Cryptographic Role-based Security Mechanisms based on Role-Key Hierarchy
Full text
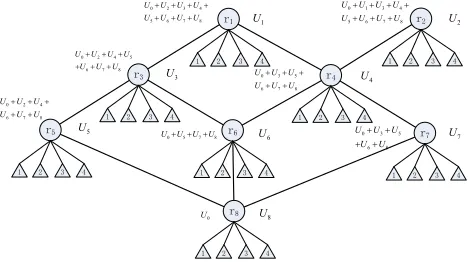
Figure




Related documents
Each year, FastCasual.com hosts the Fast Casual Executive Summit – a live business networking and social event where Fast Casual restaurant executives meet up to exchange ideas
Although both trajectory clustering and segment clustering compute a sequence of segments from a sensor stream, they are different in the following way: Segment
Sector of activity: Heating, ventilation, air-conditioning and refrigeration systems, controls, services and sustainable solutions for residential, commercial, industrial, food
However, these points are not reliable enough to be used in ICP registration if the capture points are far from each other because two possible sources of errors exist: errors in
CA No hold conference - autodial Combined feature, not supported -- CCOS Controlled class of service Change COR Access Code FAC CFW Call forward all calls
Hypothesis 4b: Increased levels of organizational constraints aggregated to the unit-level (Level 2) will be associated with individual-level (Level 1) decreased supervisor-rated
Games and Practices With Associated Injury Rates by National Collegiate Athletic Association Division and Season, Women’s Lacrosse, 1988–1989 Through 2003–2004*.. Total Games