Mobile Ad-hoc for Enterprise Level Security
Full text
Figure
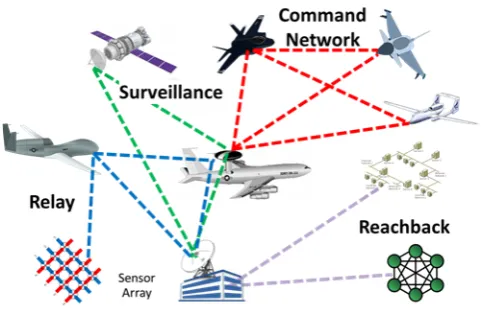
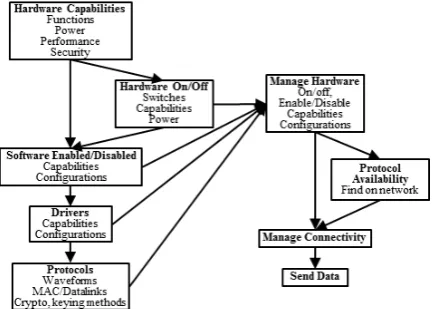
Related documents
Thermal Design Power introduced by Intel Corporation to reduce the heat energy produced by processor chip while running the application or system in working condition.. The
All minority 5-year age groups increased by at least 35 percent from 2000 to 2010, whereas some White non-Hispanic 5-year age groups lost population and children under 5 had
affect consumer demand for goods and services (Table 1). These spending differences generally ref lect the size, composition, lifestyle, and income of those
While their discussion of static tasks is comprehensive and offers many useful real-world examples, our taxonomy offers a system- atic way to specify the possible permutations of
In the present paper, data are presented which show that (1) the centrifuga- tion effect is highly significant even after the effect of other controllable post-
Existing approaches to phantom protection in B trees (namely, key range locking) cannot be applied to multidimensional data structures since they rely on a total order over the
These include changing how C is allocated in fixed and dynamic schemes based on data from current forest syntheses and different parameterization of allocation schemes for
There has been sharp disagreement among courts about whether the IRC and FDCPA constitute applicable law under Section 544(b) of the Bankruptcy Code, such that the creditor