An Internal Intrusion Detection and Protection System by Using Data Mining and Forensic Techniques
Full text
Figure
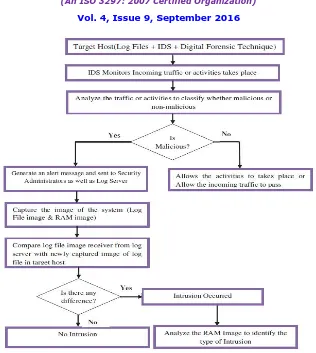
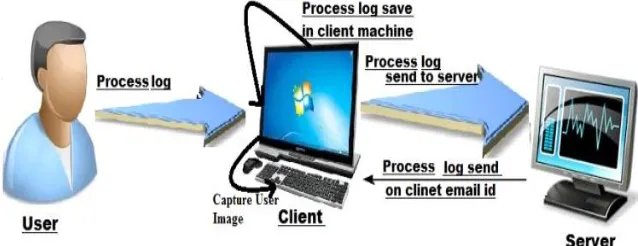
Related documents
At startup, the RDB sends a message to the tickerplant and receives a reply containing the data schema, the location of the log file, and the number of lines to read from the
According to the relationship between the decomposing behavior of EEMD algorithm and the decomposed results of different IMFs with different frequencies, this
Generally speaking transnational corporations are one of the driving forces of international production internationalization, international trade liberalization and ultimately
It will give you information about your site's visitors: activity statistics, accessed files, paths through the site, information about referring pages, search engines,
Web Server Logs Using Web Usage Mining Web Usage Mining process , W3C log file format Uses unstructured data Worked on. single log file
For the cases involving two electron donor ligands (e.g. PEt 3 , CO, t BuNC), the rate at which the ligand binds to the metal centre must be faster than the rate of
(hereinafter: Xiangyu company) developed the Xiangyu • Yosemite project as background, a more systematic and comprehensive exposition of the real estate market formation
Also, econometric model specifies the moderate relation between excess bank liquidity and non- performing loan (NPL) which supports the real economic model that