Advanced Persistent Threats and its role in Network Security Vulnerabilities
Full text
Figure


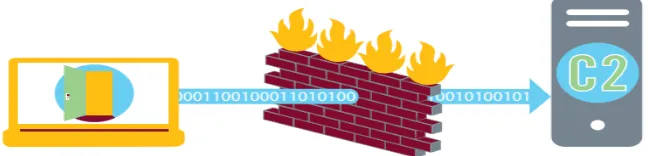

Related documents
Internationally many nations are seeking to recognise and reward excellent teaching at an institutional, subject and individual level, acknowledging the importance
5 In the case of TSMT, additional dissection of adipose tissues was performed at the aortopul- monary window, at lateral of both phrenic nerves from phrenic nerve to both
After failed radiofrequency (RF) energy applications at right His-bundle region, the complete elimination of atrial tachycardia was achieved with an RF energy application in
The magnitude of difference (average of weekly measurements on step counts and self-reported occupational sitting) between (i) baseline, (ii) throughout the ramping phase (weeks 1 –
Pearson's correlation coefficients among the scores of the Korean version of BD-QoL, the BD Clinical Activity Form for Korean Patients (BDCAF-K), and the Korean version of Center
In this study, the genotoxic effects of three commonly used NSAIDs were investigated using the frequency of SCEs in peripheral lymphocytes before and after drug use in
As outlined in Figure 12, 21% of the participants have the opinion that there will be a conflict, if the Olympic Games are scheduled during religious festivals; 15% of the
software acquisition security (includes the security specifications in all processes to buy, rent, or interchange software to use in an enterprise) and
