An Efficient SKM Framework for Data Authentication and its Application to the Adhoc Networks
Full text
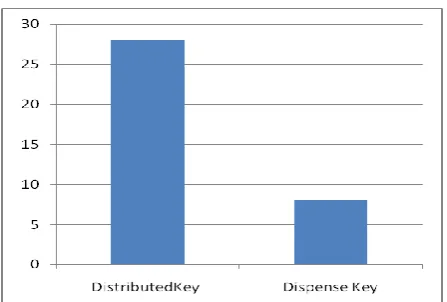
Figure

Related documents
communication systems stays stationary outside the structure and talks to another person with the matching communications system inside the structure to test
Other readings (not required): Pearson, Neil D., 2002, Risk Budgeting: Portfolio Problem Solving With Value-at-Risk (New York: John Wiley & Sons), Chapters 11, 12, and 13;
Description: The CapX2020 transmission plan consists of approximately 250 miles of new double-circuit, 345 kV transmission line between Brookings County, South Dakota, and
RUSHES MANAGEMENT 20 ACQUISITION LOCATION/STUDIO CAMERA/CARD FORMAT Choice of file-based camera Integrated or separate audio recorder Codec on camera Audio codec Choice of
sumed in the theory section. This decision was made after conducting a pilot experiment where individuals drew costs up to $1. I found that, with such low opportunity costs,
Furthermore, while symbolic execution systems often avoid reasoning precisely about symbolic memory accesses (e.g., access- ing a symbolic offset in an array), C OMMUTER ’s test
This descriptive quantitative study was designed to determine if a significant relationship existed between open enrollment students and students living within the district in
In the longer first period of 17 months (high salinity, low DIN/SRP), Cabras Lagoon was characterized by cyanobacteria of functional group Z.. This state abruptly changed