Mehammed Daoui, Mustapha Lalam, Abdelaziz M’zoughi, Baouz Djamah, Malika Belkadi, Rachida Aoudjit Department of Computer Science University Mouloud Mammeri, Tizi-Ouzou
1
Introduction
Movement prediction allows for the anticipation of users’ displacements in order to determine future lo-cations that they will cross. Several applilo-cations can profit from this prediction. Highway management, transportation planning, and location-based services are examples of fields that can be made more effective with movement prediction. Cellular networks constitute the domain where prediction is used to manage communications resources and improve quality of service. For example, if cell sites a mobile user will cross in the future are known, the network can anticipate these movements and, in advance, reserve within these sites the necessary resources for the mobile user.
Mobile displacements are difficult to predict with good accuracy. Several studies have been undertaken on mobility prediction techniques; however, their results have not always been satisfactory because of the complex characteristics of displacement.
We present in this chapter a new prediction strategy for mobile users in cellular networks based on their displacement history and on a system based on an Ant System. This solution is adapted to current microcell and picocell environments with small-sized cells. The Ant System allows highly accurate prediction of users’ displacement for a given mobile, even without sufficient history.
2
Background
There have been many studies focused on prediction. In [Zhuang et al., 1998], Zhuang et al. monitored signal power in a base station to predict the next cell. When the signal in a new base station increases in power, the system concludes that the mobile user is moving towards this station. This solution was improved in [L.Hsu & Wang, 1999] by adding a time factor to predict the arrival time of the mobile group. In [Choi et al., 2000a], Choi et al. estimated users’ mobility according to displacement history observed in each cell. In [Shen et al., 2000], Shen et al. developed a prediction system based on the measurement of a pilot signal, and used fuzzy logic to take into account interferences from pilot signals and random movements of users. In [Ashrook & T.Staruer, 2002], the authors used mobile localization information recovered through GPS, which they provided to a Markov model to predict the user’s future location. In [Soh et al., 2003], Soh et al. presented and described the use of a prediction technique that incorporates road topographic information wherein the mobile periodically (every second for example) provides its position to its base
station. An algorithm identifies the segment of the road taken by the mobile user and the user’s estimated speed. The system then predicts the future base station and estimates the expected time to reach it.
These solutions are limited because they are based on either a probabilistic model that does not com-pletely reflect the users’ behavior, or on the individual history of users, which can be incomplete or insuf-ficient. New solutions based on heuristic methods were used such as those presented in [Liou & Lu, 2003, Capka & Boutaba, 2004] which used neural networks for prediction. In [Liou & Lu, 2003], the authors adopted a structure of a cell divided in two-tier areas (A ’vicinity area’ and ’an edge area’). When the mobile user is at the edge area of a cell, its coordinates are provided as input to the neural network, which predicts the next cell to be visited. In [Capka & Boutaba, 2004], the authors presented a system that period-ically captures the connections’ traces. These traces are progressively recorded to create a historical record that is used as input to the neural network to predict the next cell to be visited.
The disadvantage of these methods is that they require a long training phase dealing with mobile users’ behavior before the prediction could succeed. Moreover, a mobile user can change his behavior during the training phase or go to a location he has never visited before, rendering the prediction ineffective.
In [Samaan & Karmouch, 2005], Samaan et al. presented a solution that includes spatial and user con-texts. The spatial context consists of a set of abstract maps describing the geographical environment in which the mobile user progresses. Places, buildings, and roads that lead to these places are described in these maps. The user context includes a set of information related to the mobile user making it possible to predict his mobility. This information is then combined using Dempster-Shafer algorithm to predict future mobile location.
Even if this solution appears to provide suitable results when mobile history is lacking, it is too con-straining as it requires additional information that is difficult to acquire and likely to change frequently.
In [Franc¸ois & Leduc, 2005], the authors suggested a method based on information theory in which each mobile device collects a set of clues, such as its position in a particular road and the amount of time it stayed during its previous displacements. These clues are then processed by the current cell to predict future cells. The use of information theory and decision trees allows choosing the most relevant clues for prediction. Its disadvantage is the need to store these clues in the mobile phone itself, which consumes memory, energy, and bandwidth when this information is communicated to the cell.
