A New Chaos Based Image Encryption and Decryption using a Hash Function
Full text
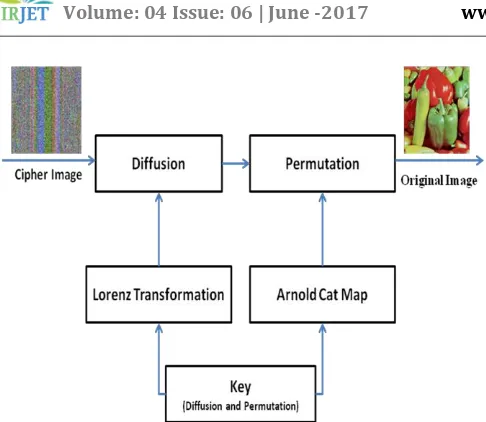
Figure


Related documents
In this design, the PIC microcontroller is used as a gateway communicate to the various sensors such as temperature sensor, heartbeat sensor, ECG sensor, sensor
The test results revealed that 15% of cement can be optimally replaced by red mud beyond which compressive strength, split tensile and flexural strength
Following what entomologists understand about honey bee disease, I hypothesize that there will be an increase in observed morbidity factors in colonies located where available
We examine relationships between fame and premature mortality and test how such relationships vary with type of performer (eg, solo or band member) and nationality and whether cause
The overrepresentation of males and minority students within special education classrooms is worrisome and has led to the hunt for an alternative method within schools that
Semantic-sensitive Namespace Management in Large-scale File Systems. Many document frameworks depend
On the hand if the traffic is present on the road R2 then the control is sent to state S2 which switches on the signal on road R2 to green and rest of the signals are