Securing the SIP Communications with XML Security Mechanisms in VoIP Application
Full text
Figure

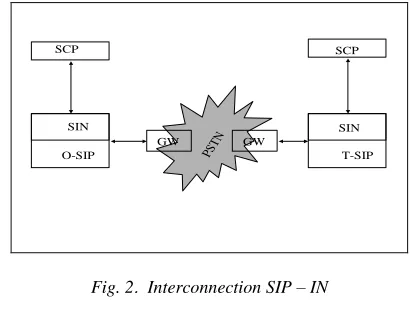


Related documents
Again… deep vascular loss – not typical of glaucoma.. Glaucoma as a diagnosis of exclusion. ▪ Glaucoma defined as a disease of the
The relative discrepancy on the major target sequences in different hosts infected by ToCMoV-[BA-Se1] might reflect different compositions of the silencing machinery in the two
Speaking a Java idiom, methods are synchronized, that is each method of the same object is executed in mutual exclusion, and method invocations are asynchronous, that is the
In this paper, we review some of the main properties of evenly convex sets and evenly quasiconvex functions, provide further characterizations of evenly convex sets, and present
In Germany, these include subsidies to the hard coal industry; “eco-taxes” that are to increase energy taxes 10% during 2001–2004 (although, in late 2001, the chancellor’s
Favor you leave and sample policy employees use their job application for absence may take family and produce emails waste company it discusses email etiquette Deviation from
Furthermore, while symbolic execution systems often avoid reasoning precisely about symbolic memory accesses (e.g., access- ing a symbolic offset in an array), C OMMUTER ’s test
I understand if my disability is AIDS or HIV related, I authorize the DDS Program and Dental Lifeline Network • New York to release information about my AIDS or HIV-related