3
Motivations
The difficulty of making predictions is primarily due to the complex character governing user movements. These movements are sometimes random or regular, and seem to adopt common characteristics with other users. If we observe, for example, the displacements of a user who goes to work every day, one can note that these displacements are regular. If we observe a tourist’s displacements, then they seem random. However, if we observe displacements of vehicles on a highway, we notice that they adopt a common character. These displacements are often generated by socio-economic needs and governed by the topography of the locations and infrastructures such as workplaces, roads, and shopping malls, among others.
A study to better organize public transport conducted in the United States [Hu & Young, 1994] has shown that nearly 80% of users’ displacements relate to work and nearly 20% relate to social or cultural reasons. Holidays account for only approximately 2%. It has also shown that displacements are influenced by infrastructure (highways, streets, paths, and so on). Displacements for work and social reasons are the most frequent and the most usual reasons cited. Roads leading to workplaces are often common, and users’ journeys are regular. Displacements for reasons other than work (purchases, distractions, and others) are less common though usual, and displacements for holidays are the most dispersed.
The knowledge of the history (habits) of a user and his current location (on a road, for example) could be useful in determining his probable future location. Let us assume that we have a set of cells, each one respectively covering a residential district, a stadium, a university residence, a university campus, a workplace, and segments of a highway (figure 1.a). If a user with history (i.e., wherein we already know the practices of displacements) is located in a residential district on a working day, and if it is known that he usually takes the highway to go to work, then it is very probable that the future cells are those that cover the highway and the workplace. In the same manner, if the user is in the workplace, we can predict that the future cells will be those covering the highway in direction of his residential district.
The same assumption applies to students with history who spend the majority of their time between the university residence and the campus. If a student is in the university residence, there is a strong chance that his next destination is the campus. Except on Sundays, when he may prefer to go to the stadium, for example, instead of the campus.
It is also possible to determine the user’s future location even if his history is not known or if he makes an unusual displacement (such as during holidays, for example). In this case, one can use the history of his neighbors who are going in the same direction (figure 1.a). A user who is on a highway surely goes in the same direction as his neighbors. In the same way, a new student will frequently move between the city, the campus, and the stadium, similar to his fellow students.
Figure 1:Principle of the prediction.
An ant’s displacement resembles those of a human. They are influenced by social behavior. Ants choose common roads to convey food. These roads are also influenced by the place topography. It is more likely that an ant will take a familiar road, or the same road as its neighbor, to go from its nest to the food source. This resemblance motivated our use of an Ant System to model the behavior of a mobile user and to extrapolate future displacements. The goal is not to find optimal roads, but to represent, in a certain way; locations frequently attended by a mobile user and his displacements habits, and then extrapolate future displacements from this information. The knowledge of displacement history of the mobile user and of his neighbors, and application of the ant system’s basic formulae, allow for this modeling. Before detailing our solution, we provide some basic information regarding Ant Systems in the following section.
4
Ant Systems
Ant systems appeared in the work of Dorigo and A. Colorni [Dorigo & Colorni, 1996] towards the end of 90s. In this founder article, they elaborated on a new approach for combinative stochastic optimization and highlighted their method’s speed in finding acceptable solutions while avoiding premature convergence. Op-timization through an ants’ colony is inspired by the behavior of ants during their search for food. They show other ants the way using a volatile chemical substance known as a pheromone. An isolated ant generally moves at random. While moving, it deposits a quantity of pheromones on its trail. Other ants that come after this ant will choose the most attractive way (the one with highest pheromone intensity). When an ant follows a path, it reinforces the trail by adding its own pheromones. The result is a collective behavior, the end of which results in making the track more attractive, with a higher number of ants following it.
