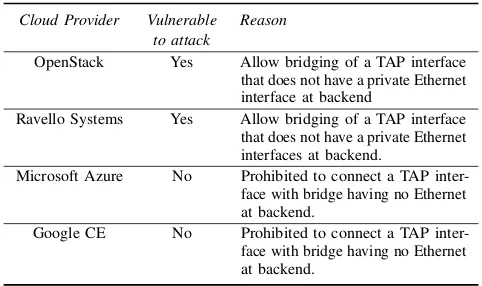
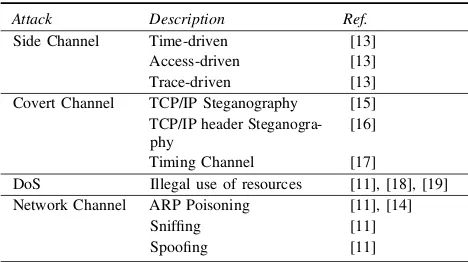
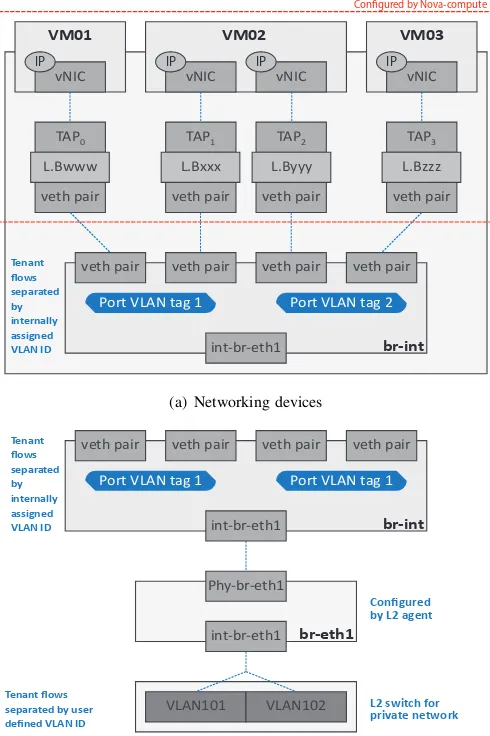
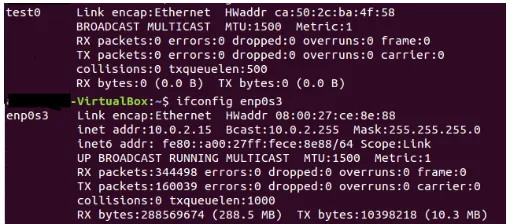
A Cross Virtual Machine Network Channel Attack via Mirroring and TAP Impersonation
Full text
Figure
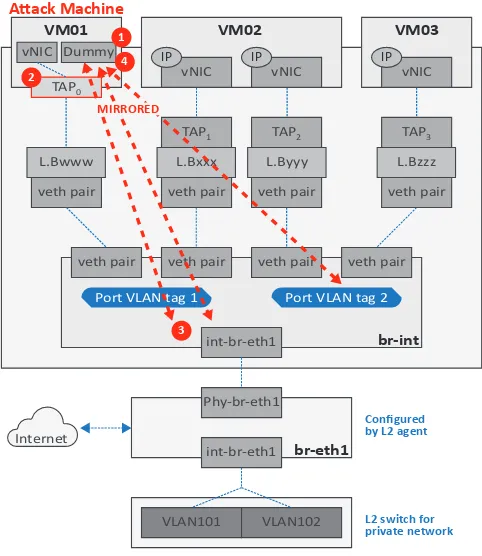
Related documents
• Classify tweets of a user filtered by a word as neutral, positive or negative. • Visualize a stream of tweets filtered by word and location. The reason why the first branch
the production of domestic hot water. Solar energy and heat pumps complement each other ideally in this application. Depending on your customer’s needs, an unpressurised
Rethinking the Fourth Amendment: Why the Coming Surveillance Society Need Not Lead to a Surveillance State, University of Mississippi School of Law National Center for Justice and
Specifically, the market might believe that the target 52-week high represents a sign of poor performance when the target’s current price falls below the 52-week high
Shuvrqdo lqfrph wd{hv dqg vhohfwlyh vdohv wd{hv duh erwk vwurqjo| qhjdwlyho| fruuhodwhg zlwk orfdo hfrqrplf jurzwk1 Irfxvlqj uvw rq shuvrqdo lqfrph wd{hv/ uhjuhvvlrqv ri qhw
Third, parental preferences play a key role in child time allocation decisions. In this set- up, preferences do not drive differences in the allocation of child time between the
suppression. Figure 2.1 reprinted with permission from Shahriari et al. Copyright 2014 American Chemical Society.. Illustration of Leidenfrost state suppression of a 100 µL isopropanol
FreeStyleXtreme replaced its carrier management system with Route Genie,. which is believed to be best in order fulfillment and returns segment in UK for a three-year