Collecting Sensitive Information from Windows Physical Memory
Full text
Figure


Related documents
Stampacchia: Le probleme de Dirichlet pour les equations elliptiques de second ordre a coefficients
However, there is a crucial difference between American, Spanish and Russian resistance to foreign occupation and late nineteenth century guerilla resistance in Cuba and
Note: If there is paper in the paper tray, pull the paper release plate forward and remove the paper before loading the imaging film.. 1 Open the operation panel by grasping the
We note that construction of the topological degree for elliptic operators in un- bounded domains is essentially different in comparison with the operators in bounded domains.. In
In the sequel we will abuse notation and simply denote ¯ u by
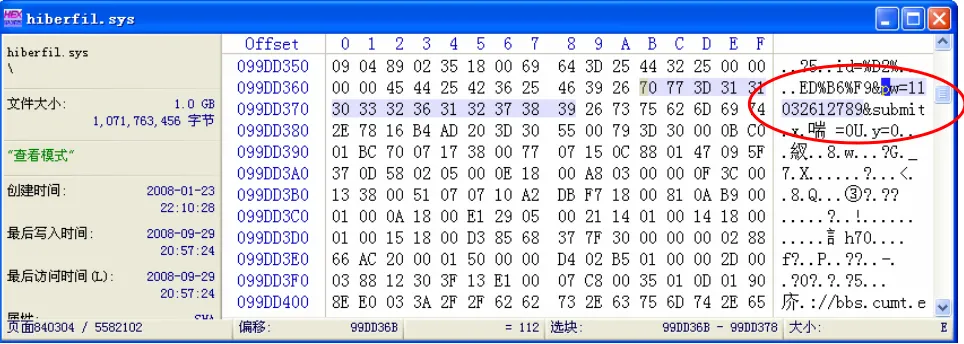
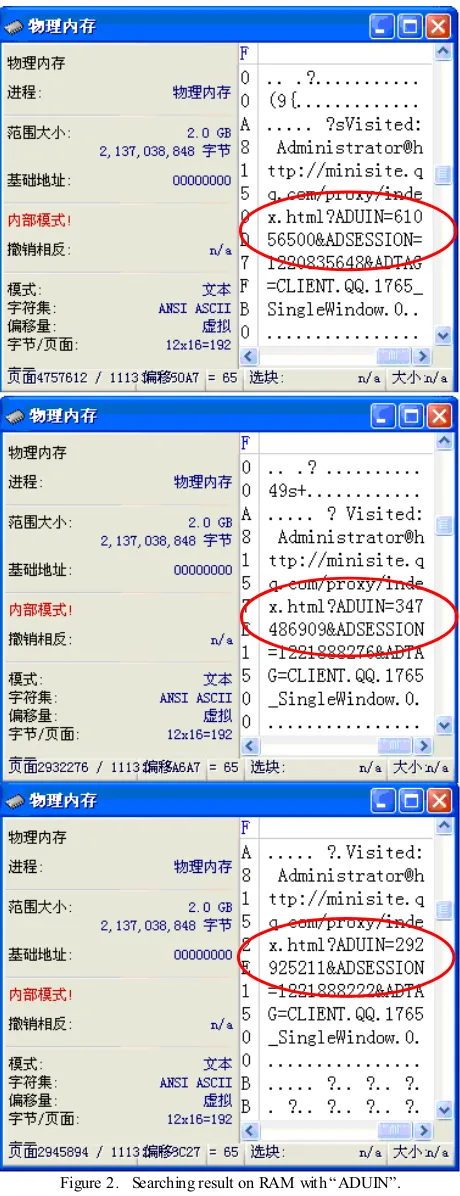
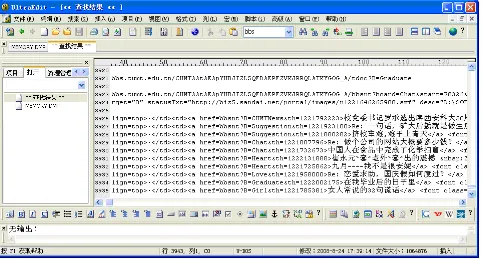
z z In X In X - - Ways Forensics, disks, interpreted image Ways Forensics, disks, interpreted image files, virtual memory, and physical RAM are files, virtual memory, and
For any edge (u, v) in G′, if there is a typical vertex x ∈ N(u) ∩ N(v), such that w(u, x) + w(x, v) = d(u, v), then, uprooting edge (u, v)from G′ won't influence the
Therefore, we apply for the discretization in time several explicit Runge- Kutta and Adam-Bashforth methods, means direct methods, as an alternative discretisation method to