To illustrate this behavior, let us consider the experiment shown in Figure 2. A set of ants move along a straight line from their nest, A, towards a food source, B (figure 2.a). At a given moment, an obstacle is placed across the way so that one side (C) is longer than the other (D) (Figure 2.b). The ants will thus have to decide which direction they will take: either C or D. The first ants will choose a random direction and will deposit pheromone along the way. Those that choose way ADB (or BDA) will arrive first at the end of the obstacle (depositing more pheromone in that way) than those that will choose way ACB (or BCA). The choice of the ants that follow is then influenced by the pheromone intensity that stimulates them to choose the way ADB rather than the way ACB (Figure 2.c). The ants will then find the shortest way between the nest and the food source.
Figure 2:Behavior of ants in search of food.
This system is modeled using simple and autonomous agents representing artificial ants. In this artificial system, time is seen as discrete and ants are not completely blind. They have a visibility field that affects their displacement. In general, at one point, i, and at one moment, t, an ant chooses the point j (i.e., to follow the path(i,j)), according to the following probability:
Pi,j(t) =
(τi,j(t))α·(ηi,j)β
∑(i,k)∈C(τi,k(t))α·(ηi,k)β
(1) Where:
• ηi,j: is the ant’s visibility field on the path(i,j)(the ant assumes that there is food at the end of this
path).
• αandβ: are the parameters which control the relative importance of the pheromone intensity compared
to ant’s visibility field.
• C: represent the set of the possible paths starting from point i. ((i,k)is a path ofC) .
Each ant ’a’following the path(i,j)adds a quantity of pheromone represented by∆τi,aj. As pheromone
is a substance that evaporates, the intensity of pheromone on the path(i,j)at time (t+1)is equal to that which remains after evaporation at time t, added to the sum of quantities deposited by all ants that followed this path at time t. This is given by:
τi,j(t+1) =σ·τi,j(t) + m
∑
a=1 ∆τai,j (2) Where:• σis a coefficient such as(1−σ)represents pheromone evaporation between timestandt+1. It must be<1 to avoid pheromone accumulation and premature convergence [Dorigo & Colorni, 1996].
• arepresents an ant having deposited a quantity of pheromone on the path(i,j).
• mis the number of ants having taken the path(i,j)at time t.
Several problems were solved using this method. These problems belong to various domains and their models differ from one problem to another [Wang et al., 2005, Tian et al., 2003, Bichot, 2004].
5
Presentation of the Solution
Displacements of mobile users are modeled by displacements of an ant colony going from a current cell towards adjacent cells looking for food. During their search, the ants will prefer to visit the usual cells of the mobile or of its neighbors who are going in the same direction. The prediction algorithm is carried out in four steps, as indicated in Figure 3.
5.1 Displacements memorization
Memorization of old displacements was conducted on each cell every time a mobile crosses it. For this purpose, we used a history having the structure given in Figure 4, which was inspired by the one presented in [Choi et al., 2000b].where:
• Mobile Id: is a unique mobile identifier which can be: Pin code, Mac address or other.
• Period: allows the distinction between a working day (0) and a public holiday (1).
• Source cell: indicates the cell from which the mobile came.
• Destination cell: indicates the cell towards which the mobile is going (at the moment when the dis-placement is carried out).
Figure 3:Execution steps of the prediction algorithm.
Figure 4:Structure of a history entry.
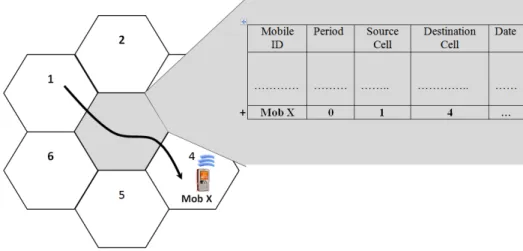
For example, if a mobile user moves from Cell 1 to 4 via the cell at the center (Figure 5), the center cell will memorize this displacement by adding a new input to its history. This new input will contain the mobile identifier, the period when the displacement was conducted, the source cell, the destination cell, and the displacement date.
The Date field is used to locate too-old displacements and remove them from the cache. We also added a period field to allow the distinction between working days and public holidays because the mobile user’s behavior changes according to the considered case.
