An Efficient Protocol for Securing Multiple Patient's Privacy in Wireless Body Sensor Network using ECIES
Full text
Figure
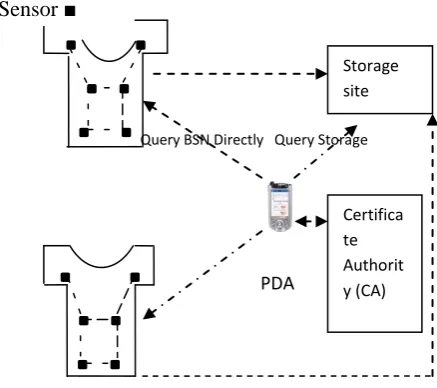

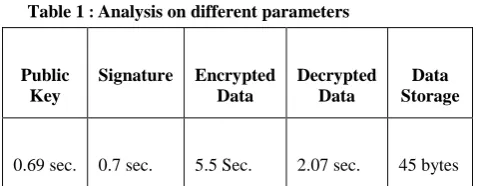
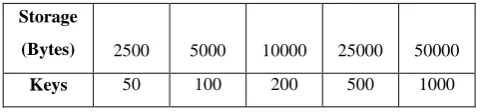
Related documents
cystic fibrosis clinic of the Hospital for Sick Chil- dren over the period 1977 to 1988 revealed that cystic fibrosis patients with insulin-dependent di- abetes meffitus are, for
did a study for predicting soil heavy metal contaminations using laboratory spectral reflectance; this research information provided another tool for investigation of
The readable message (original) is called plaintext.The secret message (not readable) is called cipher text.The process of converting plaintext to ciphertext is called
In this project, a 6- degree-of-freedom (6-DOF) motion generation platform must be designed and developed to simulate the Velodrome track cycling.. The parallel
Our data extended these findings to a cohort of tonsillitis patients in Hong Kong in which we observed a subtle but significant difference in oral rinse microbial community
For example, there is one case in 2007 where a digital forensic expert has needed to present his analysis of the CCTV (in mStar Online). Besides, social engineering has been
Methods: Linear and fractional polynomial regression analyses were performed with data from a study of Parkinson ’ s disease patients (n=138) to predict the EQ-5D index values
An effective computational approach based on Gegenbauer wavelets for solving the time fractional Kdv Burgers Kuramoto equation Secer and Ozdemir Advances in Difference Equations (2019)