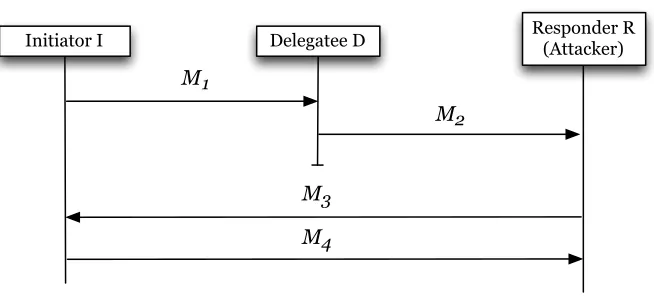
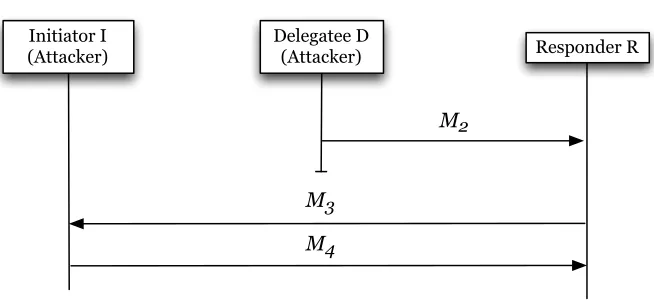
Attacks to a proxy-mediated key agreement protocol based on symmetric encryption
Full text
Figure
![Figure 1: Network architecture (adapted from [22])](https://thumb-us.123doks.com/thumbv2/123dok_us/7953243.1319783/5.612.184.412.92.282/figure-network-architecture-adapted-from.webp)


Related documents
In most cases, QL and QLQT show better reliabilities than non-redundant, TMR and TIR circuits. However, they also incur a larger area overhead than TMR and TIR. For
The present study revealed thinning of total retinal thickness, especially some of its layers including retinal nerve fiber layer, inner plexiform layer, and ganglion
Next, the average via- bilities of CyL/+ and Pm/+ heterozygotes carrying wild-type chromosomes of these various categories, but developing in cultures yielding
ATEC’s trademarked software and middleware, and in-house programming expertise, facilitate deep integration between disparate systems, which is a capability that contributed to ATEC
The DJ-195 does not require a serviceperson to manipulate the components on the printed-circuit board, except the trimmer when adjusting reference fre- quency and deviation.Most of
Figure 4.13: Development of NP concentration profile using heterogeneous blood flow modeling at high flow rate and low average hematocrit.. Zero concentration gradient assumed
CASE Application Management System (CAMS) is developed using some of these technologies (Google Web Toolkit and Java EE) to achieve the features of a modern web application..
1) At your telephone: Lift the handset, depress m and dial the desired intercom number. 2) If the called telephone does not answer: Depress them button to set