A Robust Trust Aware Secure Intrusion Detection for MANETs
Full text
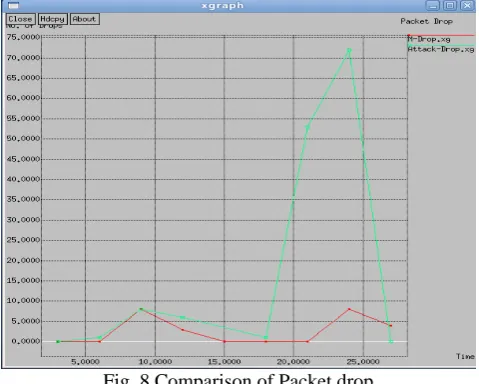
Figure



Related documents
The antithesis appears in the second half of the verse in the source text: I bow down to the holy humus, / In this virgin land something is chewing, / Hey, sky-high weeds, / So
• The sourcing device must see the defined constant load current as the discovery voltage increases from 3 volts to 80% of the maximum output. • At the operating voltage minus 10%
The birth of cryptocurrency (or “virtual currency”) kickstarted a new era for technology, banking, and finance. The United States Government Accountability Office defines
age phosphor plate assembly comprises at least one storage phosphor plate comprising a storage phosphor layer for storing X-ray information and a substrate layer on which
Groundwater/Soil monitoring template Lic No: P0577-03 Year 2013 Surface water EQS Groundwater regulations GTV's Drinking water (private supply) standards Groundwater
Greater mobility results in increased productivity because it allows users to have access to all of their computing resources, files and other content regardless of their
The study aimed to implement a HSC and investigate the feasibility , acceptability, and improvement in the quality of patient han doff communication and improvement of nurse
Dickinson (1995) found that individuals with positive perceptions of classroom or school environment enhance their learning and motivation by adapting mastery