IJRISE| www.ijrise.org|editor@ijrise.org[125-129]
A SMART DATA BACKUP TECHNIQUE IN CLOUD COMPUTING
USING SIGNCRYPTION
Sridevi .N.
1, Ashwini .A
21
Asst.Professor,, Dept of CSE,SVCE,Bengaluru
,n.sridevi5@gmail.com
2
PG Student Dept of CSE,SVCE,Bengaluru,
ashwini.ashu1091@gmail.com
ABSTRACT
In cloud computing, the data is generated in electronic form which is huge in amount. To maintain the huge amount of data efficiently, there is a need for data recovery services. To cater this, in this paper we propose a smart remote data backup algorithm, Seed Block Algorithm (SBA). The objective of proposed algorithm is twofold; first it help the users to collect information from any remote location in the absence of network connectivity and second to recover the files in case of the file deletion or if the cloud gets destroyed due to any reason. When the user’s data is stored in the remote server, the security to maintain the integrity of the user’s data should be provided so that the data can be shared among the different users. The integrity of cloud data is subject to uncertainty due to the hardware/software failures and human errors because of this. This paper also proposes a smart remote data backup technique using signcryption technique. The objective of proposed technique is to provide the privacy of any user while sharing the data in cloud.
Keywords
: Data recovery, remote storage, signcryption, seed block.
---
1.
INTRODUCTION
The files or information of clients which are stored in comp uter or laptop is lost due to hardware problem like if the system is crashed or data is corrupted then there will be no other source to recover it. It is very difficult to manage many client records and there are lots of chances of that errors can occur in maintaining the users and there is large data storage problem in centralized system. So the data is lost from the main server and there is no other backup facility to restore this data. So this method provides a feasible solution that collects data and sends it to a centralized storage location smartly and we can access the data remotely.
Today, Cloud Computing is itself a massive technology which is surpassing all the previous technology of computing of this competitive and challenging IT world .Cloud sto rage provides the online storage where data stored in form of virtualized pool that is usually hosted by third parties. The cloud computing has rapidly grown in recent years due to the advantages of greater flexibility and availability of computing resourc es at lower cost. Cloud service providers offer users efficient and scalable data storage services with a much lower marginal cost compared to traditional approaches. As Cloud computing gives flexibility, when users put their data in the cloud, its not required to manage the information stored in cloud storage. Cloud computing will allow you access all your application and document from anywhere in the world. The hosting company (Cloud service provider) operates large data on data centre and according to the requirements of the customer these data centre virtualized the resources and expose them as the storage pools that help user to store files or data objects. Data sharing becomes a standard feature in most cloud storage offerings, including Dropbox, iCloud and Google Drive. As number of user shares the storage and other resources, there are chances that other customers can access your data. Either the human error, faulty equipment’s, network connectivity, a bug or any criminal intent may put our cloud storage on the risk and danger.
The integrity of data in cloud storage, however, is subject to uncertainty as data stored in the cloud can easily be lost or corrupted due to the unavoidable hardware/ software failures and human errors. This matter can be made even worse, cloud service providers may avoid informing users about these data errors in order to maintain the reputation of their services and avoid losing profits.
To overcome these issues, we propose a new technique in which the data is stored in t he remote cloud. If the main cloud gets destroyed or data is lost then the remote cloud will give the back-up of data to the client. The data integrity is provided using signcryption technique.
IJRISE| www.ijrise.org|editor@ijrise.org[125-129]
2. RELATED WORK
In literature many techniques have been proposed PCS[1], Linux Box [2], HSDRT[3],ERGOT[4], Cold/Hot backup strategy [5] etc. that, discussed the data recovery process. However, still various successful techniques are lagging behind some critical issues like implementation complexity, low cost, s ecurity and time related issues.
Srno Approach Advantage Disadvantage
1 Parity Cloud Service[1] Reliable Privacy Low cost High complexity
2 LINUX BOX[2] Simple Low cost High bandwidth, Complete
server backup at a time
3 HSDRT[3] Used for movable clients Costly, Increased redundancy
4 ERGOT[4] Exact match retrieval, privacy Increased complexity
5 Cold/Hot Backup
Strategy[5]
Triggered only when failure
detected
Cost increases as data increases
Table- I. Comparison between various techniques of Back -up and recovery
The objective of Remote Data Collection Server: E-Health Care is to provide auto response server, better solutions for data backup and restore using cloud. It can collect data and send to a ce ntralized repository in a platform independent format without any network consideration [6].
