Ethical Hacking Techniques with Penetration Testing
Full text
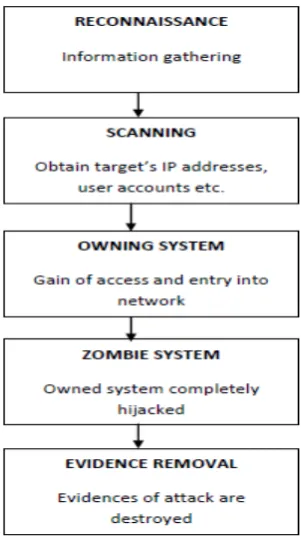
Figure


Related documents
I should like, particularly, to acknowledge my indebted ness to the Baptist Missionary Society, the Church Missionary Society, the London Missionary Society, the
Development, Journal of the European Economic Association, Journal of the Japanese & International Economies, Journal of Macroeconomics, Journal of Public Economics,
This paper examines a trial of a new online method of course delivery, using a CD-ROM as the basis of materials provision, communication and interaction, for a group of Thai
Cannot be used with other discount or coupon or prior purchases after 30 days from original purchase with original receipt.. Offer good while
on the study of the acceleration of the body is considered to be valid and reliable for predicting the risk of falling or for discriminating between population groups with
Analysis of the flavonoid profiles of a large sample set of mānuka honeys gave a mean total flavonoid 374. content of 1.16 mg/100g of honey with pinobanksin, pinocembrin, luteolin
For cylinder blocks without separate bearing plates, refer to section Bearing Plates (page 8) to locate the sealing land surfaces on the cylinder block running surface..
Virtual Network Operator – entity that utilizes virtualized network components, residing in a tenant domain of a Hosting Network Service Provider data center, to offer