Analysis of Security Vulnerability Assessment in Web Application Environment Using Common Vulnerability Scoring System Method
Full text
Figure

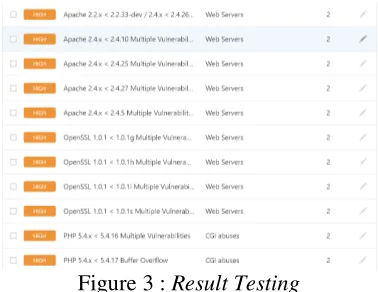
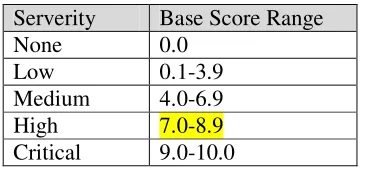
Related documents
Model 3.2 is estimated with two-stage least squares, with election-year incumbent job approval, challenger spending, and incumbent spending treated as endogenous and the
KCWE is the only station in Kansas City to offer local
Changes in the fair value of derivative fi nancial instruments that are designated as fair value hedges and are eff ective in relation to the hedged risks are recognised in profi t
For the assessment of sensitivity for the diagnosis of active TB, two defi nitions of disease were accepted: defi nite (confi rmed) and probable TB. Defi nite TB was defi ned as
Third, because of the established positive role of psychological capital (PsyCap) on attitudes, behaviors, and performance (for a recent meta- analysis on the research, see
For modules of the Core OpenStack Project, the Technical Committee may recommend to the Board of Directors the modules for addition, combination, split or deletion from the
Cooling method: Air cooled Clock: 22 MHz EM gain: 4 × Exposure time: 13.93 ms No light Clock:22 MHz Cooling temperature: –65 ˚C Air cool, Ambient temperature: +20 ˚C Elapse
If short term priority and long term priority are combined, the list of priorities is headed Talent Management, Employee Retention & Motivation, Capability &