Privacy aware reversible watermarking in cloud computing environments
Full text
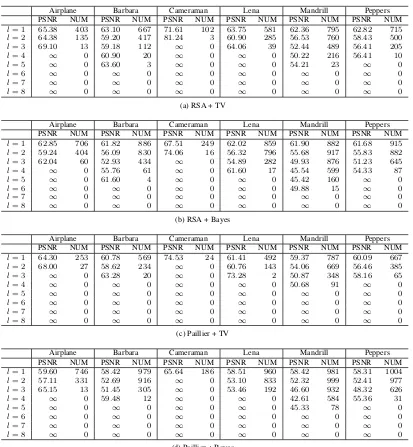
Figure



Related documents
ACORD Standards Program Activity Implementation Report Page 6 The Australia/New Zealand GI (ANZGI) Working Groups are listed below in alphabetic order:.. Joint Life and GI
A 41-year-old multigravida with a history of esophageal squamous cell cancer treated with esophagectomy and perioperative chemotherapy was diagnosed with local recurrent carcinoma
The new security functions, especially for the access via the internet, can be applied to existing systems by using interfaces with the new KNX security mechanisms... The advantage
• e2e Operations Management SON security dashboard shows real-time state of the corporate infrastructure including the B2B integration points. • Distributed
Results further indicate that migrating to XML-based authority and bibliographic records, applying controlled-vocabulary tools such as Simple Knowledge Organizations Systems (SKOS)
Specialist Pool Health Entity Specialist Bonus Reserves PCP Hospital 20% of Surplus 20% of Surplus 23% of Premium 80% × Fee Schedule* 50% of Surplus Withhold Pool 20% × Fee
Some states may impose tax on lease payments based on where the lease was executed , rather than where the leased property is used.. Complex
In accordance with our requirements as highlighted by the Civil Contingencies Act (2004) and the Operating Framework for 2010/2011, this is to give the Board an update on the