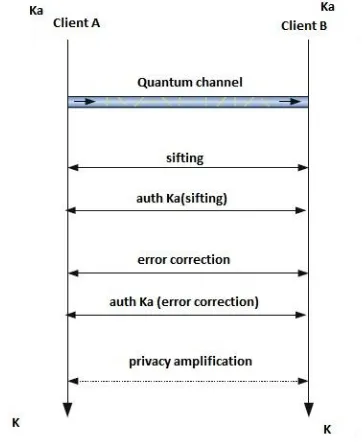
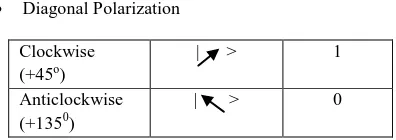
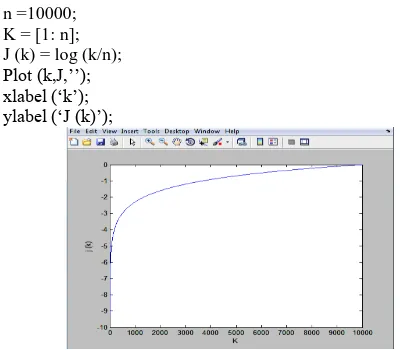
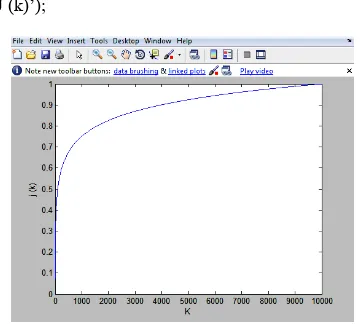
Entropy Security in Quantum Cryptography
Full text
Figure
Related documents
The company has established a comprehensive training and career development courses to provide multi-level training for agents, team managers, agent trainers, agent supervisors
To facilitate the development of an optimum UTL debulking and staging process, an analytical model has been employed to predict the extent of heat generation and cure of an 8552
In summary, our pilot trial showed that a 12-week super- vised moderate intensity aerobic exercise training pro- vided additional beneficial effects on cardiometabolic risk factors
Based on prior research and survey conducted (such as Ungku Harun Al-Rashid, 2004; Chang, 2004; Azizah, 2004; Lawrence, 2002), major skills that are highly required
This theory predicts that there are no order ef- fect for consistent evidence (overall positive or overall negative), but the recentness effect (se- quence) occurs when
We compared presence and abundance of native and exotic invaders with changes in wetland plant species diversity over a 28-year period by re-surveying 22 ponds to identify factors
While it is obvious that currently vanilla prices are historically high (see Fig. 1), livestock could play a much more important livelihood role when vanilla prices drop (see Table 3)
Organization Description Billing Address City State Code Big Beaver Falls School District 2218 8th Avenue Beaver Falls PA 15010 Bruce McKee Plumbing and Heating 2503 7th Av Beaver