BlindBox: Deep Packet Inspection over Encrypted Traffic
Full text
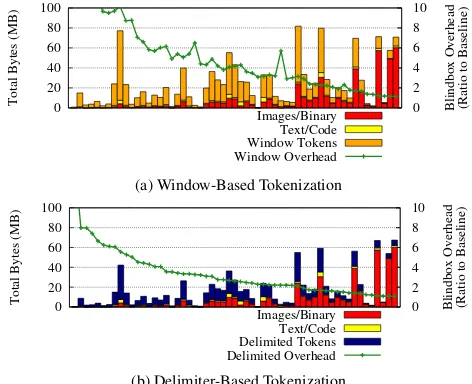
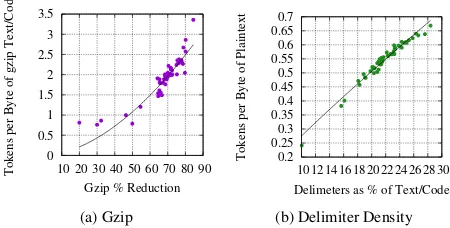
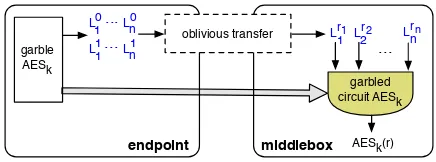
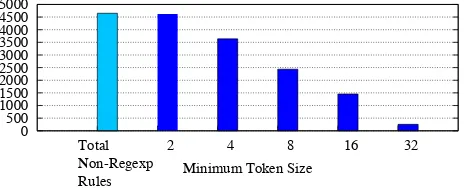
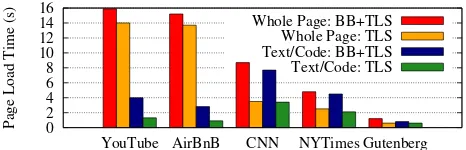
Figure

Related documents
[r]
Menu boards, custom logo signs, outdoor window displays, interior wall graphics and even creative custom signage.. We can even provide promotional items like posters and table
As can be seen in Table 2, the intervention group showed superior functioning at post-treatment on measures of seven cognitive domains: general cognitive functioning
(Fiscal 2019)) In addition, our shares held by the trust account are included in the total number of treasury shares which are deducted in the calculation of the average number
The Shared Services Summit demonstrated that Broome County’s local governments are committed to improving the quality and cost-effectiveness of the services that they provide to
As shown (Table 3) non-exchangeable potassium was significantly and positively correlated with HNO 3 boiling potassium (r=0.999*), exchangeable potassium (r=0.967) and
a 293T cells were transfected with L1-GFP reporter plasmid or the control vector JM111, together with empty vector (pcDNA), SAMHD1 wt, non-phosphorylated SAMHD1 T592A,
The Ou Reang Ov soil occurs in similar locations and generally in close proximity to Labansiek and Kompong Siem Soil groups in the basaltic landscapes of eastern