2017 International Conference on Electronic and Information Technology (ICEIT 2017) ISBN: 978-1-60595-526-1
A Practical Single Sign-on Protocol for Web-based Cloud
Computing Services Using Channel Bindings
Ling XIONG
1, Tu PENG
2, Hong-bin LIANG
3,*and Dai-yuan PENG
11
School of Information Science and Technology, Southwest Jiaotong University, Chengdu, China
2
School of Software, Beijing Institute of Technology, Beijin, China 3
School of Transportation and Logistics, Southwest Jiaotong University, Chengdu, China
*Corresponding author
Keywords: Cloud computing, Single sign-on, Transport layer security, Channel bindings.
Abstract. In practice, web-based single sign-on(SSO) protocols, such as OpenID, SAML, and OAuth, have been widely used in cloud computing services due to its convenience to users. However, these SSO authentication schemes require a fully trusted third party to help achieve mutual authentication, which makes the trusted third party being a bottleneck of security. Moreover, they do not protect users’ privacy: the trusted third party learn at which service a user logs in. To address these issues, in this work, we design an efficient and provably secure SSO protocol based on identity-based authentication using a secure channel binding, such as Transport Layer Security (TLS). The proposed SSO scheme can achieve mutual authentication without the help of the trust third party. Furthermore, our scheme can resist against various kinds of attacks and is able to provide user privacy.
Introduction
Cloud computing is based on various kinds of exposing resources over the internet which provides shared computer processing resources and data to computers and other devices on demand[1]. There are many services of cloud computing, such as data storage, data management, medical system, etc. In practice, users access these cloud-based services through web browsers, such as HTTP or HTTPS. To access these different cloud services, the user needs to log in each service provider with different identities and passwords according to traditional authentication schemes. Thus, the user needs to manage many identities and passwords. Single sign-on(SSO) schemes have been introduced into cloud service environment to address this problem[2,3].
and service providers in every authentication process will leak users’ privacy. Therefore, if the first problem is resolved, the second problem would not exist.
In this paper, we present an SSO protocol without the help of trusted third party based on identity-based authentication and the latest TLS standard. This proposed scheme achieves mutual authentication and establishes secure channel by combining TLS with SSO. Besides, our scheme can resist various attack.
The Proposed Scheme
Initialization Phase
In the initialization phase, registration center(RC) chooses an additive group of point G
with order q, and P is a generator of G. RC generates the system private key sk and calculates PK=sk⋅P . Then RC chooses five secure hash functions
* * 4 3 1
0,h,h ,h :{0,1} Zq
h → , :{0,1}* {0,1,2,...,255}
2 →
h . RC publishes the system parameters
{G,q,P,PK,h0,h1,h2,h3,h4}.
User Registration Phase
When the user Ui wants to access a service provider, he/she needs to register in RC first. The process of registration is as follows.
(1) Ui selects identity IDi and password PWi, generates a random number bi. Then Ui computes Ci=h0(IDi||PWi||bi), Ui transmits {IDi,Ci} to RC through a secure channel. (2) RC checks whether IDiexists in the user information table, if it exists, RC rejects this request. Otherwise, RC generates a random number ui and computes Xi=ui⋅P,
) || (
1 IDi Xi
h
IDU= , Ei=ui+sk⋅IDUmodq, Fi =Ei⊕Ci,Vi=h3(h2(Ci)). After that, RC
updates the user identity information table with new entry {IDi}, stores {Xi,Fi,Vi} into smart card SCi, and sends SCi to Ui.
(3) After receiving SCi form RC, Ui stores bi into SCi.
Authentication Phase
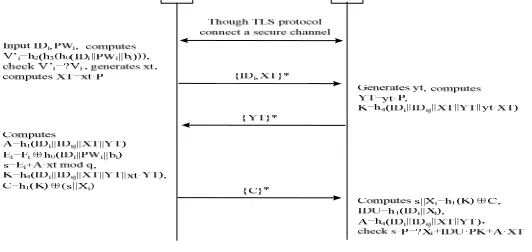
[image:2.612.173.439.515.641.2]When Ui wants to login the service provider Sj, Ui needs to access to Sj through TLS. Then, Ui and Sj establish a secure channel and Sj has been authenticated to Ui though TLS protocol. As shown in Fig. 1, the process of authentication is as follows.
