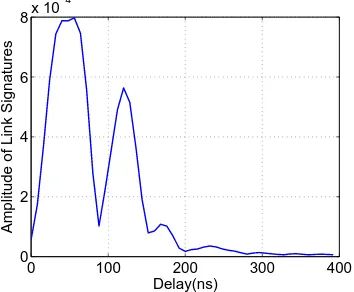
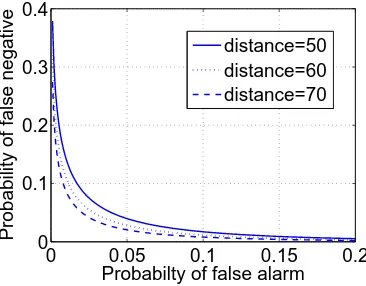
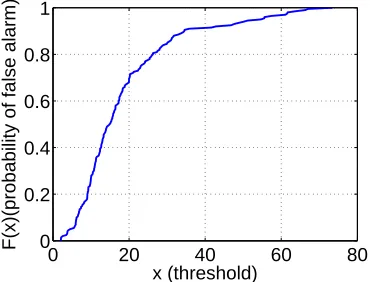
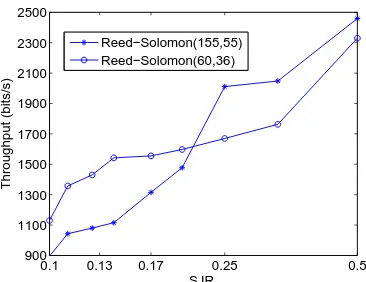
Wireless Physical Layer Security.
Full text
Figure



Related documents
GRANDEUR - PRIMO DES BRUYERES - LE MIOCHE XX Fokker: Eigenaar: VERSMISSEN, A.P... VD VAART- VAN
Chapter One introduces the study by providing a background for the main concepts and contexts of the study, namely first language acquisition, second language
Human elements involved in the problem Support systems surrounding the problem Tracking systems related to the problem.. Institutional process for managing
The total coliform count from this study range between 25cfu/100ml in Joju and too numerous to count (TNTC) in Oju-Ore, Sango, Okede and Ijamido HH water samples as
Variations in the concentration of elements in plant samples of the tunnel #504 on the sampling profi le Analysis of the results suggests that the point with the highest
Over the past nearly two decades, Nutrasource has expanded its services far beyond its original omega-3 blood test to include international regulatory capabilities,
This snippet of code will run the robot forward at half speed until the sonar sensor in digital-port 2+3 reads a value less than 45 centimeters, and then stop... ROBOTC