Advanced Re-Encryption Technique And Verification Process In Cloud Computing
Full text
Figure
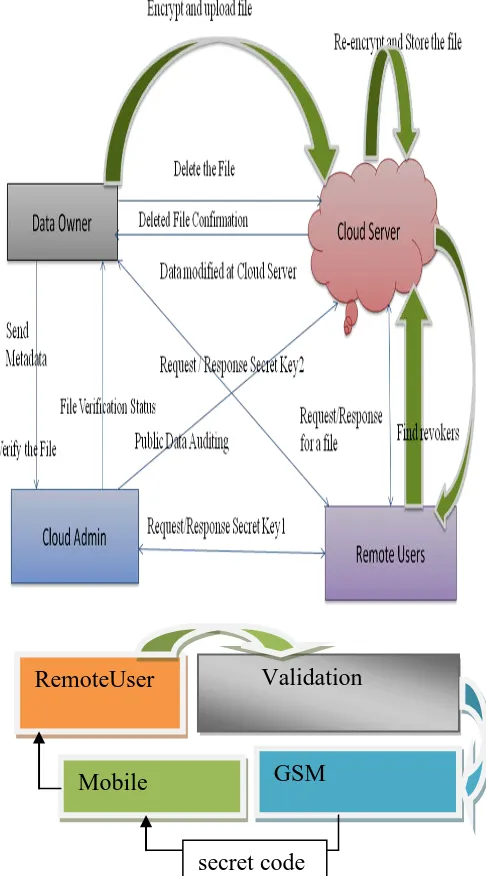
Related documents
In this work, it is shown that the PI controller designed on the basis of the plant model, linearized about a particular operating point, cannot handle the plant
The highly detailed 3-D city model derived by means of multi-source high resolution remote sensing data (cf. 4) is used as basis for inferring time-dependent population distribution
In this cross-sectional analysis of lung function from a na- tionally representative sample of US Asian population, we showed that the GLI-2012 reference equations for individ- uals
choice between different plant genotypes, an oviposition preference towards the transgenic plants. was observed in most cases except for the LeCCD1-2 tomato-cabbage looper
One of the objec- report the sequence of a total of 13 kb of the three sero- tives of the current study was to assess the effect of differ- tonin receptors in 200 nearly isogenic
To evaluate the effect of Pycnogenol® on ADHD and ADD behaviour and comorbid physical and psychiatric symptoms, as well as on immunity, oxidative damage, antioxidant status
There is limited research on health literacy and other study variables (e.g.,healthy.. dietary patterns, perceived risk of future stroke, accuracy of perceived risk of future.