Revisiting Security Aspects of Internet of Things for Self Managed Devices
Full text
Figure
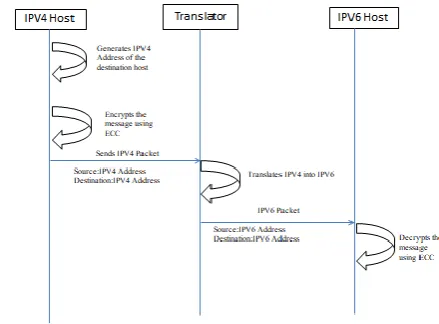
![Figure 3 System diagram aimed at communication started by IPv6 [8]](https://thumb-us.123doks.com/thumbv2/123dok_us/9304051.431534/3.595.59.276.134.297/figure-diagram-aimed-communication-started-ipv.webp)
![Table 1 : Evaluation of Key size [17]](https://thumb-us.123doks.com/thumbv2/123dok_us/9304051.431534/4.595.63.251.288.414/table-evaluation-key-size.webp)

Related documents
After the treatment phase is done with, both groups are assessed on the effect of the treatment (note taking strategies) on the reading comprehension as students
The most difficult question for the future of the Internet is not how the technology will change, but how the people will change with the progress of the
2012 The Southeastern Center for Contemporary Art, Winston-Salem, NC, Artist Talk 2011 The University of Houston, MFA Painting Program, Houston, TX,. Artist Talk and
É-U_USA [itinéraire_itinerary: Art Gallery of Ontario, Toronto (ON), Canada (2014)] [catalogue]. Wearing
CT5010 explores the development of enterprise information systems based on database technologies. The emphasis is on rapidly building information systems that are
It gives the bases of good practice in order to achieve maximum benefit in using steel, in terms of structural behaviour of steel frames, the building envelope, acoustic and
Temnothorax nylanderi (Förster, 1850) new and a second record of Stenamma debile (Förster, 1850) (Hymenoptera, Formicidae) in Norway.. TORSTEIN KVAMME & THOR
Although the original rationale for exempting the nonprofit hospital from federal income taxation was that it was organ- ized and operated exclusively for charitable