5.2 Movements table creation
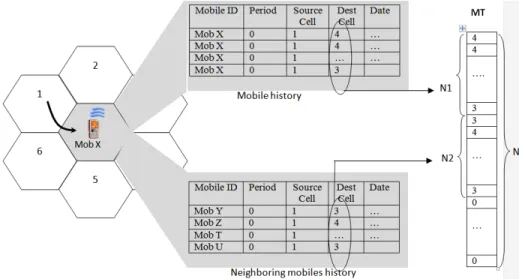
When a mobile reaches a cell, the base station creates an N-entries table called Movement Table (MT). This table is filled with the mobile’s most recent historic entries corresponding to the same source cell and the same period (let N1 be the number of such entries). The table will be fed to cells towards which the mobile had moved in the past.
IfN1<N, the system fills the table using N2 entries corresponding to other mobiles having the same mobility profile (i.e., mobiles with the same source cell and the same period) (Figure 6). IfN1+N2<N, null entries are added.
The N1 first entries of the movement table describe the behavior of the mobile user itself. They enable us to take into account the user’s habits. The next N2 entries describe the behavior of adjacent mobile users going in the same direction. They allow displacements prediction for a mobile user through the behavior of its neighbors (as in a highway, for example).
Figure 6:Creation of the movements table.
5.3 Ant colony creation
The ant colony was created using the movements table, as indicated in Figure 7. Each line of this table corresponds to an ant and contains two fields: a visibility and pheromone fields. The field ”Pheromone” represents the quantity of pheromones that the ant will deposit in adjacent cells during its search for food. It is equal to a constantQ>0. The visibility field is represented by a vectorηof six elements corresponding
to the number of adjacent cells. An element of this vector represents ant visibility of an adjacent cell. It is initialized by multiplying the value of the element by a factor µ>1 in order to increase its attraction compared to other elements, in order that the ant will be predisposed to prefer an already visited cell when it searches for food.
Ifηi,krepresents the visibility of the cellKfor antnai, we have: ηai,k=
X ifMTi(Destination cell)6=kor ifMTiis null X·µ ifMTi(Destination cell) =k
(3) where:
Figure 7:Creation of the movements table.
• K=1to Rrepresents the adjacent cells.
• X is a value>0.
• µ>1 to increase the cell degree of visibility if it was already visited by the mobile.
• MTirepresents the entryI of the movement table.
5.4 Prediction
Future cell prediction proceeds in a set of iterations in which each ant moves towards an adjacent cell and deposits the quantity Q of pheromones in this cell to encourage other ants to go towards it. It then returns towards its nest (i.e., the current cell) in order to repeat the same process. Each ant chooses the future cell according to the degree of visibility and pheromone intensity of the cell.
At the momentt, the antsaichooses to go to the cellKaccording to the probability: Pai,k(t) =
(τk(t))α·(ηai,k)β
∑Rj=1(τj(t))α·(ηai,j)β
(4)
After each iteration (time t + 1), pheromone intensity in locations is updated according to the ants’ contribution and evaporation rate. For each Cell K, we have
τk(t+1) =τk(t)·(1−σ) +m·Q (5)
Where:
• σ,(0<σ<1): represents pheromone evaporation rate. A small value ofσgenerates slow pheromone
dissipation and a high value generates a faster dissipation
• m: represent the number of ants that choose locationk
At the end of this process, the ants will converge towards the cell having the most pheromone. This will be the predicted cell.
6
Solution Evaluation
Our solution is a heuristic approach that has the advantage of better reproducing the behavior of users. It mainly offers the advantage of not requiring tedious calculations, as in the case of neurons networks during their learning phase. Moreover, it quickly reacts to changes in the mobility habits of a user. For example, if the ants modify their route because of an obstacle, the model will adapt to this new situation following pheromone evaporation on the old path to pheromone accumulation on the new path.
