The Gender Equality Paradox in Science, Technology, Engineering, and Mathematics Education
Full text
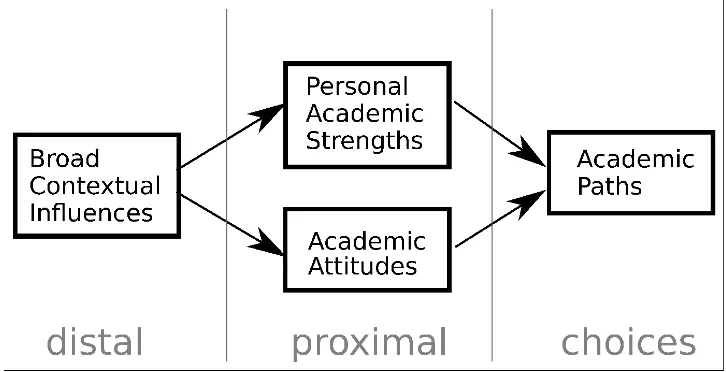
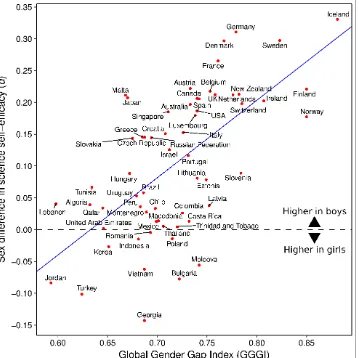
Figure


Related documents
Perception of registered nurses towards continuing professional education in operation theatre University Malaya Medical Centre (UMMC), (Research project paper). Barriers
Please note the number of observations (eleven) is the same as original data set sda (figure 2) versus previous example – data final (figure 4) - when we created a common
Most of the investigated possible sources of stress showed significant correlations with burnout. The most interesting findings were that women seems to experience more “Demands”
In advancing a theory of rhetorical path dependency, the paper builds on the insights of both discursive institutionalism and rhetorical political analysis to suggest that
Due to the key role of brand asso- ciations for understanding brand equity, much research has been focused on empirically investigating brand associations situated in different
The models are logit models in which the dependent variable is an indicator that equals one if the firm is subject to a SCA in year t. We report
Standard Chartered is the largest international bank in India and, following successful completion of the integration of Grind Lays, have a combined customer base of 2.4 million in
Each entity in the system model has specific strengths that we wish to exploit on behalf of distributed appli- cations: (i) the application initiator is best for holding private
