Relatively-Sound NIZKs and Password-Based Key-Exchange
Full text
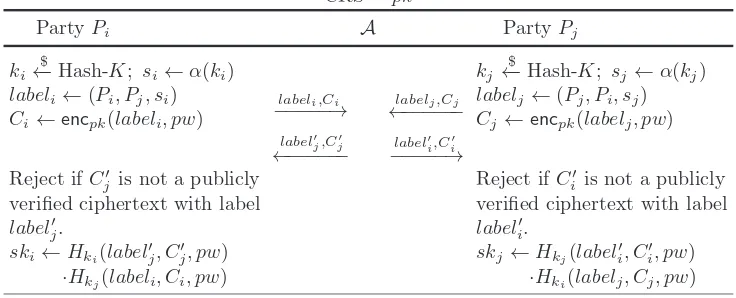
Figure



Related documents
TITLE: Correlates of extinction risk in squamate reptiles: the relative importance of biology, geography, threat and range size9. AUTHORS: Monika Böhm, Rhiannon Williams,
This study used multiple regressions to predict the effect of hope, coping strategies and levels of flourishing on the adjustment to university of 81 first year UK and international
Unfortunately, most on-line/off-line signature schemes can not be proven to be secure if their off-line signature tokens are exposed in the off-line signing phase. 5 In this paper,
This captures all possible side-channel attacks on S where the amount of information leaked in a given period is bounded, but overall can be arbitrary large, in particular much
The chapter covers the following: principals ' support for school counsellors, provision of counselling resources and facilities, training of teacher counsellors , availing time
AF: atrial fibrillation; ASMD: absolute standardized mean difference; DM: diabe‑ tes mellitus; DPP4i: dipeptidyl peptidase‑4 inhibitor; HA: hypoglycemic agents;
Violence Risk Assessment: The process of identifying behaviors that may signal an individual’s preparation to commit a violent act, assessing those behaviors in the context of