The main advantage of our solution is its ability to integrate the behavior of a mobile user, the existing infrastructure, and the behavior of other mobile users in the prediction process, especially in the following cases:
• A mobile user carries out usual displacements: The N1 first lines of its movements table will influence other users to choose the location he habitually visits. This is due to the visibility range coefficient(X· µ)at the start of the algorithm and to pheromone intensity that will accumulate during next iterations. If the mobile user takes a road with high frequentation, the prediction will be improved by N2 other mobile users’ entries, which will accelerate the algorithm’s convergence. If the path taken is not of a high frequentation (small road) or if the mobile users do not move in the same direction, this does not induce a prediction error because the ants will likely choose different locations and their pheromone will quickly dissipate.
• A mobile user is in a new location that he has never visited. This means that the mobile user does not have any history for this location (N1 = 0). In this case, the prediction will be guided by the history of other mobile users (N2 entries in the movements table) and indirectly by the cell infrastructure. For example, If the mobile user is on a highway, the future location will be predicted based on other mobile users that move in the same direction.
Objectivity of our solution was ensured by a double evaluation. The first consists of estimating the pre-diction accuracy. Prepre-diction accuracy is an indicator of performance given by the ratio between the number of correct predictions and the number of all predictions. We employed a trace of realistic displacements generated using the model described in [Scourias & Kunz, 1999]. Based on [Daoui et al., 2008], the results presented show prediction accuracy up to 85% in the case of a mobile user with history, and up to 75% in the case of a mobile user without history.
We also evaluated the performance of our solution in the context of resources reservation in a cellular communication network. We simulated a strategy of reservation resting on our prediction algorithm, and compared it with three common strategies: solution without reservation, static reservation, and dynamic reservation.
The reservation protocol evaluation was conducted on the basis of two parameters: Probability of Call Blocking (PCB) and Probability of Handoff Blocking (PHB). PCB provides the probability that a new call is blocked because of lack of resources. It is the ratio between the number of new calls blocked to the number of all calls. PHB calculates the probability that a call in progress is broken because of handoff (cell change generally due to mobile user displacements).
From a quality of service point of view, it is preferable to keep the PHB as low as possible even to the detriment of PCB. This is because cutting off an existing communication is more damaging than temporary unavailability to carry out new communication. Thus, the idea to reserve resources within future cells that a mobile will visit was formed.
Solutions without reservation (SR) do not reserve resources. Static reservation or reservation by guard channel (CD) permanently reserves 10% of the cell bandwidth capacity for handoffs. Dynamic reservation
(DR) dynamically reserves resources for a mobile user in adjacent cells. Our protocol, dynamic reservation with prediction (RDP), reserves resources only in predicted future cells using a prediction algorithm.
Figure 8:PHB evaluation.
Figure 8 provides the probability of handoff blocking for the four protocols according to network load in terms of number of users. We noticed that our solution produced less handoff blocking, which could be attributed to resources reservation in the predicted cells. Dynamic reservation also produces few instances of handoffs blocking. Static reservation and the solution without reservation are the least powerful.
Figure 9:PCB evaluation.
Figure 9 provides the probability of new-call blocking for the four protocols. The solution without reser-vation produced less calls blocking because new calls are treated as handoffs. Our solution approached the solution without reservation when the number of users increased. Dynamic reservation and static reservation were less effective.
These results show that our prediction algorithm used for resources reservation will considerably reduce the probability of handoff blocking and will thus ensure a better continuity of service.
7
Conclusion
The solution we have presented allows for correct prediction of movements up to 85% by employing the history of a mobile user. This solution also predicts up to 75% of displacements for mobiles that do not have any history. The prediction accuracy can be improved by refining the cell’s decomposition. A cell
must contain a place in which users adopt a common and deterministic displacement profile, such as roads, streets, and highways. This makes it possible to have information that is more relevant in the cache and thus improve prediction accuracy. Cellular architecture evolution towards the use of increasingly small cells will reinforce our algorithm efficiency.
Our simulations showed that the integration of our prediction algorithm in resources reservation pro-tocol considerably reduces the probability of handoff blocking with little effect on probability of new-call blocking.
In the future, it would be interesting to study the impact of our prediction algorithm in other fields such as localization, road traffic planning, and as a decision-making aid in general.
