An Efficient Encryption Schemes based on Hyper-Elliptic Curve Cryptosystem
Full text
Figure
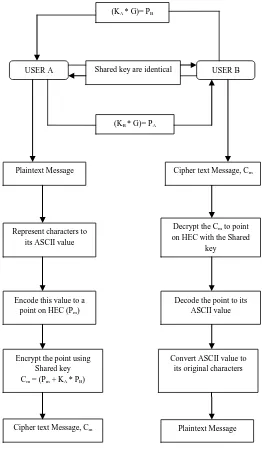
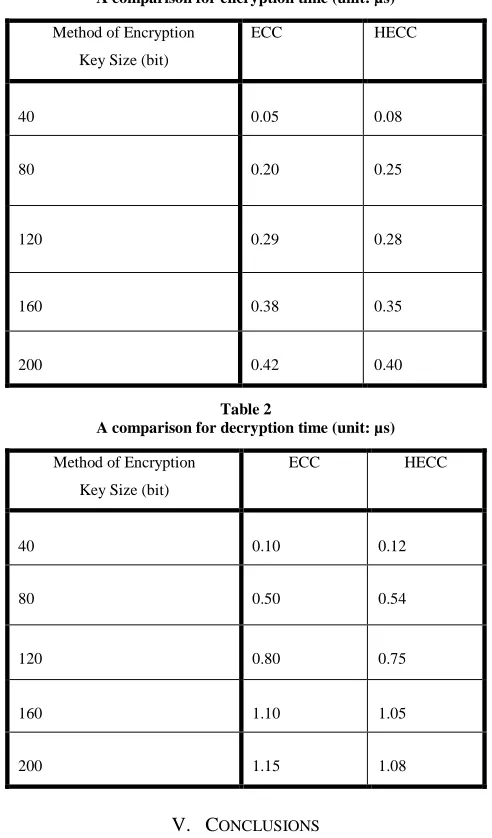
Related documents
The NVM converter was designed with the goal that any pointer pointing to an object should be converted to a relative pointer. Also, a global array of primitive or non-primitive
nonexpression due to 2-bp insertion 3 stop codon C5 Recurrent neisserial infections CH50, RID, ELISA, C5 function Point mutation 3 stop codon C6 Recurrent neisserial infections
Chapter 2 reviews previous studies on online health services, the current situation of online services offered by Malaysian private hospitals, prior studies on
(iv) To integrate aforementioned data structure, loading algorithm and culling technique with the chosen triangle-based LOD technique into the real-time terrain visualization
From the table it can be proved that the pore with meso size has been formed by delamination process of PREFER to ITQ-6 leads to material with higher external surface.. ITQ- 6
Resonant soft X-ray reflectivity and scattering (R-SoXR and R-SoXS) are used to investi- gate the interfacial and bulk nanomorphology of organic electronics including organic
1 (a) Geometry of SET, (b) Equivalent circuit of SET consisting of tunnel and non-tunnel junctions with ideal voltage sources, (c) SET with double islands.. distribution in
It is this researchers opinion that these standards should address adaptation from face-to-face to cybersupervision standards in the following areas; (a) using effective