All these techniques tried to cover different issues maintaining the cost of implementation but it creates large amount of data and requires more storage as the s ize of data is not reduced. Also there is lack of privacy and security in these techniques.
3.PROPOSED TECHNIQUE
The objective of proposed techniques is To help the users to collect and recover the files in case of the file deletion or if the cloud get s destroyed due to any reason
To maintain the privacy of any user during data sharing in cloud. Admin panel is used to preserve the
privacy of the user.
We are also providing encryption technique to provide security to the user’s data and digital signature to provide user authentication.
A .Seed Block Algorithm
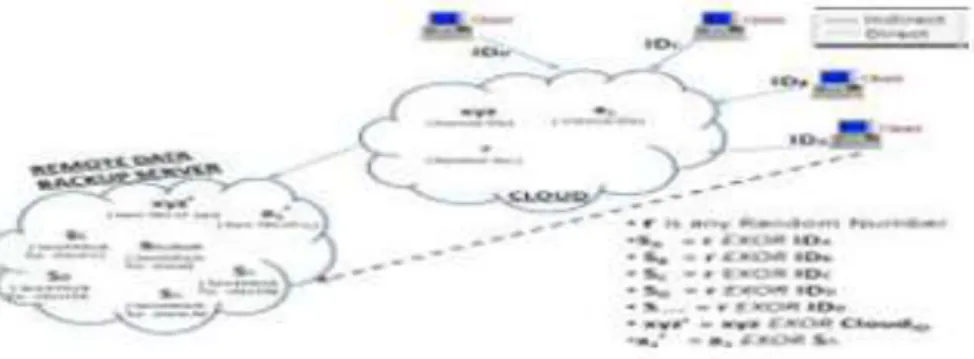
This algorithm used to provide the backup and recovery process. It is represented in Fig3.1 which contains main cloud and its clients and the remote cloud. Here, first the random number is set in the main cloud and the unique client id for every client. Second, when the client id is being registered in the main cloud; the client id and random number is getting EXORed with each other to generate seed block for the particular client. The generated seed block corresponding to each client is stored at remote server. When the client creates the file in cloud first time, it is stored at the main cloud. The main file of client is being EXORed with the Seed Block of the particular client when it is stored in main server. And that EXORed file is stored at the remote server in the form of file’ (pronounced as File dash). If either file in main cloud is crashed /damaged or file is been deleted by mistake, then the user will get the original file by EXORing file’ with the seed block of the corresponding client to produce the original file and return the resulted file which is the original file back to the requested client. The Seed Block Algorithm’s architecture representation is shown in the Fig 3.1
IJRISE| www.ijrise.org|editor@ijrise.org[125-129]
Fig 3.1 Seed Block Algorithm Architecture
B .SBA Algorithm
The seed block algorithm is as follows:
Initialization: Main Cloud :Mc ;Remote Server:Rs ; Clients of Main Cloud: Ci ; Files:a1 and a2 ;
Seed block: Si ; Random Number: r ; Client’s ID: client_id
Input : a1 created by Ci ; r is generated at Mc; Output: Recovered file a1 after deletion at Mc;
Given: Authenticated clients could allow uploading, Downloading and do modification on its own the files only.
Step 1: Generate a random number. int r = rand( );
Step 2: Create a seed Block Si for each Ci and StoreSi at Rs .Si = r ⨁client_id ( Repeat step 2 for all clients) Step 3: If Ci creates/modifies a1 and stores at Mc
, then a2 create as a2 =a1 ⨁ Si
Step 4: Store a2 at Rs .
Step 5: If server crashes a1 deleted from Mc, then, we do EXOR to retrieve the original a1 as: a1= a2 ⨁ Si
Step 6: Return a1 to Ci .
IJRISE| www.ijrise.org|editor@ijrise.org[125-129]
4.
