Elliptic Curve Cryptography in JavaScript
Full text
Figure
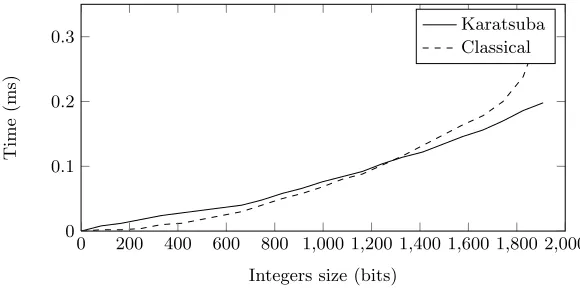
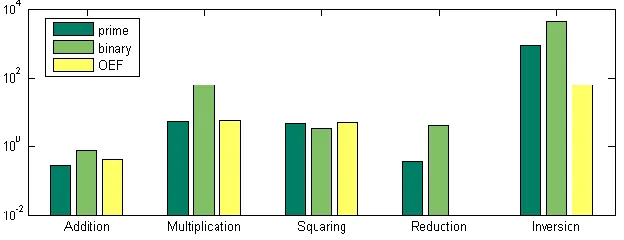
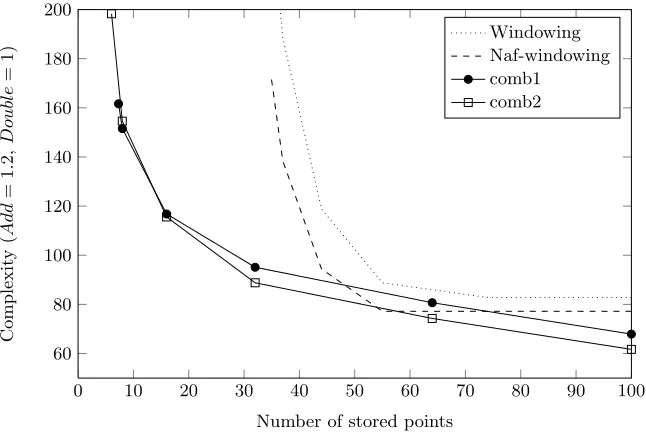
Related documents
The cloud and shadow detection is done using window based thresholding approach [5] by considering hypothesis that, regions of the image covered by clouds
Contour-SURF feature extraction and matching technique all along with a matching practice are given for the contour based shape detection.. The algorithm automatically extracts
We propose a method for systematically sparsifying radial basis function kernels such that the resulting kernel is compactly supported, and hence has a sparse Gram matrixA.
Figure 5.17 Comparison of Spectral Radiance from EAST, CEA-NEQAIR, and CEA- NEQAIR (large artificial impurity addition) in the Ultraviolet Spectrum.. 39 Figure 5.18 Comparison
A test structure satisfying these specifications was designed and fabricated for experimental testing (Figures 3.2, 3.3). The base of this test structure features a lip for
ABSTRACT : Tall concrete buildings experience time-dependent axial shortening which may be interpreted as either absolute or differential, the former being with respect to a
The proposed method extract color and texture based on super pixel in multiresolution domain which is conceptual simple since wavelet transform play an important
Hepatotoxicity associated with antiretroviral therapy in adults infected with human immunodeficiency virus and the role of hepatitis C or B virus infection. Hepatitis