Figure 1. The user authentication phase.
(1) Ui inputs IDi and PWi into smart card SCi. SCi computes Ci=h0(IDi||PWi||bi),
)) ( ( 3
2 i
i h h C
V′= , and checks whether V′iand Vi are equal. If not, SCi terminate the session.
Otherwise, SCi generates a random number xt∈Zq*, and computes XT =xt⋅P. Then Ui
(2) Sj generates a random number yt∈Zq* , and computes YT= yt⋅P , ) || || || || (
4 ID ID XT YT yt XT
h
K= i Sj ⋅ . Sj sends YT on the secure channel to Ui. (Note. In
practical, there is no need to generate random number yt and compute YT for Sj, because it can use the temporary random number for Diffie-Hellman in TLS.)
(3) After receiving the message, Ui computes A=h1(IDi||IDSj||XT||YT),
i i
i F C
E = ⊕ , s=Ei+A⋅xtmodq,K=h4(IDi||IDSj||XT||YT||xt⋅YT), ( ) ( || )
1 K s Xi
h
C= ⊕ .
Then Ui transmits C on the secure channel to Sj.
(4) Sj computes s||Xi=h1(K)⊕C, IDU=h1(IDi||Xi), A=h1(IDi||IDSj||XT||YT)and
checks whether s⋅P=Xi+IDU⋅PK+A⋅XT is established. If not, Sj fails to authenticate the user Ui, and the session is terminated. Otherwise, Sj verifies Ui successful.
Password Update Phase
When the user Ui wants to update the password, he/she should run as follows:
(1) Ui inputs IDi, password PWi into smart card SCi. SCi computes )
|| || (
0 i i i
i h ID PW b
C = , Vi′=h2(h3(Ci)), and checks whether Vi′and Vi are equal. If not, the
smart card fails to authenticate Ui, and rejects the request of password update. Otherwise Ui inputs a new password PW*i.
(2) SCi computes C*i=h0(IDi||PW*i||bi),
* *
i i i
i F C C
F = ⊕ ⊕ , ( ( *))
2 3 *
i
i h h C
V = .
(3) Finally, F*i and V*i are stored in the smart card to replace Fi and Vi respectively.
SECURITY ANALYSIS
Security Model
Based on Tsai and Lo’s work 6], we proposed a security model for our scheme. The security of our scheme is defined by a game played by the adversary A and a challenger
ζ. Let instance s U
∏ be the user oracle in session s, s S
∏ be the service provider oracle in
session s. A can make following oracle queries.
hi(mi): This query simulates hash function. When A ask the query mi, ζ
generates a random *
q i Z
h∈ and return hi to A.
Register(IDi): This query simulates A registration as a legitimate user. A issues
identity and receives secret information of smart card.
Send(P,s,P’,M): This query simulates P’ sends message M to s P
∏ . Then the
oracle takes the actions specified by the protocol and outputs a response to A. If M is
null and P is user oracle, it means to create a new instance.
Reveal(IDi): This query simulates the leakage of session key attack, and will output the session key K.
There are three corruption queries:
Corrupt(IDi, PWi):This query simulates password leakage attack, and will output the user password PWi.
Corrupt(IDi, SCi):This query simulates smart card stolen attack, and will
output the secret information stored in smart card.
Corrupt(Sj):This query simulates service provider compromise attack.
Definition 1: Matching sessions: A session in instance s U
∏ and a session in instance
s U
′
∏ are said to be matching if s = s’, pidU = S, pidS = U and both have accepted, where
Definition 2: Secure protocol: we say that our scheme is secure if the following properties hold:
s
U
∏ and s S
∏ are matching session and they accept each other. The probability of s
S
∏ accepted A as s U
∏ is negligible.
