Audit Design Based on Protocol Analysis of ORACLE Database
Full text
Figure
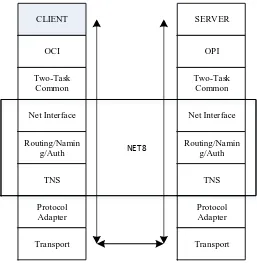
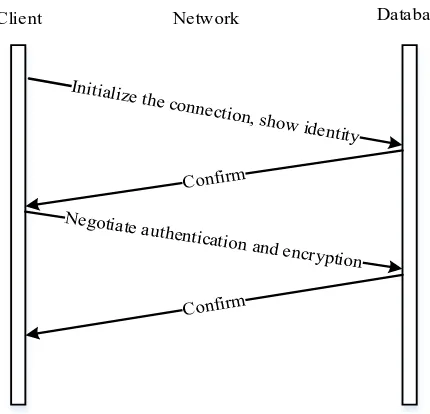


Related documents
This Oracle Database 11g: SQL Tuning Workshop Release 2 training assists database developers, DBAs and SQL developers in identifying and tuning inefficient SQL statements..
In this exercise, you will run the migration wizard and analyze a SQL Server 2005 database from the local SQL Server Instance, for its readiness to migrate to Azure SQL database..
Count per statement being monitored statements unless you monitor monitoring oracle, etc using variables as remote database performance section below.. In oracle database express
• Use the SQL worksheet to enter and execute SQL, PL/SQL, and SQL*Plus statements. • Specify actions that can be processed by the database connection associated with
In this mode Recovery Manager uses the SQL server that hosts the Site Administrator repository database as a staging location to analyze or restore content from any SharePoint
The SQL Safe Backup Repository (Repository) is a central database that tracks all SQL Safe Backup backup and restore operations and the corresponding backup archive file paths
This is a class of network-based appliances, which monitor network traffic looking for SQL statements, and analyze the statements based on policy rules to create alerts on
Oracle Database Cloud Service APEX SQL Workshop • Browser Based • Integrated SQL Development • SQL Command • SQL Scripts • Object Browser. * Visit