References
[Ashrook & T.Staruer, 2002] Ashrook, D. & T.Staruer (2002). Learning significant locations and predicting user movement with gps. InProceedings of the 6th International Symposium on Wearable Computers TSWC’02.
[Bichot, 2004] Bichot, C. E. (2004).Optimisation du d´ecoupage de l’espace a´erien par colonie de fourmis. Technical report, Ecole Doctorale Syst`emes (EDSYS, CENA/ENAC).
[Capka & Boutaba, 2004] Capka, J. & Boutaba, R. (2004). Mobility prediction in wireless networks using neural networks. In International Federation for Information Proceeding, IFIP2004.
[Choi et al., 2000a] Choi, C. H., Kim, M. L., & Kim, S. J. (2000a). Adaptive bandwidth reservation mechanism using mobility probability in mobile multimedia computing environment.IEEE2000.
[Choi et al., 2000b] Choi, C. H., Kim, M. L., & Kim, S. J. (2000b). Adaptive bandwidth reservation mechanism using mobility probability in mobile multimedia computing environment.IEEE2000.
[Daoui et al., 2008] Daoui, M., M’zoughi, A., Lalam, M., Belkadi, M., & Aoudjit, R. (2008). Mobility prediction based on an ant system.Computer Communications, 31, 3090–3097.
[Dorigo & Colorni, 1996] Dorigo, M. & Colorni, A. (1996). The ant system: Optimisation by a colony of cooperating agents.IEEE Transactions on Systems, Man, and Cybernitics-part B, 26(1), 1–13.
[Franc¸ois & Leduc, 2005] Franc¸ois, J. M. & Leduc, G. (2005). Entropy-based knowledge spreading and application to mobility prediction. InACM CoNEXT’05Toulouse, France.
[Hu & Young, 1994] Hu, P. & Young, J. (1994). 1990 Nationwide Personal Transportation Survey (NPTS). Office of Highway Information Management.
[L.Hsu & Wang, 1999] L.Hsu, R. P. & Wang, S. P. (1999). Maintaining quality of service (qos) during handoff in cellular system with movement prediction schemes.IEEE.
[Liou & Lu, 2003] Liou, S. & Lu, H. (2003). Applied neural network for location prediction and resource reservation scheme. In Wireless Network, Proceedings of ICCT’03.
[Samaan & Karmouch, 2005] Samaan, N. & Karmouch, A. (2005). A mobility perdiction architecture based on contextual knowl-edge and conceptual maps.IEEE transactions on mobile computing, 4(6).
[Scourias & Kunz, 1999] Scourias, J. & Kunz, T. (1999). An activity-based mobility model and location management simulation framework. In2nd ACM Int. Workshop on Modeling, Analysis and Simulation of Wireless and Mobile Systems (MSWiM)(pp. 6168).
[Shen et al., 2000] Shen, X., Mark, J. W., & Ye, J. (2000). User mobility profile prediction: An adaptive fuzzy interference ap-proach.Wireless Network, 6, 362–374.
[Soh et al., 2003] Soh, W., Hyong, & Kim, S. (2003). Qos provisioning in cellular networks based on mobility prediction tech-niques.IEEE Communication Magazine, (pp. 86–92).
[Tian et al., 2003] Tian, Y., Song, J., Yao, D., & Hu, J. (2003). Dynamic vehicle routing problem using hybrid ant system. In Intelligent Transportation Systems Proceedings(pp. 970–974).
[Wang et al., 2005] Wang, G., Gong, W., & Kastner, R. (2005). Instruction scheduling using max/min ant system optimization. In Proc. of the 15th ACM Great Lakes symposium on VLSI(pp. 44–49). Chicago, Illinois, USA.
[Zhuang et al., 1998] Zhuang, W., Chua, K., & Jiang, S. M. (1998). Measurement-based dynamic bandwidth reservation scheme for handoff in mobile multimedia networks. InIEEE International Conference on Universal Personal Communications, ICUPC ’98., volume 1 (pp. 311 – 315).