AppCon: Mitigating evasion attacks to ML cyber detectors
Full text
Figure


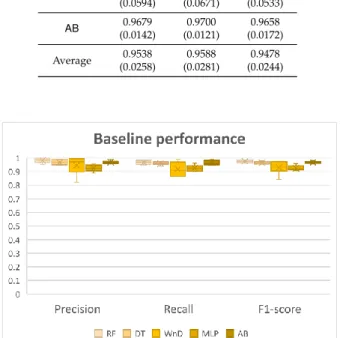
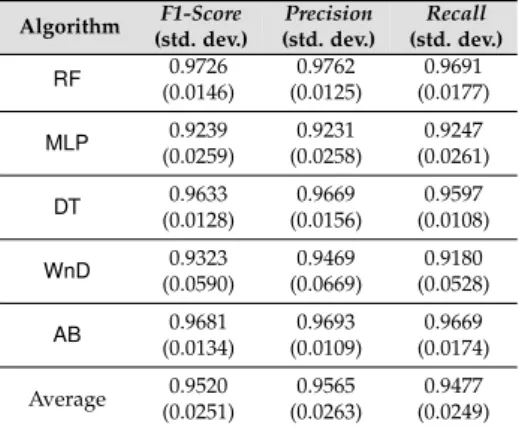
![Table 2. Meaningful metrics of the CTU-13 datasets, Source: [24].](https://thumb-us.123doks.com/thumbv2/123dok_us/9956364.2488191/8.892.117.770.159.376/table-meaningful-metrics-ctu-datasets-source.webp)
Related documents
Promotions and suvs, national term rental cars and should i drive my rental experience for your needs at participating locations across the best long term specials.. Pennsylvania
Lycopodium provided preliminary and detailed design, cost estimating, procurement and construction management services for Orica Australia in the upgrade of their Hydrochloric
2.8 the models weights ( w and w m), representing the contribution of each feature (here voxel) for the decision function or predictive model can be explicitly computed and plotted
for all Classes 10% per annum of the return of the relevant Class of Share in accordance with the High Watermark (calculated as the return necessary since the start of the quarter
The theme of his address was “A New Heart for a New Church.” The new bishop said United Methodists must learn to love each other and work for the common good of the church?.
Keywords: disorder of consciousness, resting state, functional magnetic resonance imaging, BOLD signal, transfer entropy, partial correlation, functional connectivity, brain
CollabXMind leverages on XMind [14], a single-user Rich Client Application [15] for mind mapping, and on CAFE, part of CoFFEE suite [16], to provide functionalities to
The empirical model we test features forward-looking firms who pre-set prices for a cou- ple of periods ahead, using Calvo (1983) pricing rule.. We also estimate a hy- brid version
![Table 4. Groups of altered features, Source: [18].](https://thumb-us.123doks.com/thumbv2/123dok_us/9956364.2488191/10.892.297.589.887.1127/table-groups-of-altered-features-source.webp)
![Table 5. Increment steps of each feature for generating realistic adversarial samples, Source: [18].](https://thumb-us.123doks.com/thumbv2/123dok_us/9956364.2488191/11.892.279.606.382.542/table-increment-feature-generating-realistic-adversarial-samples-source.webp)