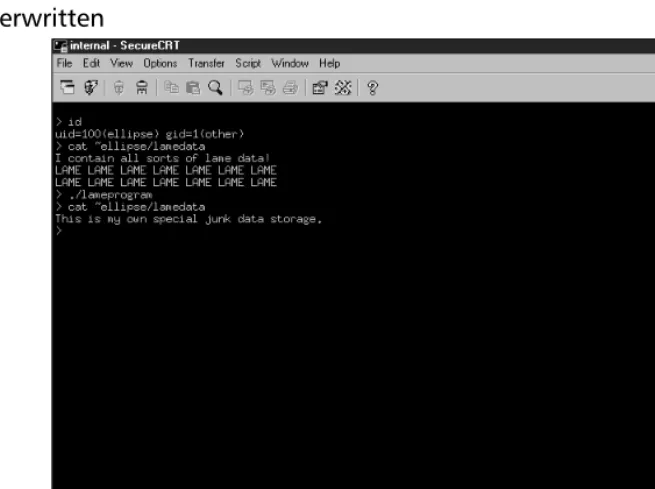
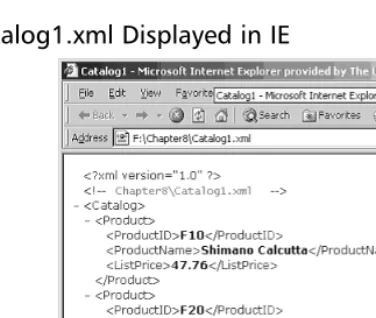
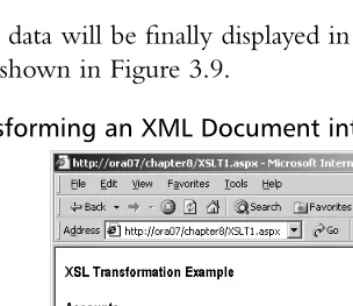
Hack Proofing XML pdf
Full text
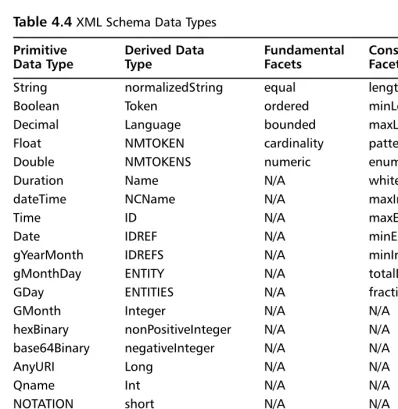
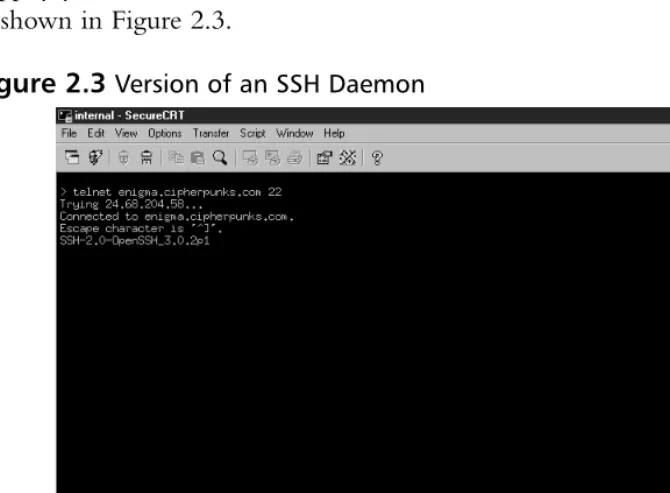
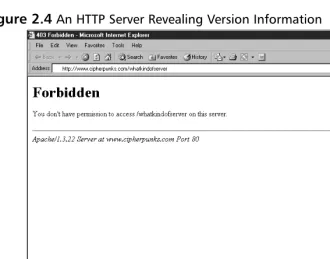
Figure


Outline
Related documents
– 96 000 Hz for sampling frequency, – 511 bits for length of Gold code sequence, – 7000 Hz for carrier and chip frequencies, – Method I for location estimation
The diversity level of fish catches caught by the fishermen in the waters of south coast of Java, Gunungkidul Regency, is low (the diversity index value is less than 2), except
Dosen harus melakukan login untuk dapat menerima presensi dari mahasiswa, melihat mata kuliah yang diajar, dan melihat peserta kuliah. Pengujian prototype pada halaman
With FGCS comprising such a large portion of a campus population at UK, it is important to note that while retention strategies that work for FGCS are likely to be successful for the
Research Question 1: The first research question (RQ1) addresses what impact the HIPPY program has on kindergarten student’s school readiness skills at Time 1 (early literacy,
Helping service staff know what’s going on and how to act smarter With hardware support for GPS, maps, geo-location and 4G connections, Windows 8 devices, ably assisted by
Incidence of liver failure, all-cause mortality and clinical disease progression following sustained virological response according to the pres- ence of bridging fibrosis or
The present study prospectively enrolled 226 Japanese patients with CHC, and investigated the impact of hepatic steatosis and its related SNPs, including rs8099917 of IL28B,