Secure De-Duplication over Cloud Using Attribute Based Access Policies
Full text
Figure
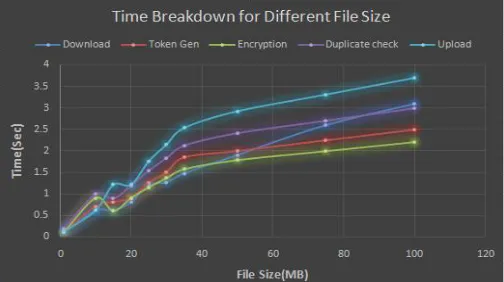
Related documents
Classroom teaching is the basic approach and core of curriculum implementation. To implement the principle of student-centered and advocate the students to
• Available in two widths 850mm or 1000mm • Flexible height from 1600mm to 2250mm • Double sided retractable banner stand • Comes complete with nylon carry bag •
The summary resource report prepared by North Atlantic is based on a 43-101 Compliant Resource Report prepared by M. Holter, Consulting Professional Engineer,
From a Korean perspective AustranaTs it eleventh largest export market and sixth most important import sour~ While Korea's financial and economIc cnS1S of 1997-98
Penurunan ini karena produksi senyawa penghambat aktivitas enzim (Galliard, 1971), atau produk samping dari hasil reaksi atau terjadi inaktivasi enzim dengan semakin
Public awareness campaigns of nonnative fish impacts should target high school educated, canal bank anglers while mercury advisories should be directed at canal bank anglers,
Nazario Moreno, the enigmatic spiritual leader of the cartel, was allegedly killed in a shootout with government forces in December 2010 and soon after various factions
The social representations of QoL, wellbeing and happiness described by these students were offered without any discussion of tourism at