PROPOSED OUTCOME
To achieve the objective of this paper, the following techniques are proposed.While user uploads the file into the cloud , the signcryption (digital signature + encryption) is done for the user’s data, that is digital signature(SHA-256) is used for user authentication and encryption(AES) is used for providing security for the user’s data. Then by using seed block algorithm the copy of the user data is saved in the remote cloud.
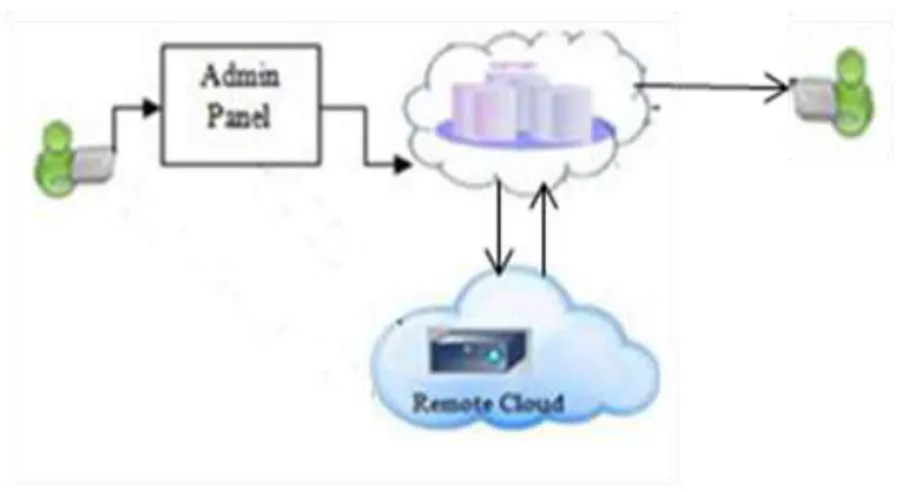
Fig 4.1.Architecture of remote data backup
The Fig 4.1 shows the architecture of the remote data backup server. As shown in Fig 4.1 the data owner gets registered to the main cloud for the data storage with the admin permission who provides the unique key to the data owner so that the privacy is persevered. The admin provides the keys for the data owner which helps him to generate digital signature. Later the signcrypted file is uploaded on the main cloud by verifying the signature. The copy of file is stored on the remote cloud and SBA is applied. If data in the main cloud is lost due to any reason, then the data can be retrieved from the remote cloud. Later , as per the request the file is sent to the receiver who will decrypt the data to get the original file.
5. EXPERIMENTATION AND RESULT ANALYSIS
Fig.5.1 Graph Showing Processor Utilization
The Fig 5.1 shows the CPU utilization at Main Cloud and Remote Server. As shown in Fig 5.1he Main Cloud’s CPU utilization starts with 0% and as per the client uploads the file onto it then utilization increases; such that it has to check whether the client is authenticated or not, at the same the time it send request to Remote Server for the corresponding Seed Block. When request is reached to Remote Server the algorithm starts collecting the details and gives response in form of the seed Block and during this period, the load at Main Cloud decreases which in return causes gradual decreases in CPU utilization at main cloud. After receiving the requested data, the CPU utilization at main cloud increases as it has to perform the EXORed operation. Again the Final EXORed file is sent to Remote Server.
IJRISE| www.ijrise.org|editor@ijrise.org[125-129]
6.SNAPSHOTS
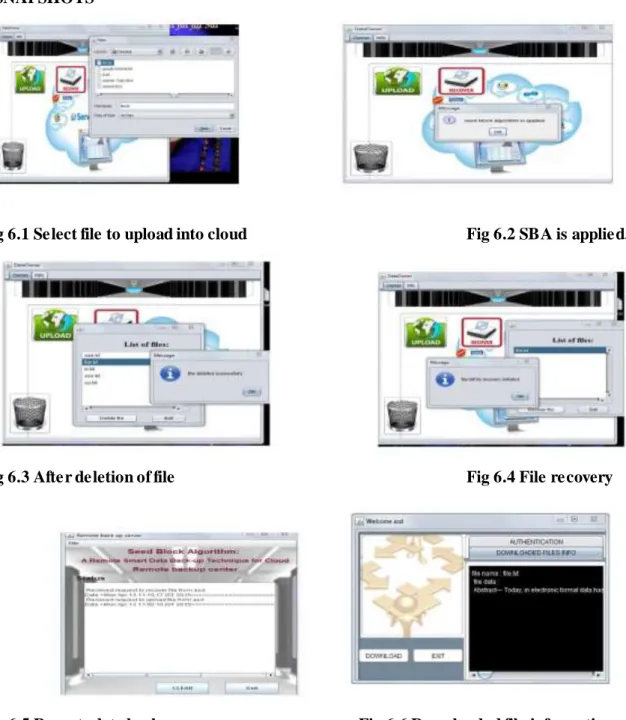
Fig 6.1 Select file to upload into cloud
Fig 6.2 SBA is applied.
