Cloud Security Mechanism : Prevent Access with Location
Full text
Figure
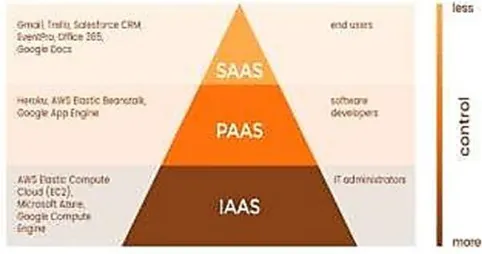



Related documents
Daniel Construction Co.' 4 and concluded that the grounds for its determinations as to the basis of indemnification for one's own negligence were equally compelling for
A negative GRABS score for a mutant indicates cells with reduced stiffness and growth in 1% agarose that is slower than that of wild-type cells (again, when the growth rates of
"Because the Court of Military Appeals has held that our cases construing the Fifth Amendment right to counsel apply to military interrogations and control
Rule 52(b) of the Texas Rules of Appellate Procedure provides in pertinent part as follows: When the court excludes evidence, the party offering same shall soon
The results thus far show that bacterial growth rate is reduced when the tufB operon is translo- cated to chromosomal locations that are more distant from the origin of replication
In conclusion, we propose that hyphal growth is initiated inside acidic phagosomes (albeit at a reduced rate) and that alkalinization results from excessive membrane distension,
After trial of this matter, the district court ruled asbestos-containing waste was not property under the MCA, and therefore, the TRC did not have jurisdiction to
We conclude that binding of the periplasmic domain of FtsB to FtsQ in the absence of FtsL involves only FtsB residues 64 to 87 as shown by the structure, and this interaction can