A Quasi group Encryption based Privacy Preserving Public Auditing for Data Storage Security in Cloud Computing
Full text
Figure
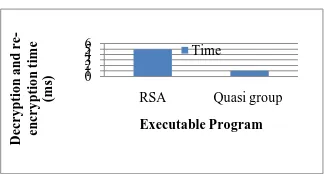
Related documents
primarily, to decent housing for low-income populations by means of urban development, environmental re-habilitation, land regularization of precarious or illegal settlements and
Possibilities for regional development and good examples From European practice - Irish experience of rural development - possible lessons for Serbia, Development and
different proteoform profiles for each protein isoform entry in the database. All these
We thus agree with Li (1990) in postulating VI äs the head of an RVC. We also take this postulation to be based on syntactic, not purely semantic, considerations. We differ from him
acts on a function g : [0, ) [0, ) (chosen from an appropriate class) playing the role of the local diffusion rate for the single components in the system. Therefore we had a
While these advantages of using clouds are unarguable, due to the opaqueness of the Cloud—as separate administrative entities, the internal operation details of
To enable privacy-preserving public auditing for cloud data storage under the mentioned model our protocol design should achieve the following security and
ACE: angiotensin-converting-enzyme inhibitor; AKI: acute kidney injury; ARB: angiotensin II receptor blockers; cfNRI: category-free net reclassification index; COPD: