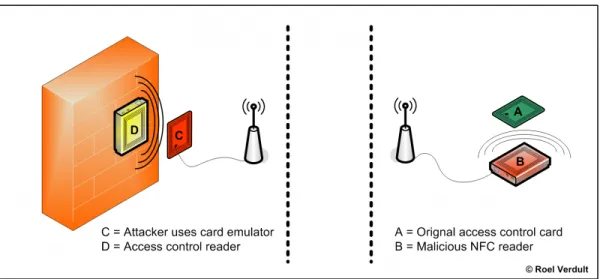
A Relay Prevention Technique for Near Field Communication
Full text
Figure

![Figure 1.1: NFC Forum specifications for peer-to-peer mode, reader/writer mode and card emulation mode [17]](https://thumb-us.123doks.com/thumbv2/123dok_us/80902.2509179/15.918.230.713.133.385/figure-nfc-forum-specifications-peer-reader-writer-emulation.webp)
![Table 1.1: Maximum downlink eavesdropping ranges for BER of 0.1% [39].](https://thumb-us.123doks.com/thumbv2/123dok_us/80902.2509179/19.918.267.683.314.493/table-maximum-downlink-eavesdropping-ranges-ber.webp)
![Table 1.3: Maximum uplink eavesdropping ranges for BER of 0.1% [39].](https://thumb-us.123doks.com/thumbv2/123dok_us/80902.2509179/20.918.280.673.131.311/table-maximum-uplink-eavesdropping-ranges-ber.webp)
Outline
Related documents
Post hoc com- parison of program types with Fisher’s least squares difference (LSD) test showed that those admitted to supported living programs tended to be younger at time of
In Shaik Mastan Bi v, Shaik Bikari Sahab which was a Sunni case, the Andhra Pradesh High Court held that although a Hanafi Muslim cannot make a gratuitous transfer of
Figure 6(I) shows the next sequence from the kata in which the right hand performs a knife hand block (a), is brought to the chambered position, and then used for
For a certain reaction, xM yL, the rate of reaction increases by 4 times when the concentration of M is doubled... Among similar reactions, the endothermic reaction has
The purpose of this research is to examine student teachers’ personal beliefs as well as their cooperating teachers’ personal beliefs about children and developmentally appropriate
Social work qualifications comprises both the bachelor’s and master’s degrees (the Act on Qualification Requirements for Social Welfare Professionals 272/2005; 3§) - working
© 2006 by Carnegie Mellon University March 2006 Executive Strategy Seminar - Module 3 - 9 The PSP Course PSP0 •Current process •Basic measures PSP1 •Size estimating •Test
The CA certificate called Trustis FPS Root CA should be installed in the Trusted Root Certification Authorities tab, and the Issuing Authority certificate called Trustis..