Analysis on Security Evaluation of Pattern Classifiers under Attack
Full text
Figure
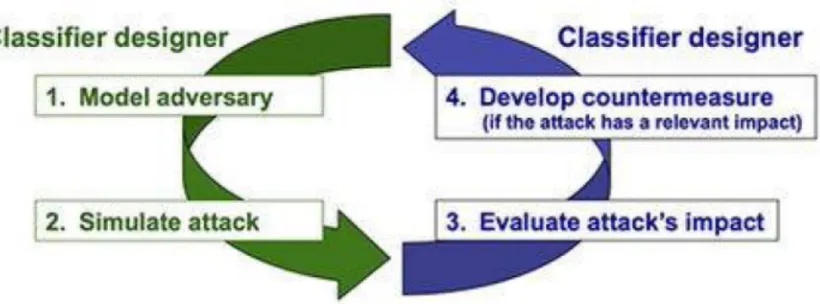
Related documents
• Maintenance free AC traction and steering motors, CAN-Bus technology and Access 1-2-3 comprehensive control system guarantee high energy efficiency and uptime,
Finally, in Tables 4-6 the results for the output power and the idler power, calculated using the UFE and the NU-PWr models, are compared for both the dysprosium trivalent
However; as I spent more time in the literature, it seemed as though the most relevant literature was that of supportive communication which led me to my initial research question
PHT material.The stress field is compared with the SSY solution at different deformation levels for different a/W ratios.Figure 6 shows the typical variation of ‘Q’ with distance
ABSTRACT : Benzothiazole derivatives are known to have wide spectrum of therapeutic activities such as antitumor activity, antimicrobial activity, anti-inflammatory activity,
This study has been able to establish that cocoa powder has a beneficial effect on the feed and water in-take, body weight and fasting blood glucose of normal and
We analyze notions of security against key recovery attacks and security against distinguishing attacks, and then construct a scheme which is WKR-SCA-secure and IND-secure, but
This section explains the proposed encryption based compression scheme. The input image is decomposed by means of optimized DWT and the resultant approximate and