SECURITY PROTOCOL FOR WIRELESS SENSOR NETWORK
Full text
Figure
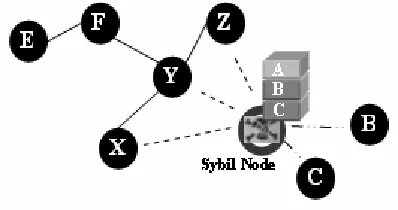

Related documents
Faxafdruk op volledige pagina Master thesis CE&M The reduction of life cycle costs by the application of service level agreements Arnhem, February 2008 Y (Yvonne) Lenters (s)
The present study aimed to analyze and compare the prognostic performance of the Glasgow-Blatchford (GB), pre-endoscopy Rockall (PER), and modified early warning (MEW) scores
In this study, we use recession flow analysis as outlined by Brutsaert and Nieber (1977) to investigate the possible permafrost thawing rate in response to climate change in
trans -regulatory variation affects standing levels of gene expression: To examine the effects of trans - regulatory variation on transcript abundance, we used pyrosequencing to
The hardware makes use of Solar panel, boost converter, battery, PIC 16F877A microcontroller, speed sensor and MOSFET for speed control of PMDC motor using
Is a motivational interviewing based lifestyle intervention for obese pregnant women across Europe implemented as planned? Process evaluation of the DALI study RESEARCH ARTICLE Open
Characteristics of the syneruptive spouted type lahar generated by the September 2014 eruption of Mount Ontake, Japan Sasaki et al Earth, Planets and Space (2016) 68 141 DOI 10
Kim and Kim Advances in Difference Equations 2013, 2013 343 http //www advancesindifferenceequations com/content/2013/1/343 R ES EARCH Open Access Hermite and poly Bernoulli mixed