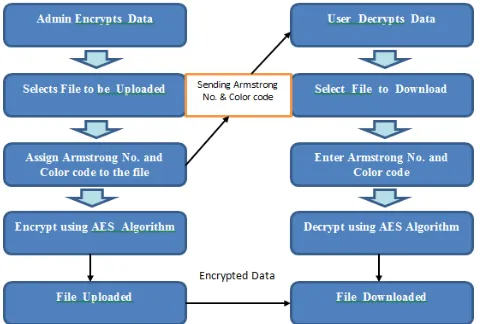
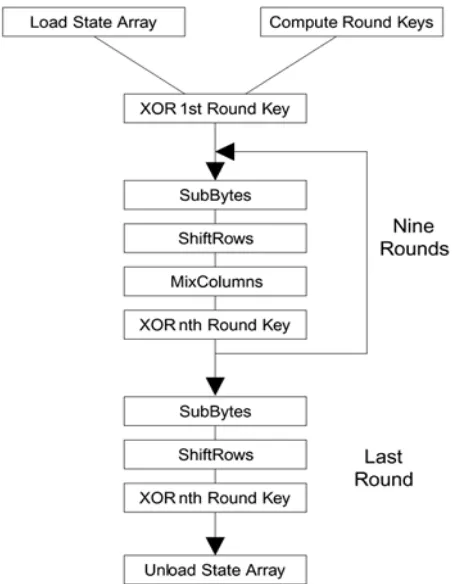
User Authentication Using Color and Secure Message Transmission Using Armstrong Number
Full text
Figure
Related documents
in Shaffer v. Heitner 4 stated applied to all assertions of jurisdiction, does not apply to the exercise of jurisdiction over a non-resident defendant served in the forum
Expression of genes encoding three zinc efflux systems, zntA , zntB , and zitB (Fig. 2A, blue), and two zinc acquisition systems, znuABC and zupT (Fig.. At 5 min
Citing Sherman v. First National Bank, 26 Garcia v. Bennett, 28 the Texas Supreme Court adopted the evidentiary standard that, when reviewing a no evidence basis
A534V substitution resulted in impaired processing of RRV nonstructural polyprotein and in elevated production of replicase-generated pathogen-associated molecular pattern (PAMP)
The United States Supreme Court held that the totality of the circum- stances surrounding a hearsay statement will be examined to determine whether the proponent
noted, however, that compliance with the contract conditions may have evi- dentiary relevance to the tort action since the basis of an action for breach of the duty of
54 Although a few courts have approved of such liability based largely upon an aiding and abetting rationale, 5 " the majority of courts have rejected the
As with any contract, valid consideration must support a noncompetition covenant. 5 ' If a covenant not to compete is ancillary to a valid agreement, that agreement