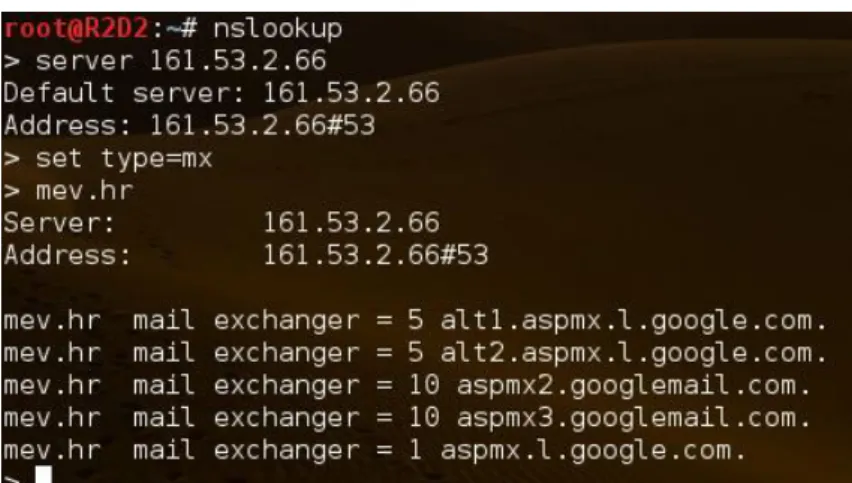
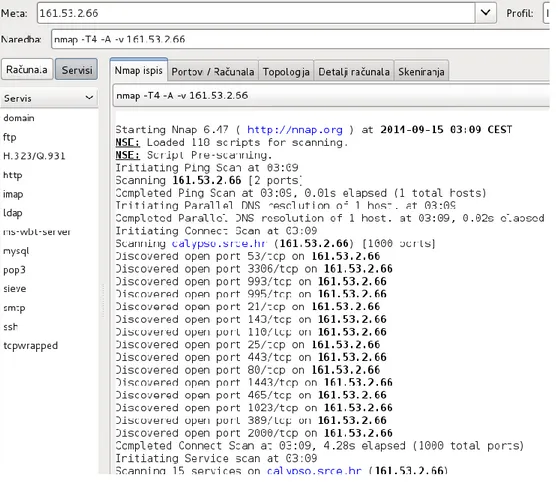
Intrusion into the computer networks and information systems
Full text
Figure
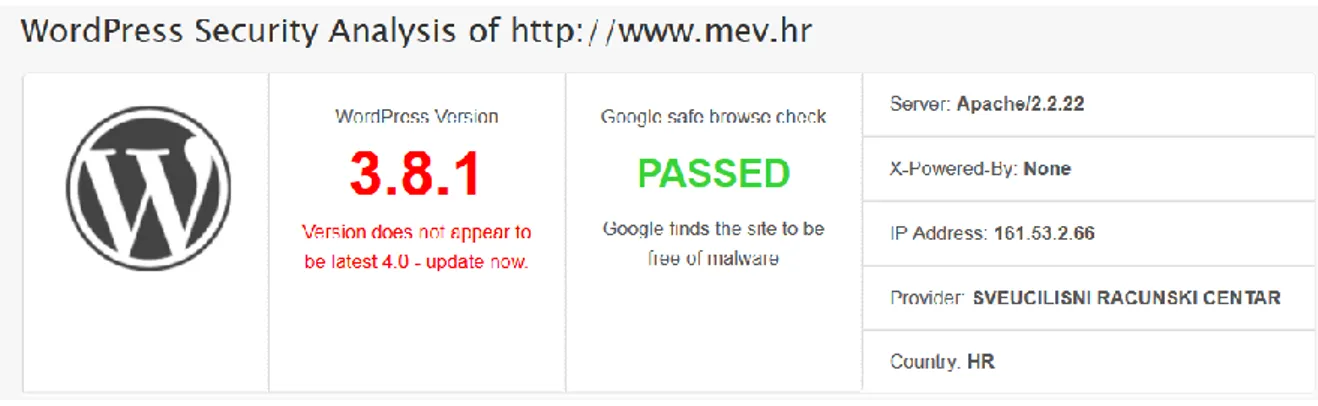
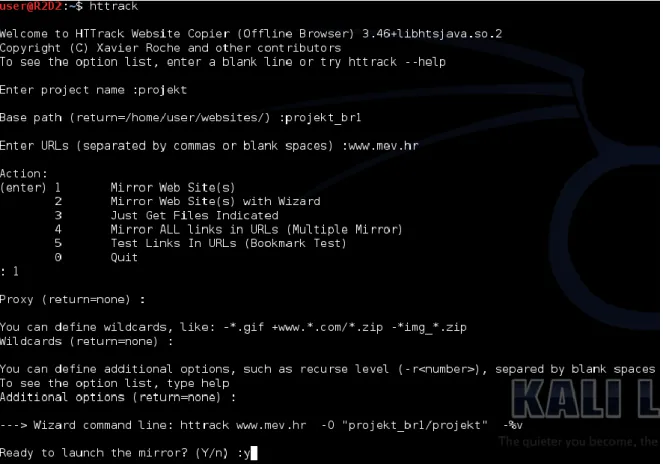
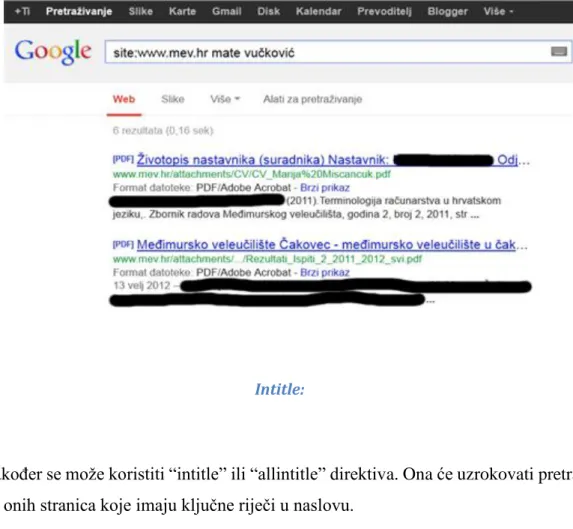
Related documents
(However, the receipt type is regarded as the single/double + addition mode receipt type.) • Only the top logo is printed on the first part of the double receipt and the
This study investigated the mineral and proximate composition of Golden/canary melon ( Cucumis melo ) seeds and the physiochemical properties of the seed oil.. Proximate
Although the process the Jesuit Education Foundation went through with Horizon 2020 is documented in the collection Transforming Education (Aragay et al., 2015c), an
Coherently with the socio-cognitive theory of moral agency (Bandura, 1999) and with the socio-ecological model of bullying (Swearer & Doll, 2001), we propose that
unRAID je operativni sustav baziran na Linux-u. Originalno je obavljao dužnosti mrežnog skladišta podataka, ali je u novijim verzijama dobio mogućnosti kao što su
The primary purpose of this quantitative study was to assess whether there is a predictive relationship between students’ content area final exam scores in naturopathic basic
The cur- rent debate about the tree interactions in near-natural beech forests and their role in emergent forest structures and dynamics led to the research questions if (1)
Diagnostics 2 nd Generation MW injection / power measurements Movable 2D Langmuir probe 2 Mach probes Optical fiber PMT or Spectrometer. Line integrating telescope or local