The probability of A knew the password is negligible.
Provable Security
To prove the security of our proposed scheme, we assume that our scheme is defined by a game played between the adversary A and a challenger ζ.
Lemma 1. (Secure user authentication): In the proposed scheme Π, if the hash function (h0,h1,h3,h4) are ideal random function and s
S
∏ has accepted, then no polynomial
adversary against the proposed scheme can forge a legal authentication message with a non-negligible probability.
Proof. We assume that the adversary A can forge a legal authentication message with a
non-negligible probability ϵ. Then there is a challenger ζ can solve the DL problem with a non-negligible probability.
Given an instance (P,RK= sk·P) of DL problem, the task of ζ is to compute * q
Z sk∈ .
ζ sends the system parameters {G,q,P,PK,h0,h1,h2,h3,h4} to A. ζ randomly selects a user’s identity IDC as the challenge identity and answers A’s queries as follows:
hi (mi) : The hash query hi(mi), i = 0,1,3,4 maintains a list Lhi initialized empty. ζchecks whether the message mi exists in Lhi. If it exists, ζ returns its value hi to A. Otherwise, ζ generates a random number hi, stores the tuple (mi,hi) into Lhi and returns
hi to A.
Register (IDi): In this query ζ maintains a list LR with initialized empty. When
A asks this query with identity IDi, ζ checks whether the tuple of IDi exists in LR. If it exists, ζ return IDi to A. Otherwise, ζ operates as follows:
If IDi = IDC, ζ generates two random number ui,εi∈Zq*, computes Xi=ui⋅P,
sets h1(IDi||Xi)=εi, Ei=⊥, and stores (IDi,ui,Xi,Ei) and (IDi,Xi,εi) into LR and Lh1 respectively. ζ returns IDi to A.
If IDi ≠ IDC, ζ generates two random number ui,εi∈Zq* , computes
PK
ε
P u
Xi= i⋅ − i⋅ , sets h1(IDi||Xi)=εi, Ei = ui, and stores (IDi,ui,Xi,Ei) and (IDi,Xi,εi) into LR and Lh1 respectively. ζ returns IDi to A.
Send (IDi,s,Sj,M): ζchecks whether IDi = IDC. If they are not equal, ζoperates
according to the specification of the proposed scheme and return the result of response to A. Otherwise, ζ aborts the game.
Send (Sj,s,IDi,M): ζoperates according to the specification of the proposed
scheme and returns the result of response to A.
Reveal (IDi): ζ
returns the session key K of IDi to A. Corrupt (IDi,PWi):ζ returns the password PWi of IDi to A.
Corrupt (IDi,SCi):ζ checks whether IDi and IDC are equal. If not, ζ searches
whether the tuple (IDi,ui,Xi,Ei) in the LR, and returns (Fi,Vi) to A. Corrupt(Sj):ζ returns the state of Sj to A.
where Fi′=Ei⊕h(0 IDC||PWC||b)c . Therefore, the forged authentication messages are
the following two equations:
EC⋅P=XC+εC⋅PK (1)
EC′ ⋅P=XC+εC′ ⋅PK (2)
Based on equations (1) and (2), we derive the following equations:
(EC−EC′)⋅P=(εC−εC′)⋅PK (3)
Therefore,
) (
) (
C C C C
ε ε
E E
′ − ′ −
is the answer to DL problem. We now analyze the
probability of ζsolving the DL problem. We assume that A forges user UC and pass user authentication successfully with non-negligible probability ϵ, and the attack at least once among qs sessions. Therefore the probability of A pass user authentication in this session is ϵ/qs. When we repeat the simulation with a different choice h1, and the attack at least once among qs+1 session. Therefore, the probability that ζcan solve the DL problem is ϵ/qs(qs+1).
It is clear that the probability of ζ solving the DL problem is non-negligible due to ϵ is non-negligible. Obviously, it is a contradicts assumption. Therefore, there is no polynomial adversary can forge a legal authentication message with non-negligible probability.
