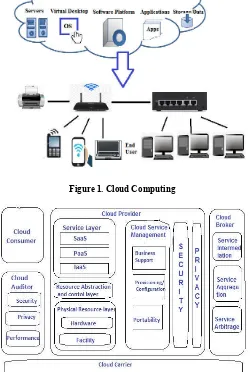
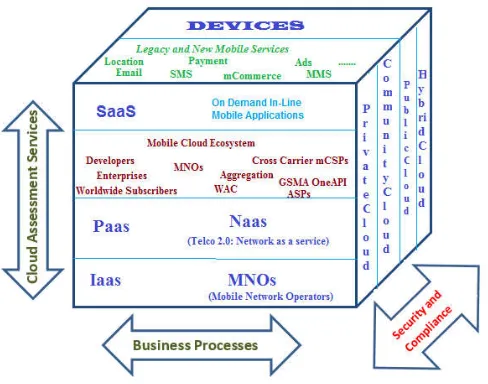
Cloud computing – architecture, features, security and privacy in cloud
Full text
Figure
Related documents
The area constitutes the largest continuous stretch of forest north of the Missouri River in the state and is sanctuary to a unique wildlife population that includes deer,
The inflow boundary condition for such LES simulations is set using the turbulence information extracted from the wind farm aerodynamics simulations performed in the first step..
The final design incorporated high levels of thermal efficiency using a clay block with external insulation to provide thermal mass, highly insulated roof
In the interview, students were asked about their educational goals; their experiences with searching for, evaluating, and using information; their experiences with IL instruction;
In fact, the WGS–based approaches (both the wgMLST and the bioinformatics script) already implemented in the National Reference Laboratory will be thereafter applied for the
Also both negative and positive perfectionism could significantly predict changes in self handicapping (p<0.001). Conclusion: In the presence of positive
Gill can act as an informative tissue for determining the effects of anoxia on energy metabolism proteins (Tomanek, 2008) and has already been used in numerous studies
AF — atrial fibrillation; AP — accessory pathway; ASD — atrial septal defect; CTI — cavotricuspid isthmus; MAP — multiple accessory pathway; NA — not available; O-AVRT