Fig 6.3 After deletion of file
Fig 6.4 File recovery
Fig 6.5 Remote data backup server
Fig 6.6 Downloaded file information
The above figures show how the data can be recovered even after the deletion in the cloud and sharing of data to another user. In Fig 6.1, the data owner selects the file and uploads into cloud. In Fig 6.2, after verifying the signature ,file is uploaded into cloud and SBA algorithm is applied. In Fig 6.3, the uploaded file is deleted. The deleted file is recovered shown in Fig 6.4. In Fig 6.5, the details of uploaded, deleted and recovered file will be shown. The Fig 6.6 shows how the user can download the file and the file information7. CONCLUSION
In this paper, we presented detail design of proposed SBA algorithm. The Proposed SBA is potent in helping the users to collect information from any remote location and also to recover the files in case of the file deletion or if the cloud gets destroyed due to any reason. A signcryption technique to perform a smart remote data backup is proposed in this paper.
IJRISE| www.ijrise.org|editor@ijrise.org[125-129]
REFERENCES
[1] Chiwon Song, Sungmin Park, Dongwook Kim, Sooyong Kang, 2011, “Parity Cloud Service: A Privacy -Protected Personal Data Recovery Service,” International Joint Conference of IEEE TrustCom-11/IEEE ICESS-11/FCST-1
[2] Vijaykumar Javaraiah, Brocade Advanced Networks and Telecommunication systems (ANTS), 2011,“Backupforcloud and Disaster Recovery for Consumers and SMBs,” IEEE 5th International Con ference, 2011.
[3] Yoichiro Ueno, Noriharu Miyaho, Shuichi Suzuki,Muzai Gakuendai, Inzai-shi, Chiba,Kazuo Ichihara, 2010, “Performance Evaluation of a Disaster Recovery System and Practical Network System Applications,” Fifth International Conference on Systems and Networks Communications, pp 256-259.
[4] Giuseppe Pirr´o, Paolo Trunfio , Domenico Talia, Paolo Missier and Carole Goble, 2010, “ERGOT: A Semantic-based System for Service Discovery in Distributed Infrastructures,” 10th IEEE/ACM International Conference on Cluster, Cloud and Grid Computing.
[5] Lili Sun, Jianwei An, Yang Yang, Ming Zeng, 2011, “Recovery Strategies for Service Composition in Dynamic Network,” International Conference on Cloud and Service Computing.
[6] Kalyani Bangale, Nivedita Gupta, Swati Singh Parihar, “Remote Data Collection Server : E-Health Care” International Journal of Innovative Research in Computer and Communication Engineering, An ISO 3297: 2007 Certified Organization, Vol. 2, Issue 2, February 2014.
[7] Eleni Palkopoulouy, Dominic A. Schupke, Thomas Bauscherty, 2011,“Recovery Time Analysis for the Shared Backup Router Resources (SBRR) Architecture”, IEEE ICC.
[8] Sheheryar Malik, Fabrice Huet, December 2011, “Virtual Cloud: Rent Out the Rented Resources," 6th International Conference on Internet Technology and Secure Transactions,11-14 ,Abu Dhabi, United Arab Emirates.
[9] Kruti Sharma, Kavita R Singh, “Online Data Back-up and Disaster Recovery Techniques in Cloud Computing: A Review” ISSN: 2277-3754 ISO 9001:2008 Certified International Journal of Engineering and Innovative Technology (IJEIT) Volume 2, Issue 5, November 2012.