Personal identification based on mobile based keystroke dynamics
Full text
Figure


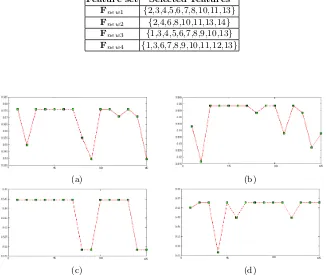
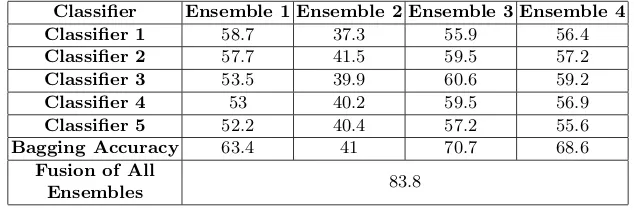
Related documents
As the monitoring location is upstream to the domestic waste water discharge points to Koel River, the water quality at the monitoring location remains at the Class C level..
Fuzzy modeling results: As mentioned previously, in the implementation phase of fuzzy system, 7 variables information technology, organizational culture, auditing
Therefore, agency theory predicts that high level of ownership concentration which reflects shareholders’ control on the firm will increase the level of leverage in the
This is a rare case of carcinoma ex pleomorphic adenoma of the antrum with an unusual malignant component of squamous cell carcinoma.. The SCC component has
Befu, Harumi. “Nationalism and Nihonjinron” in Cultural Nationalism in East Asia. Representation and Identity edited by Harumi Befu, 107-135. Berkeley: University of
The national health priority areas are disease prevention, mitigation and control; health education, promotion, environmental health and nutrition; governance, coord-
Porter и Millar (1985) сметаат дека информациските технологи, па според тоа и интернетот може да придонесе за создавање на конкурентска предност преку нов