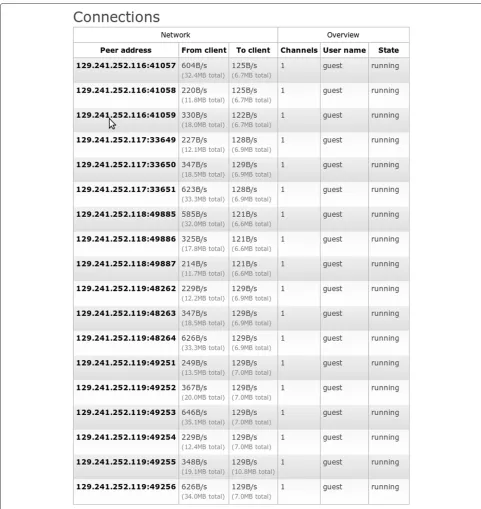
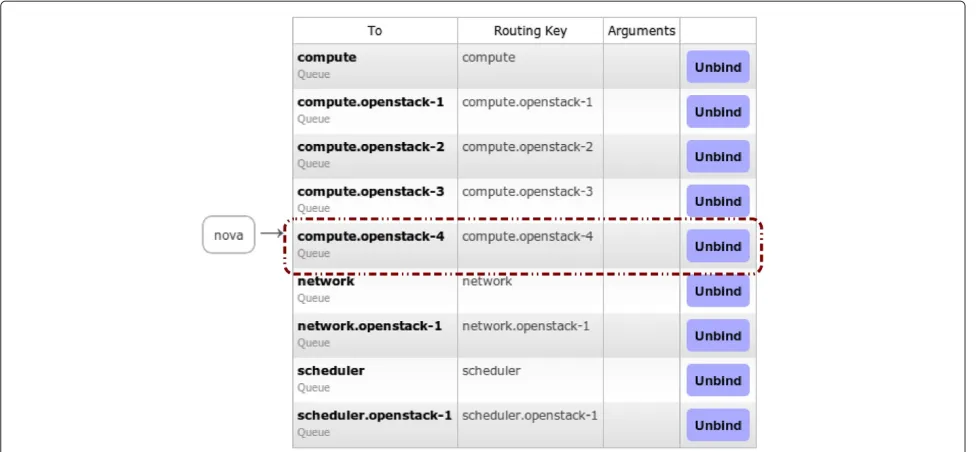
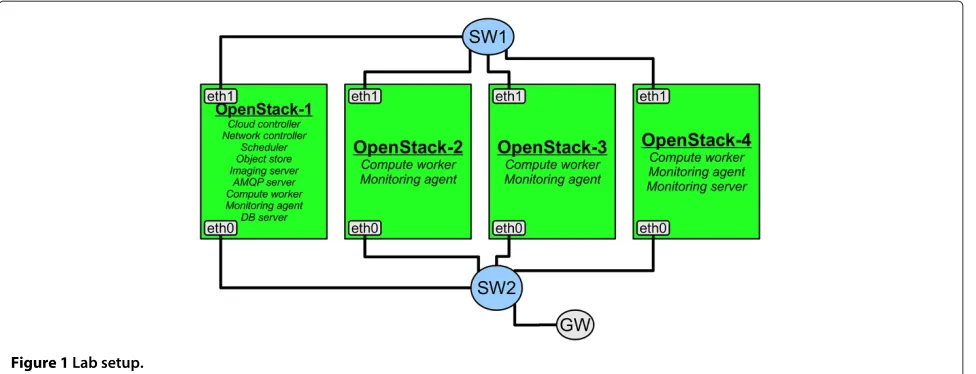
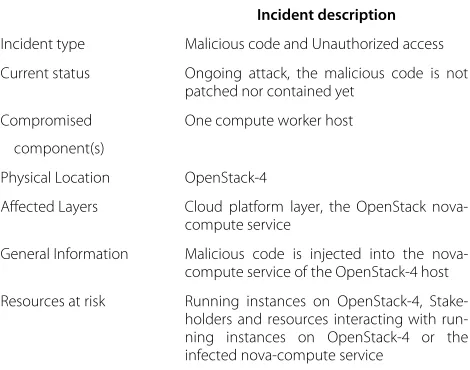
Handling compromised components in an IaaS cloud installation
Full text
Figure
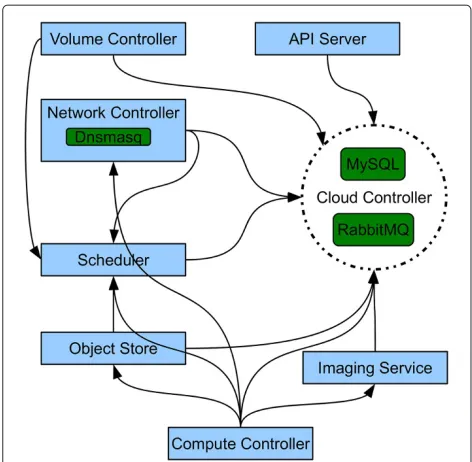
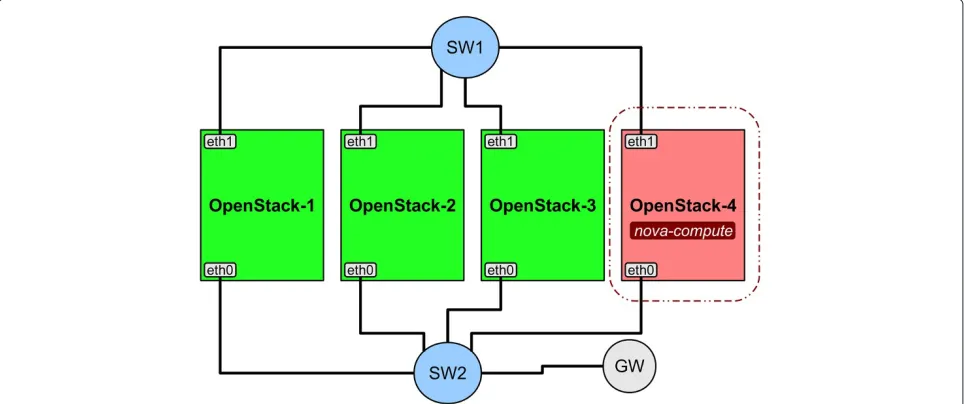
![Figure 2 OpenStack Compute basic architecture [6].](https://thumb-us.123doks.com/thumbv2/123dok_us/857773.1583366/3.595.57.541.86.311/figure-openstack-compute-basic-architecture.webp)
Related documents
‘Delivering Change in the Higher Education Sector’, Higher Education Leadership Conference, Dublin.. This Presentation is brought to you for free and open access by the Centre
Combining Properties and Evidence to Support Overall Confor- mance Claims: Safety-critical system development increasingly relies on using a diverse set of verification
Based on this understanding, this work focuses on the effect of the inclusion of shallow donor dopant such as gallium into the normal cadmium chloride post-growth treatment as
The three-dimensional frequency selective surface (3D FSS) with band reject multiple transmission zeros and pseudo-elliptic response is designed from two-dimensional (2D)
Kulick will celebrate Stations of the Cross each Friday during Lent from different parishes across the Diocese of Greensburg.. Videos of these celebrations will premiere
Sequences in the PR 2 database are assigned an identifier in the form accession.p1.p2_X, where accession is the ac- cession number of an entry, p1 and p2 are the positions of
This suggest that developed countries, such as the UK and US, have superior payment systems which facilitate greater digital finance usage through electronic payments compared to
message authentication and confidentiality where authentication is tied both to the plaintext and to the