Building the State and the Nation in Kosovo and East TimorAfter Conflict
Full text
Figure
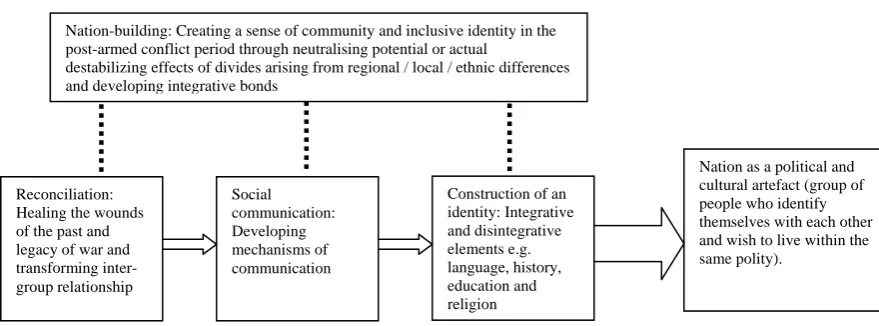
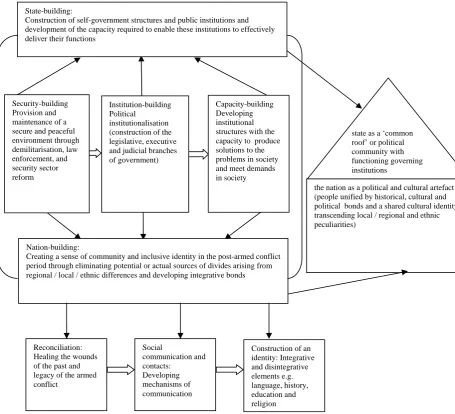
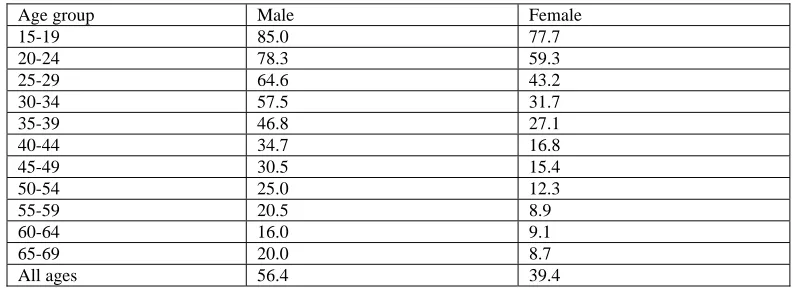
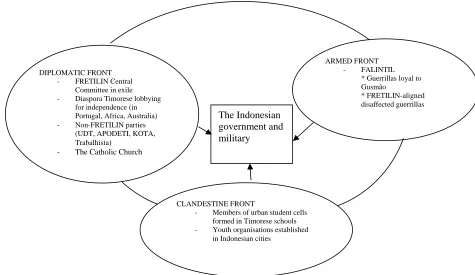
Outline
Related documents
The formal deñnition of VCGen is outside the scope of this paper (it can be found in [2]). Intuitively, the veriñcation condition is a conjunction of boolean expressions
This will earn China a steady flow of energy resources, it will secure Chinese presence in new markets, it will secure commercial/supply routes throughout the Indian Ocean
Commercial aircraft programs inventory included the following amounts related to the 747 program: $448 of deferred production costs at December 31, 2011, net of previously
Accordingly, we explored general practitioners ’ , hospital physicians ’ and non-physicians ’ (1) radiation knowledge, (2) weighting of radiation dose when referring, (3) use
This essay asserts that to effectively degrade and ultimately destroy the Islamic State of Iraq and Syria (ISIS), and to topple the Bashar al-Assad’s regime, the international
National Conference on Technical Vocational Education, Training and Skills Development: A Roadmap for Empowerment (Dec. 2008): Ministry of Human Resource Development, Department
Results suggest that the probability of under-educated employment is higher among low skilled recent migrants and that the over-education risk is higher among high skilled
Analogously to Hardware Security Modules in the physical world, our architecture segregates the management and storage of cloud clients’ keys as well as all cryptographic
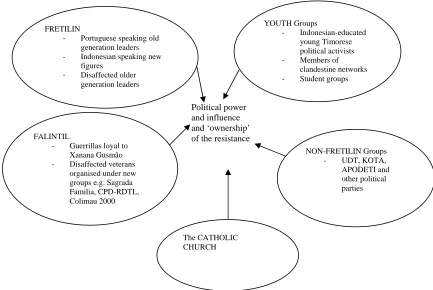

![Table 4.6. Indigenous languages of Timor-Leste (Data compiled from Hull, “The Languages of East Timor: Some Basic Facts”, Instituto Nacional de Linguística Universidade Nacional Timor Lorosa’e [The National Linguistic Institute of the National University of East Timor], 1999, revised on 24/08/2004;](https://thumb-us.123doks.com/thumbv2/123dok_us/21993.502045/157.612.111.540.70.442/indigenous-languages-instituto-linguistica-universidade-linguistic-institute-university.webp)

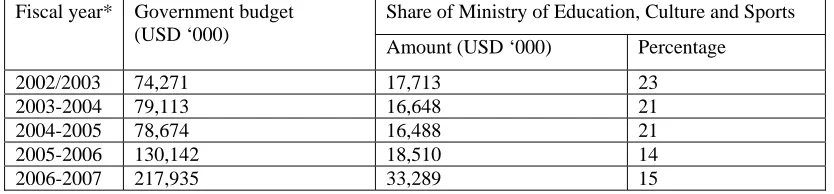
![Table 4.9. Ministry of Education of Timor-Leste and World Bank estimates of schools, teachers and students enrolled in Timor-Leste (Adapted from World Bank website, on 26 November 2006])](https://thumb-us.123doks.com/thumbv2/123dok_us/21993.502045/168.612.107.548.70.220/ministry-education-estimates-teachers-students-enrolled-adapted-november.webp)