Data Leakage Detection and Dependable Storage Service In Cloud Computing
Full text
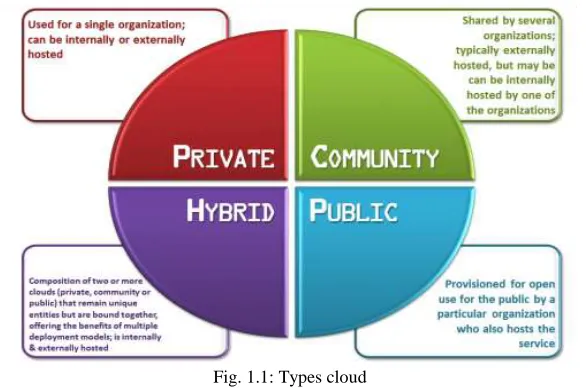
Figure



Related documents
National Conference on Technical Vocational Education, Training and Skills Development: A Roadmap for Empowerment (Dec. 2008): Ministry of Human Resource Development, Department
However, obtaining bacterial genomic information is not always trivial: the target bacteria may be difficult-to-culture or uncultured, and may be found within samples containing
The corona radiata consists of one or more layers of follicular cells that surround the zona pellucida, the polar body, and the secondary oocyte.. The corona radiata is dispersed
○ If BP elevated, think primary aldosteronism, Cushing’s, renal artery stenosis, ○ If BP normal, think hypomagnesemia, severe hypoK, Bartter’s, NaHCO3,
The FSC logo, the initials ‘FSC’ and the name ‘Forest Stewardship Council’ are registered trademarks, and therefore a trademark symbol must accompany the.. trademarks in
• Excellent mechanical stability and corrosion protection • Excellent oxidation stability, helping extend grease life • Excellent extreme pressure, anti-rust and water
The main optimization of antichain-based algorithms [1] for checking language inclusion of automata over finite alphabets is that product states that are subsets of already