Cyber-physical security of a chemical plant
Full text
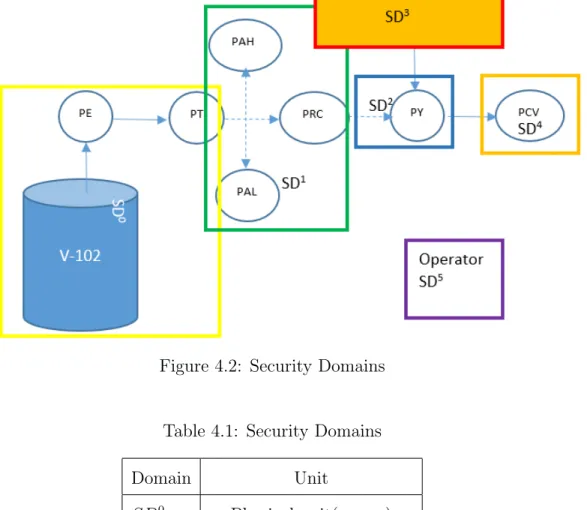
Figure
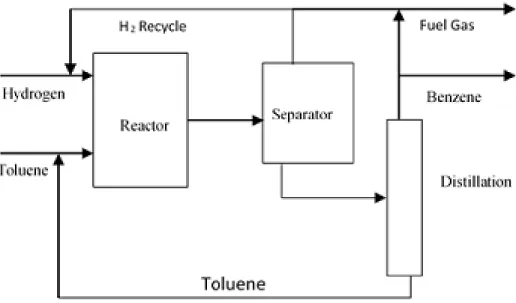
![Figure 3.2: P&ID [2]](https://thumb-us.123doks.com/thumbv2/123dok_us/1382399.2685176/24.918.172.810.107.564/figure-p-amp-id.webp)
Related documents
Significant, positive coefficients denote that the respective sector (commercial banking, investment banking, life insurance or property-casualty insurance) experienced
❖ Proposal I: concerned making all BOT meetings virtual meetings except the one at WSBC – defeated ❖ Proposal J: motion to disband the virtual services conference committee –
The high heritability estimates obtained for days to first flower, number of root nodules, number of seed per pod, and 100-seed weight, suggests that
This standard contains the essential welding variables for carbon steel plate and pipe in the thickness range of 16 through3/4 in., using manual shielded metal arc welding. It cites
Generally, there are two primary legal approaches to internet contract enforcement: The United States model that relies on basic notice requirements to establish and
Furthermore, while symbolic execution systems often avoid reasoning precisely about symbolic memory accesses (e.g., access- ing a symbolic offset in an array), C OMMUTER ’s test
The aim of this study was to evaluate the current vac- cination status of the HCWs in all of the Departments different from the Department for the Health of Women and Children of one
Incorporating the actual degree of facilities-based and service-based intra-platform competition allows an analysis of the efficacy of both forms of access regulation, including