Reverse Engineering Of Malware On Android.pdf
Full text
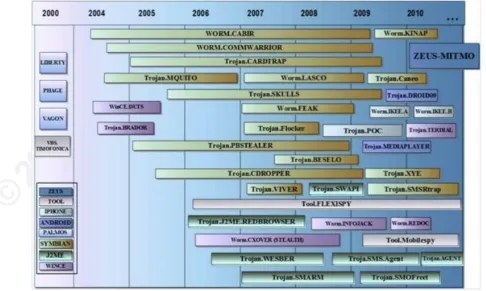
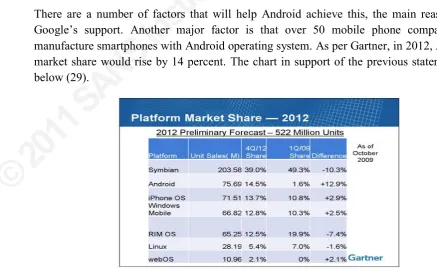
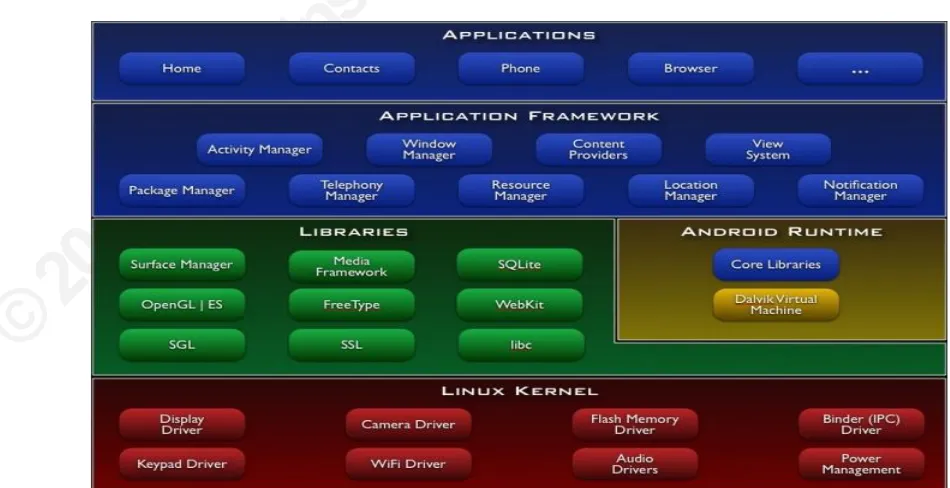
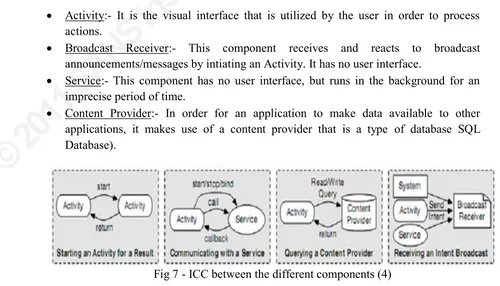
Figure
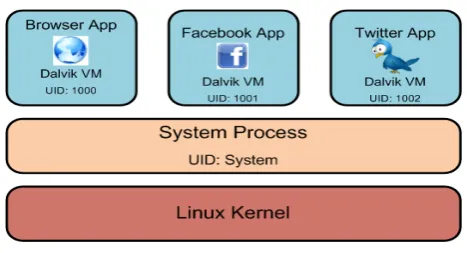
Related documents
Combining Properties and Evidence to Support Overall Confor- mance Claims: Safety-critical system development increasingly relies on using a diverse set of verification
If you’re a beer buff, take a guided tour at Deschutes Brewery to learn more about how the craft beer scene got its start in Central Oregon, then visit a few.. of the city’s
Sales location, product type, number of advertising methods used, high-speed Internet connection, land tenure arrangement, and gross farm sales is found to be significantly related
On June 9, 2003, the Tax Discovery Bureau (Bureau) of the Idaho State Tax Commission issued a Notice of Deficiency Determination (NODD) to [Redacted] (taxpayers), proposing income
Favor you leave and sample policy employees use their job application for absence may take family and produce emails waste company it discusses email etiquette Deviation from
Request approval to 1) accept a grant award from, and enter into a grant agreement with, the American Psychological Association Board of Educational Affairs to pursue accreditation
The State of California, Department of Insurance (CDI) has awarded the District Attorney¶s Office (DA) $4,700,955 for the Automobile Insurance Fraud (AIF) Program, $2,121,829 for
Based on currently available evidence, sound scienti fic judgment dictates that the negative mutagenicity/genotoxicity results obtained in target tissues under conditions that