Evaluation of off target and on target scoring algorithms and integration into the guide RNA selection tool CRISPOR
Full text
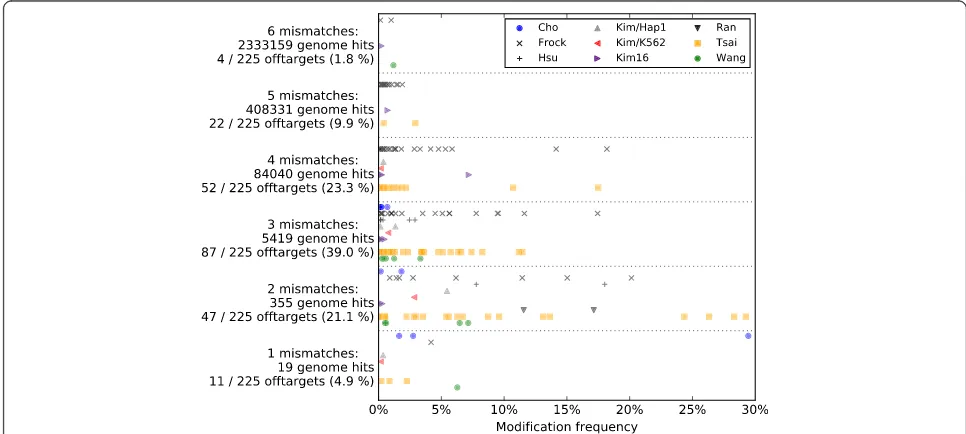
Figure



Related documents
The corona radiata consists of one or more layers of follicular cells that surround the zona pellucida, the polar body, and the secondary oocyte.. The corona radiata is dispersed
Introduction The Student Health Insurance Load process (ZSRHIEL) allows users to assign students listed in the USG approved Health Insurance provider waiver/exemption file to
I problematize three family images associated with the design and implementation of housing projects: the bureaucratic family, envisaged by policymakers as conflating with a model
In 2011 there was a high level of field activities in Green- land with a major mapping and geochemical programme in South-East Greenland, a large field and shallow-core drill-
Human elements involved in the problem Support systems surrounding the problem Tracking systems related to the problem.. Institutional process for managing
National Conference on Technical Vocational Education, Training and Skills Development: A Roadmap for Empowerment (Dec. 2008): Ministry of Human Resource Development, Department
In a recent Gartner survey (Source: Gartner: Survey Analysis: E-Commerce Customers Look to Cloud, Mobile and Transformational Change, July 2013, Fletcher, C., Alvarez G., et
The encryption operation for PBES2 consists of the following steps, which encrypt a message M under a password P to produce a ciphertext C, applying a