Theorem 1: The proposed scheme is secure protocol if DL problem is hard.
Proof. Based on Lemma 1, we can know that there is no polynomial adversary can forge a legal user login if DL problem is hard. Besides, if we have asked corrupt (IDi, SCi) query and knew the secret data in the smart card,the probability of the adversary knew the password256/|DPW |, which is negligible. According to the definition 2, the proposed scheme is a secure protocol.
Further Security Analysis of Our Scheme
Resistance to User Impersonation Attack: In our scheme, in order to impersonate as
Ui, the adversary has to generate a valid login request (Fi,PWi), where Fi stored in the device. An adversary who wants to impersonate user Ui must know the user's password and smart card at the same time. If the adversary has obtained one of the two factors, he still does not know any information of another factor. Therefore, our proposed scheme can resist user impersonation attack.
Resistance to Replay Attack: In our improved scheme, we use a random number to prevent the replay attack. The random xt is fresh and different at every authentication.
Therefore, when the user sends login request, it must be the current session, not previous session. So, our scheme can avoid the replay attack.
Two-factor Security: Obviously, the adversary is not able to impersonation user when he only knows the user’s password. On the other hand, suppose the adversary steals the user's smart card and obtain the data (Fi,Vi), Fi=Ei⊕Ci, Vi=h2(h3(Ci)). The
adversary cannot guess the correct password, because there exist |DPW |/256 candidates of password, where |DPW| is the space of password. This is called fuzzy verifier method [9], where the adversary is prevented from obtaining the exacting correct password. Therefore, the proposed scheme can provide two-factor security.
check user login. If the user inputs wrong password PW*i , the smart card will reject user login by checking whether Vi and Vi′=h2(h3(IDi||PWi||bi)) are equal. Therefore,
our scheme can quickly detect unauthorized login/update with the wrong password. Mutual Authentication: Services provider Sj is authentication to Ui based on TLS protocol, which has been proved security. According to the proofs of Theorem 1, there is no polynomial adversary that can forge a legal user authentication message. Thus, the user and the service provider can successfully authenticate each other.
Conclusions
In this paper, based on identity-based authentication we proposed an efficient and provably secure SSO authentication scheme over TLS. The proposed scheme fulfills mutual authentication without the help of RC. Moreover, through the formal security analysis, we have shown that our scheme can resist various known attack and provide more security features.
Acknowledgement
This research wassupported by National Science Foundation of China under Grant number (Grant No. 61502034 and 61571375).
References
[1] P. Mell and T Grance. The NIST Definition of Cloud Computing . National Institute of Standards and Technology: U.S. Department of Commerce. Special publication 2011, pp. 800-145.
[2] S. Ahmad, B. Ehsan, The Cloud Computing Security Secure User Authentication Technique, International Journal of Scientific & Engineering Research, 2013, pp. 2166-2171.
[3] N. Fotiou, A., Machas, G.C. Polyzos, and G. Xylomenos, Access control as a service for the Cloud, Journal of Internet Services and Applications, 2015, pp.1-15.
[4] Microsoft, Windows Live ID. [Online]. Available: https://account.live.com/.
[5] Open ID Foundation, Open ID Authentication 2.0. [Online]. Available:http://openid.net/specs/openid-authentication-2_0.html.
[6] J.L. Tsai and N.W. Lo, A privacy-aware authentication scheme for distributed mobile cloud computing services, IEEE Syst. J. 2015, 9(3),pp.805–815.
[7] Q. Jiang, J.F. Ma, and F.S. Wei, On the Security of a Privacy-Aware Authentication Scheme for Distributed Mobile Cloud Computing Services, IEEE Systems Journal, 2016, pp.1-4.
[8] D. Fett, R. Küsters, and G. Schmitz, SPRESSO: A Secure, Privacy -Respecting Single Sign-On System for the Web. The 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, Colorado, USA, 2015, 1358-1369.